Akamai Kona WAF
Akamai Kona Web Application Firewall (WAF) provides protection against web application attacks including SQL injections, cross-site scripting, and remote file inclusion.
The Akamai Kona WAF adapter provides Axonius with visibility into your publicly accessible assets, including domain, URL, and security configuration data.
Asset Types Fetched
- Devices
- Domains & URLs
- Network/Firewall Rules
Before You Begin
Required Ports
- TCP port 80/443
Authentication Methods
- Client Token/Client Secret
- Access Token
Required Permissions
The adapter connection requires an API user with permissions to retrieve firewall configurations, security files, and property manager data.
APIs
Axonius uses the Akamai Application Security API to retrieve asset data.
Supported from Version
This adapter is supported from Axonius version 4.6.
Connection Parameters
To connect the adapter in Axonius, provide the following parameters.
Required Parameters
-
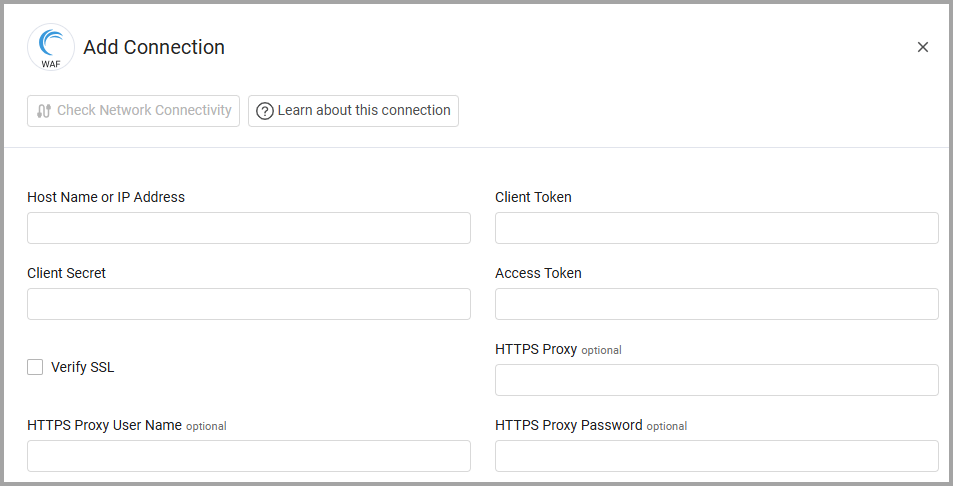
Host Name or IP Address - Enter the hostname or IP address of the Akamai Kona WAF server.
-
Client Token and Client Secret - Enter the credentials for a user account that has permissions to fetch assets.
-
Access Token - Enter an API key associated with a user account that has permissions to fetch assets.
Optional Parameters
-
Verify SSL - Select whether to verify the SSL certificate of the server against the CA database inside of Axonius. For more details, see SSL Trust & CA Settings.
-
HTTPS Proxy - Enter an HTTPS proxy address to connect the adapter to a proxy instead of directly connecting it to the domain.
-
HTTPS Proxy User Name - Enter the user name to use when connecting to the value supplied in Host Name or IP Address via the value supplied in HTTPS Proxy.
-
HTTPS Proxy Password - Enter the password to use when connecting to the server using the HTTPS Proxy.
To learn about additional optional/common adapter connection parameters, see Adding a New Adapter Connection.
Advanced Settings
Note
- Advanced settings can apply to either all connections of this adapter, or to a specific connection. For more detailed information, see Advanced Configuration for Adapters.
- For more general information about advanced settings, see Adapter Advanced Settings.
-
Fetch Firewall (default: false) - Select this option to fetch firewalls.
-
Fetch URLs (default: false) - Select this option to fetch URLs.
-
Fetch Dynamic IP Firewall & Network Lists (default: false) - Select this option to fetch dynamic IP firewall and network lists, using the following endpoints:
For this configuration to work properly, make sure that the “Fetch Firewall” configuration is also enabled.
-
Fetch Rules tree and hostnames list from Property Manager (default: false) - Select this option to create a URL entity, identify the Akamai property and version, list its hostnames, and retrieve the final edge URL and rule configuration.
-
Parse URL IPs (default: false) - Select this option to parse IPs for URL assets.
-
Parse Devices (default: true) – Select this option to parse assets as devices. For existing connections, this is enabled by default to preserve previous data modeling. For new connections, this is disabled by default, and assets are instead parsed as Domains & URLs.
-
Parse hostname as URL name - Select this option to parse the hostname as the URL name.
Updated 5 days ago
