Identities Dashboards
Our pre-built dashboards provide immediate value by offering readily available insights into your identity landscape. These dashboards serve as a starting point for exploring the platform's capabilities, demonstrating the potential for data analysis and informed decision-making. They showcase the power of Axonius Identities to transform raw data into actionable intelligence, enabling you to quickly identify and address identity-related risks and opportunities.
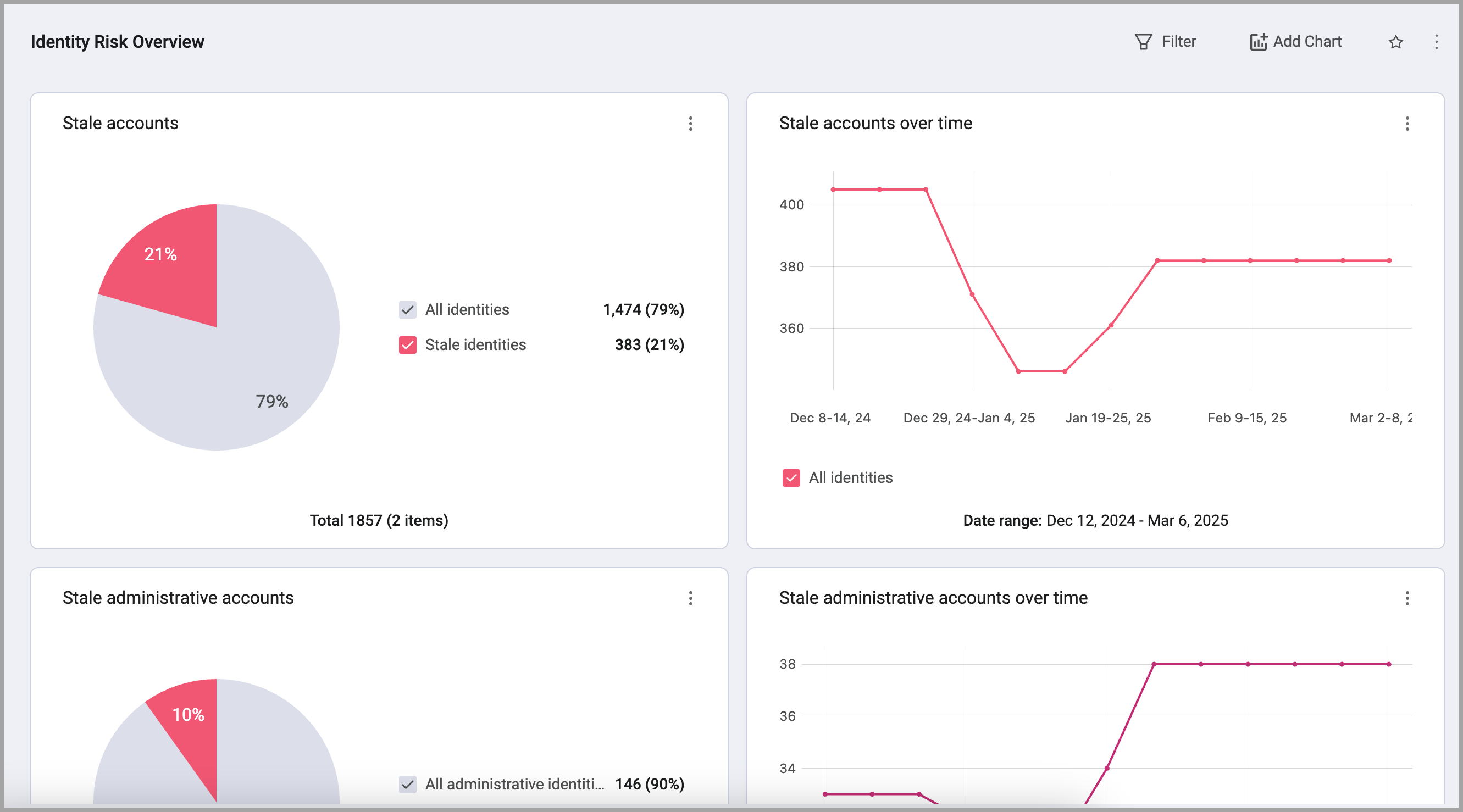
Identity Risk Overview
This dashboard provides a centralized view of critical identity-related security risks, enabling organizations to proactively address potential vulnerabilities and ensure compliance with security best practices. It highlights key areas such as password hygiene, MFA adoption, and excessive administrative access, empowering security teams to take proactive measures to mitigate risks and strengthen their overall identity security posture.
