IAVM Enrichment
IAVM is a DoD process for identifying and managing security vulnerabilities in critical systems, ensuring timely protection through alerts, bulletins, and advisories.
Types of Assets Fetched
This adapter does not fetch any assets but enriches data on Aggregated Security Findings and Security Finding Instances, according to the principles of Information Assurance Vulnerability Management (IAVM).
Parameters
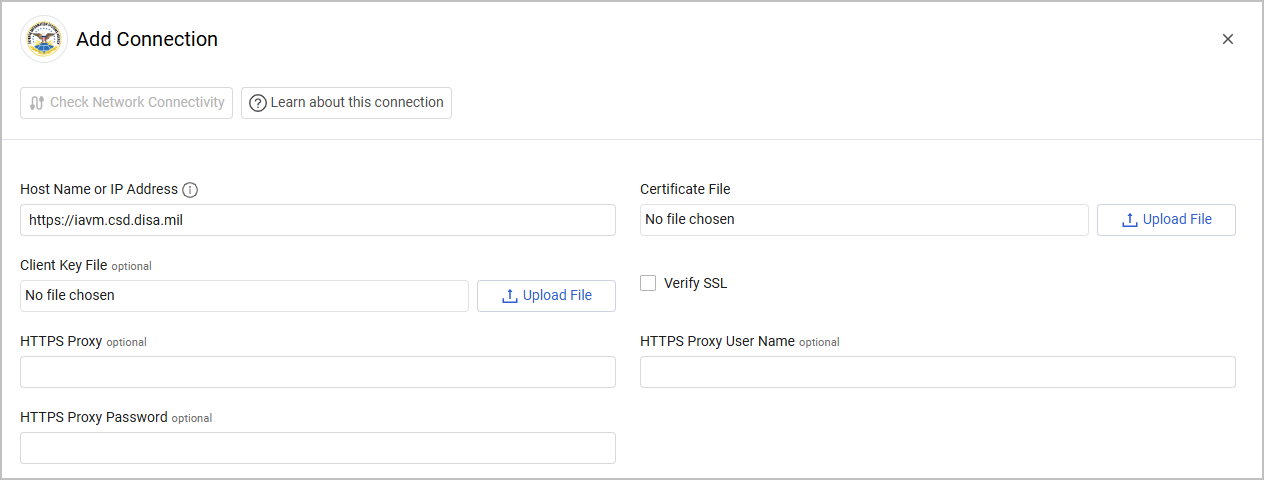
- Host Name or IP Address (required) - The hostname or IP address of the IAVM Enrichment server that Axonius can communicate with via the Required Ports.
- Certificate File (required) - A local certificate store in PEM format containing a certificate and key that has been provisioned into the system.
- Client Key File (optional) - Upload a client key file.
- Verify SSL - Select whether to verify the SSL certificate of the server against the CA database inside of Axonius. For more details, see SSL Trust & CA Settings.
- HTTPS Proxy (optional) - Connect the adapter to a proxy instead of directly connecting it to the domain.
- HTTPS Proxy User Name (optional) - The user name to use when connecting to the value supplied in Host Name or IP Address via the value supplied in HTTPS Proxy.
- HTTPS Proxy Password (optional) - The password to use when connecting to the server using the HTTPS Proxy.
To learn more about common adapter connection parameters and buttons, see Adding a New Adapter Connection.
Required Ports
Axonius must be able to communicate with the value supplied in Host Name or IP Address via the following ports:
- TCP port 443
Supported From Version
Supported from Axonius version 6.1
Updated 24 days ago
