External Exposures Workspace
The Challenge
Organizations often struggle to gain a clear understanding of which system components are exposed to the public internet. Determining this may require writing complex queries and reviewing large tables of raw data, which are often cluttered, difficult to interpret, and time-consuming.
Our Solution
External Exposures provides a clear, intuitive view of which system components are connected to or isolated from the public internet. This view maximizes visibility and reduces noise from raw data, which empowers security and IT teams to:
- Identify publicly exposed assets, which might include critical assets and crown jewels
- Track changes and security trends over time
- Prioritize remediation efforts based on data-driven decisions
- Communicate network exposure confidently to leadership
- Take faster, more informed actions to reduce the overall organizational attack surface
Before You Begin
Products Required for this Workspace
To access and use this workspace, you must have access to Axonius Exposures.
Additional Configuration
To ensure that the workspace correctly identifies public-facing elements, configure all networks outside the RFC 1918 address space as internal networks when appropriate. This configuration helps the logic of mapping Network Routes distinguish between truly public and internal routes, and reduce false positives when handling public IP addresses that should be treated as internal. For more information, see Configuring Network Settings
Workspace Assets and Modules
Note
Each workspace has its own use-case-focused navigation menu on the left. The assets and modules available from this menu depend upon your access configuration.
You can access the following assets directly from this workspace:
Use Cases this Workspace Helps You Fulfill
The External Exposures' Home page displays charts and KPIs of special interest, divided into functional areas that help you focus on specific use-case information.
The data displayed on the charts relies mainly on the Risk Score settings you have defined for your assets. If needed, you can always change those settings to get the most accurate risk picture.
General Internet Exposure Picture
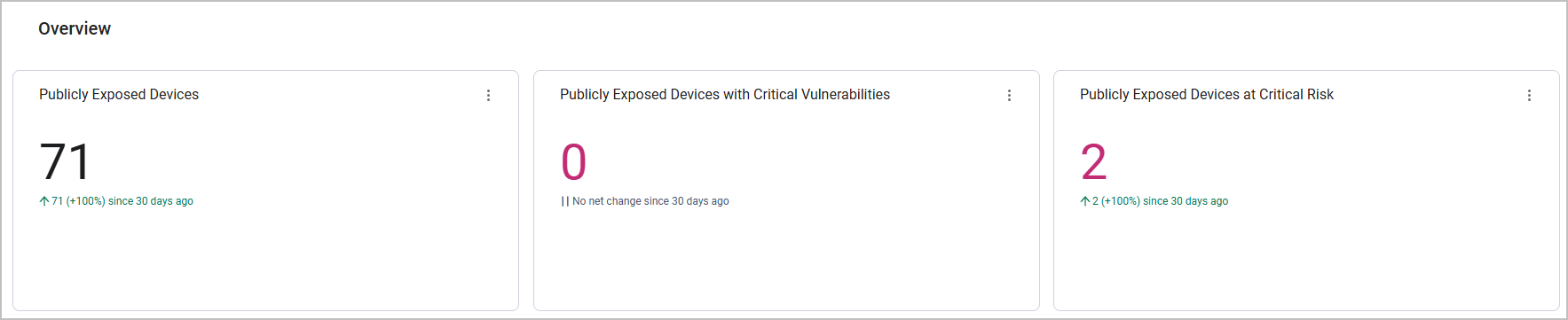
The Overview section at the top of the page provides a simple, straightforward view of your most critical assets that are exposed to the public internet. It shows data the following data:
- The total number of publicly exposed devices
- The total number of publicly exposed devices with Critical vulnerabilities, which represent the ultimate attack path.
- The total number of publicly exposed devices that are at Critical Risk Level. This number is determined by the Axonius Risk Levels you defined. Mapping Risk Levels to exposure levels helps you device which assets demand immediate attention to enhance security posture.
Recognizing Exposure Components in Context
The workspace shows you publicly exposed devices broken down by different criteria: by Operating System and by Risk Score. These different displays help you zoom in on specific connections between asset components and risks.
For example, the Publicly-Exposed Devices by Operating System chart might reveal operating systems exposed to the internet that shouldn't be exposed at all.