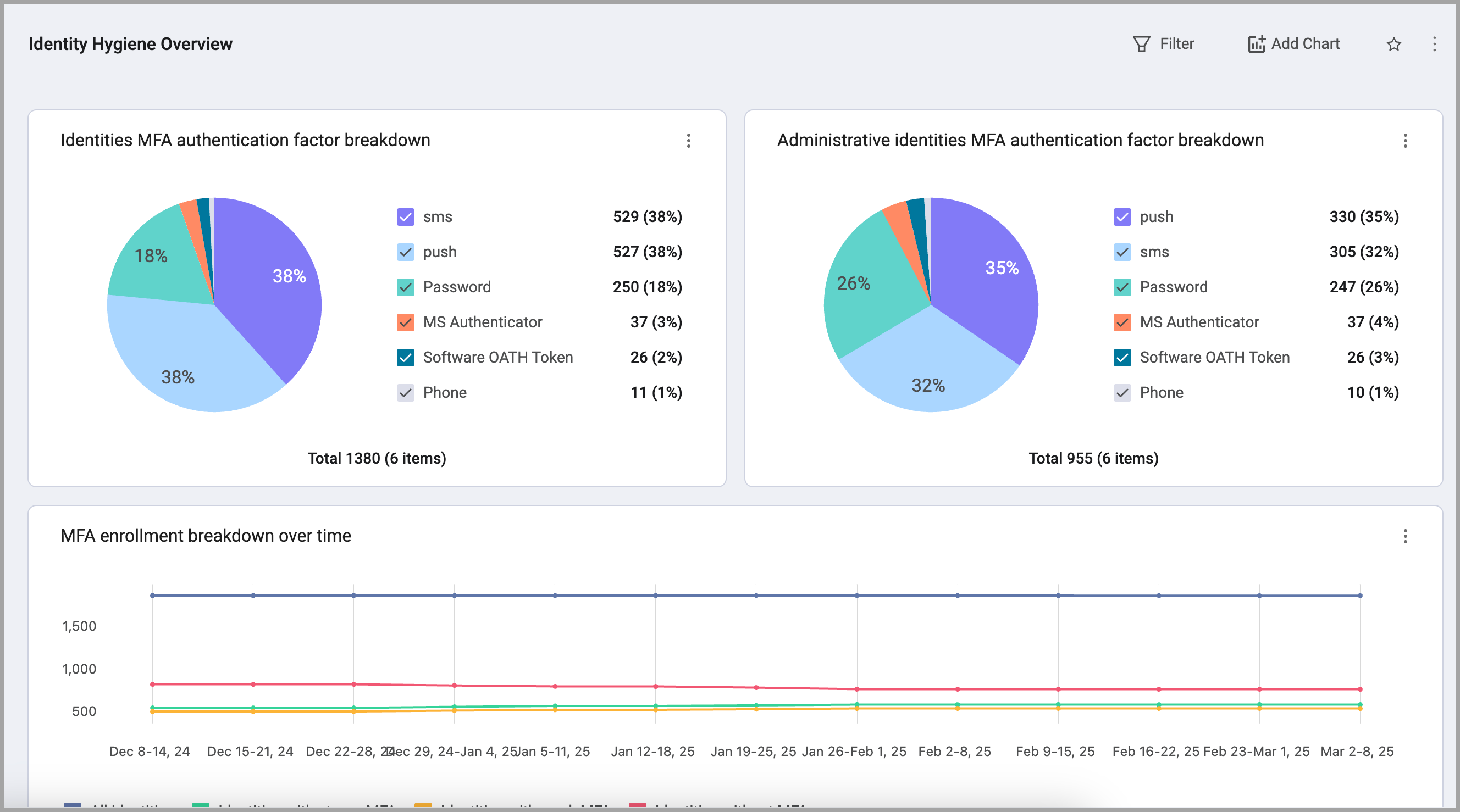
Identity Hygiene Overview
This dashboard provides a centralized view of identity-related drifts from best practices and tracks various identity projects and processes the organization implements to maintain the health and security of its identities.
