Unisys Stealth
Unisys Stealth transforms existing networks—both on-premises and in the cloud—into a Zero Trust Network through identity-based microsegmentation.
Types of Assets Fetched
This adapter fetches the following types of assets:
- Devices
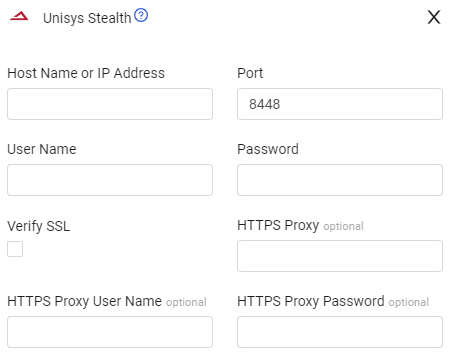
Parameters
-
Host Name or IP Address (required) - The hostname or IP address of the Unisys Stealth server.
-
Port (required, default: 8448) - The port used for the connection.
-
User Name and Password (required) - The credentials for a user account that has the permissions to fetch assets.
-
Verify SSL - Select whether to verify the SSL certificate of the server against the CA database inside of Axonius. For more details, see SSL Trust & CA Settings.
-
HTTPS Proxy (optional) - Connect the adapter to a proxy instead of directly connecting it to the domain.
-
HTTPS Proxy User Name (optional) - The user name to use when connecting to the value supplied in Host Name or IP Address via the value supplied in HTTPS Proxy.
-
HTTPS Proxy Password (optional) - The password to use when connecting to the server using the HTTPS Proxy.
-
To learn more about common adapter connection parameters and buttons, see Adding a New Adapter Connection.
APIs
Axonius uses the Unisys Stealth Ecosystem API v4.0.134.0
The API should be local with a default port of 8448. For example: https://localhost:8448
Version Matrix
This adapter was only tested with the versions marked as supported, but may work with other versions. Contact Axonius Support if you have a version that is not listed, which is not functioning as expected.
| Version | Supported | Notes |
|---|---|---|
| v1 | Yes | -- |
Supported From Version
Supported from Axonius version 4.7
Updated 5 months ago