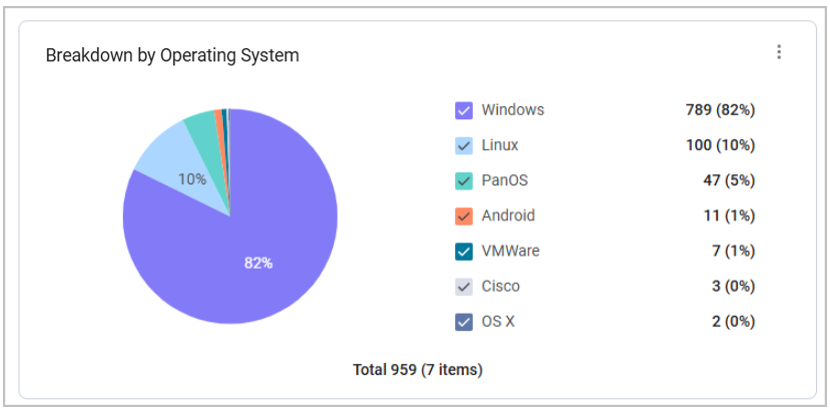
Click on the colored portion of an operating system in the chart to open the Devices page with the appropriate filters. For example, show only publicly exposed devices with a Windows operating system:
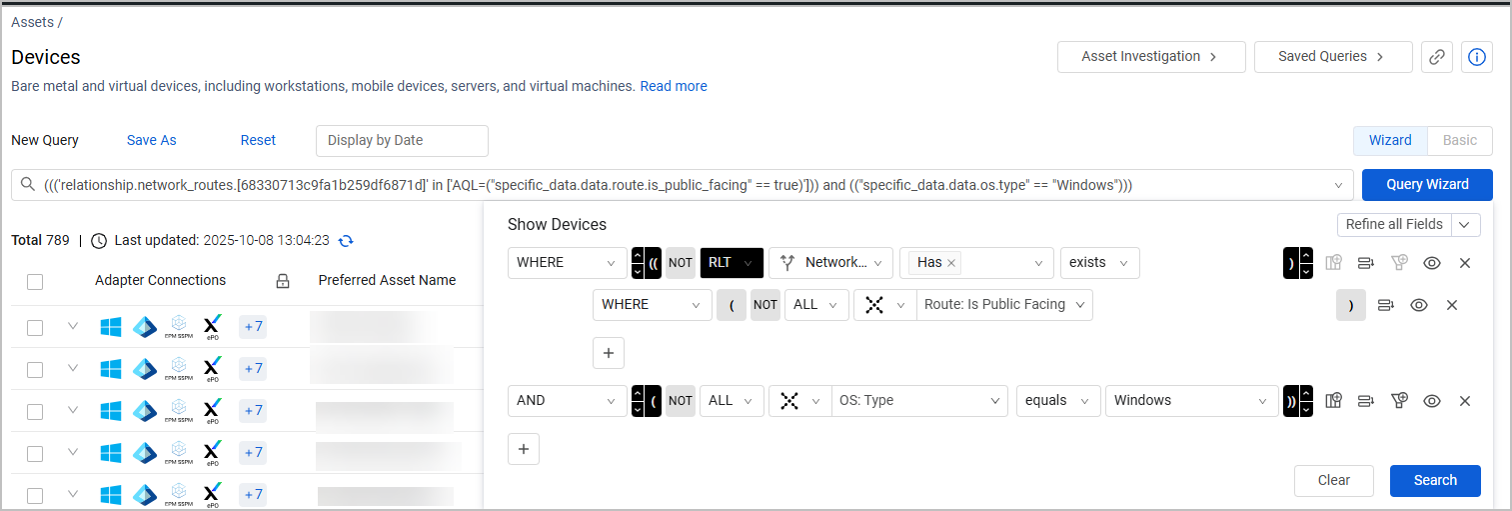
From the Devices page, you can explore a specific device on its Asset Profile page; or implement remediation workflows such as opening tickets and cases for selected devices.
Click the data in any chart in the workspace to take the same actions and additional actions from the Assets page that it opens.
The workspace also provides information on the potential network distribution components at risk, as well as potential entry points in the network route that attackers might exploit. The following data is available:
- Publicly exposed devices with no firewall protection
- Publicly exposed Load Balancers
- Publicly exposed Load Balancers with no firewall protection, which provide attackers with a direct path to multiple backend systems
Tracking Exposure Trends Over Time
The workspace shows charts that detail how many publicly exposed devices exist in your environment over a certain period of time - both general devices and devices at critical risk. This data help you outline a long-term security plan and make changes to it over time according to your needs.
Clear View of Publicly Exposed Assets
The workspace displays comprehensive lists (Assets tables) of publicly exposed Device and Network Route assets. Each table contains key information on each asset. Click View all Results to open the relevant Assets page in a new tab.
Updated 7 days ago