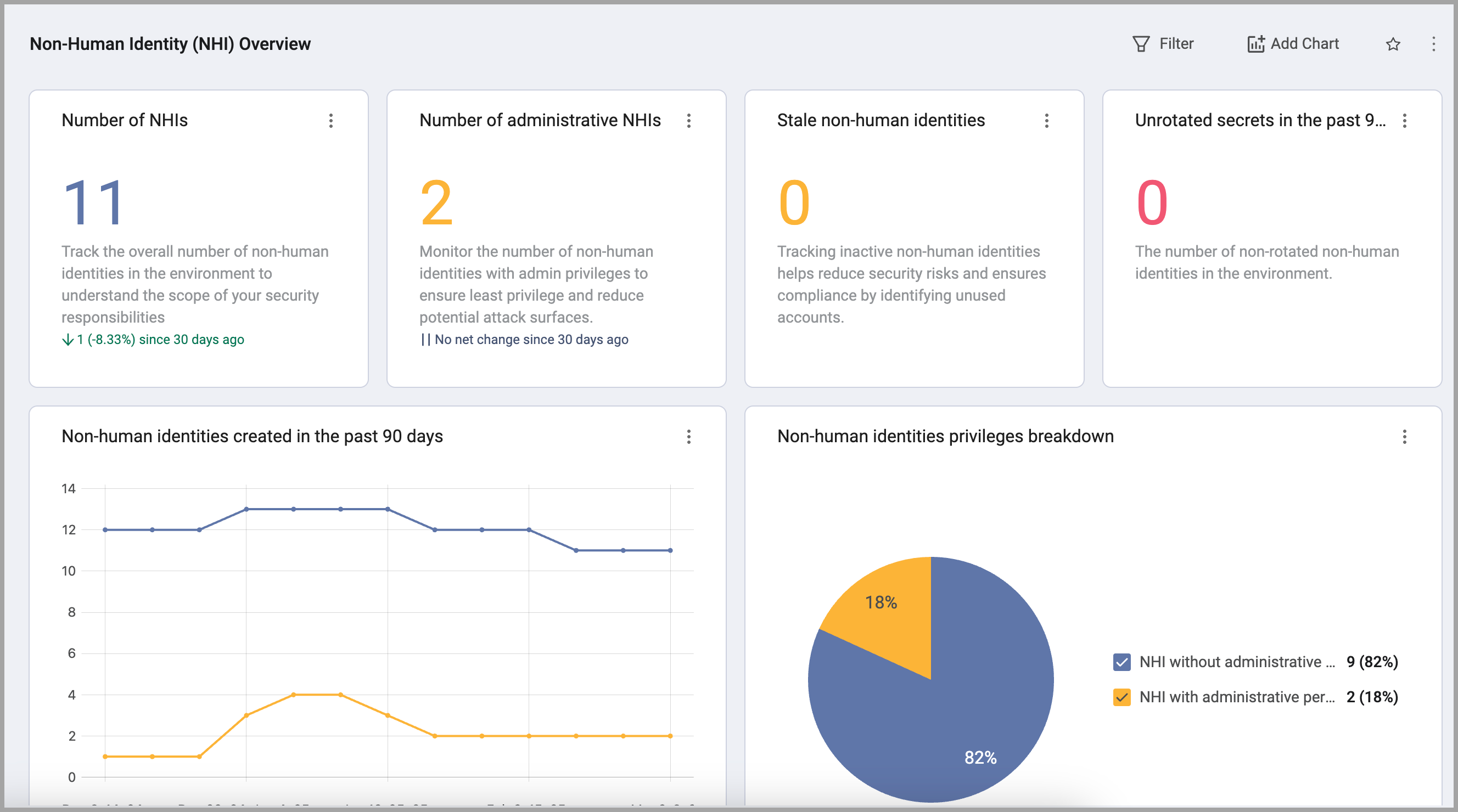
Non-Human Identity (NHI) Overview
This dashboard offers a comprehensive overview of non-human identities within your environment. It provides insights into the types, distribution, and potential risks associated with these identities, enabling you to manage and secure them effectively. A non-human identity includes but is not limited to, machines, applications, services, and other non-human entities that interact with systems or networks.
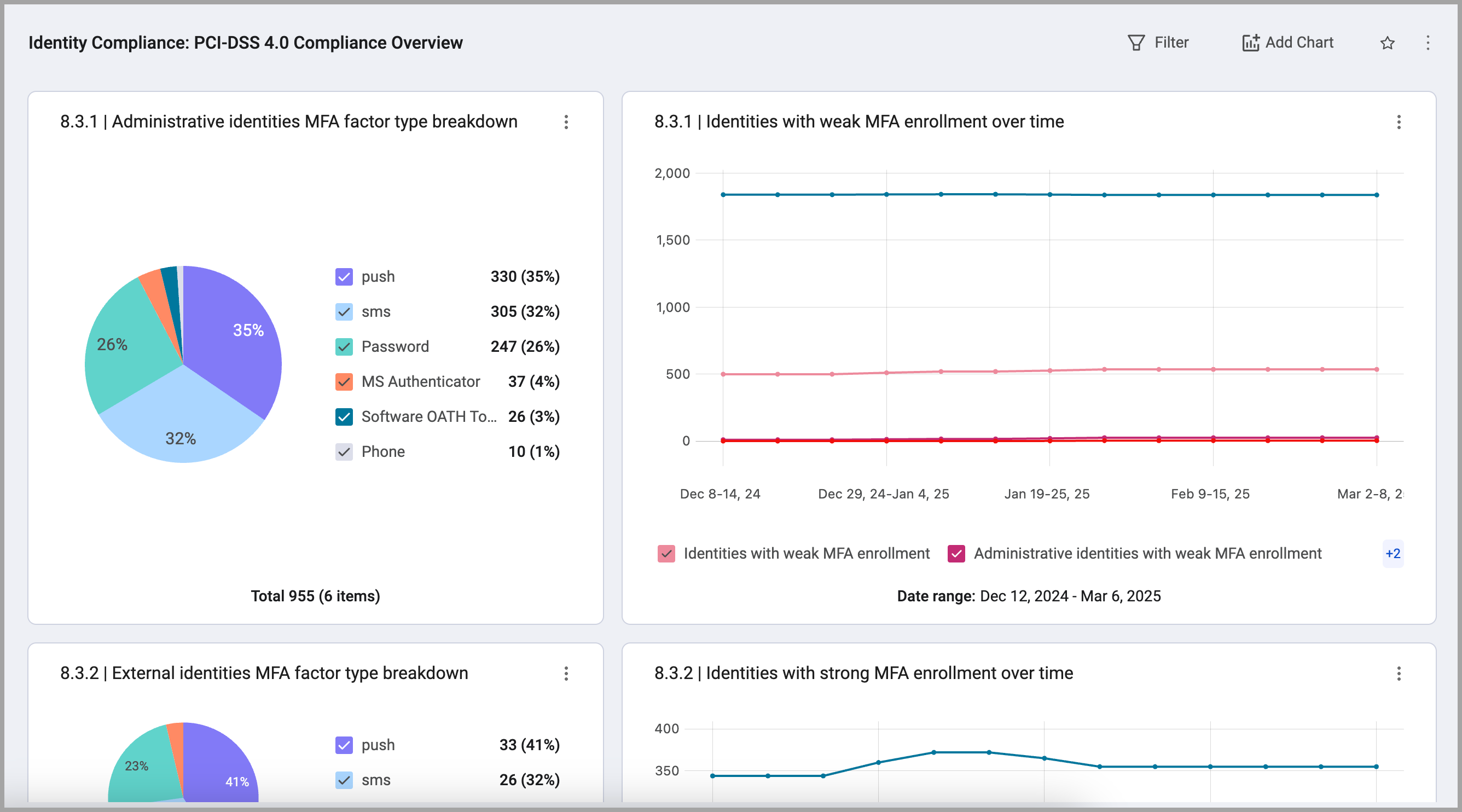
Identity Compliance: PCI-DSS 4.0 Compliance Overview
This dashboard details the adherence to the Payment Card Industry Data Security Standard (PCI-DSS) version 4.0, specifically focusing on requirements related to identities and users. It covers areas such as access control, authentication, authorization, and user management practices, demonstrating the commitment to safeguarding sensitive cardholder data through robust identity and access management controls.
Identity Compliance: NIST 800-53 Rev5 Overview
This dashboard visualizes key controls from NIST 800-53, a framework for managing IT security services throughout their lifecycle. By monitoring these controls, you can ensure effective identity and access management (IAM), mitigating risks and strengthening your organization's security posture. The dashboard provides insights into essential IAM aspects, including authentication, authorization, and account management, aligning with NIST 800-53's guidance for secure service operation.
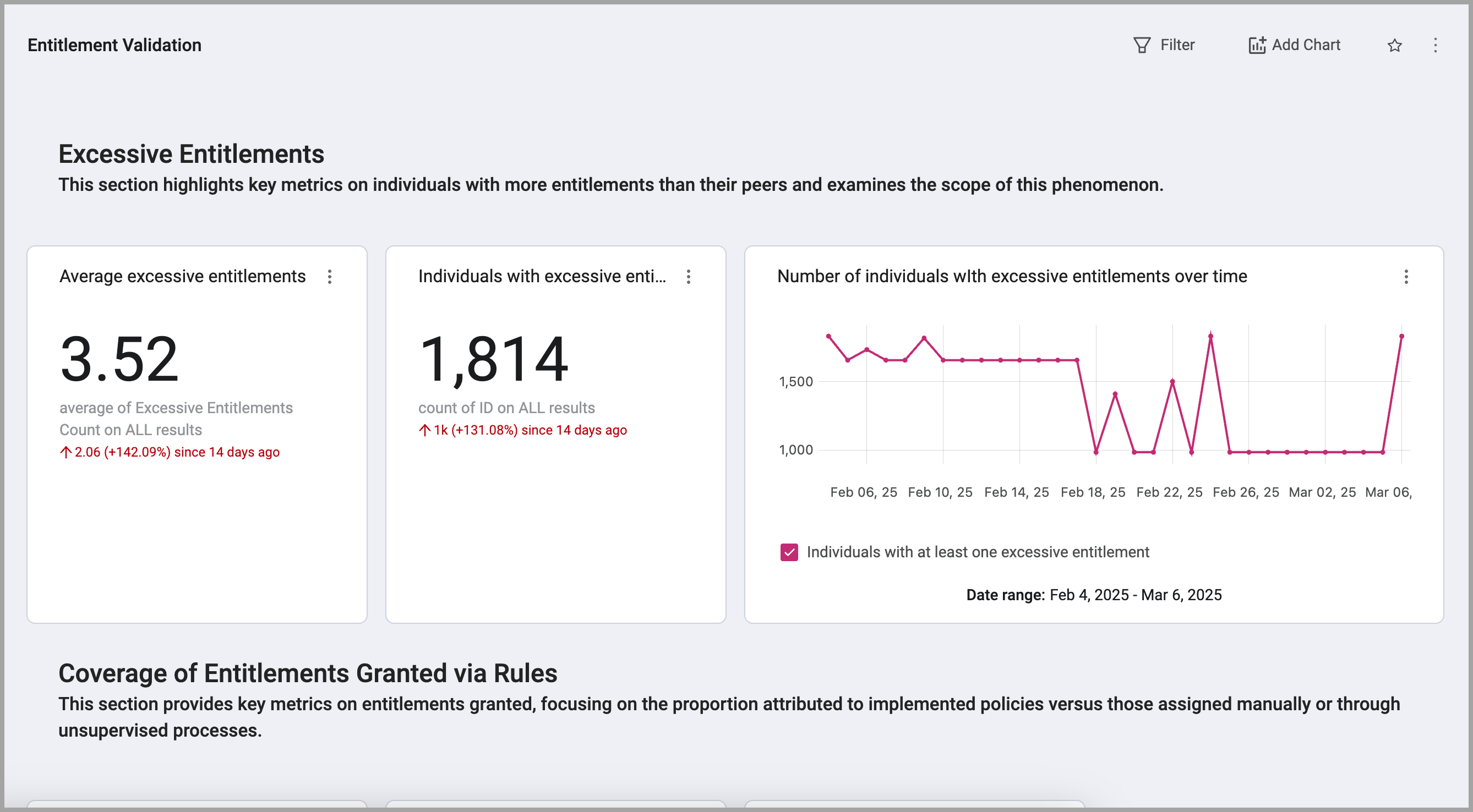
Entitlement Validation
This dashboard provides a comprehensive overview of entitlement validation processes and results. It offers insights into the effectiveness of entitlement reviews, identifies potential risks associated with unvalidated or excessive entitlements, and supports informed decision-making to optimize access control and security posture.
Updated about 2 months ago
