Incident Response
Accelerate Incident Response
Introduction
Incident Response is an organization’s processes and associated technologies for detecting and responding to cyberthreats, security breaches, or cyberattacks. A formal incident response plan using Axonius enables IR teams to get a broader view of the threat being addressed and the ability to dive deeper into individual assets that have been impacted.
Audience: SOC, Incident Response Team
Difficulty: Intermediate to Advanced
Execution Time: 1 week, ongoing refinement
Duration of Use Case: Perpetual
Value: Helps organizations streamline investigations, minimize the impact of a breach, and maintain business continuity.
What is this use case?
Every organization needs an Incident Response plan so there is no time wasted gathering data for analysis, and the impact of the incident is minimized. Axonius can provide the IR teams with information from security tool coverage (confirming what systems may be at heightened risk), user activity, and other data points of interest (like what devices have encryption enabled).
Use Case in Action:
Axonius has templates for both Device and User Incident Response, and they are a great start in developing a comprehensive collection of IR dashboards and charts:
- Endpoint Protection (EPP, XDE, EDR)
- VA Tools
- IAM
Why is it Relevant?
The key to Incident Response is responding to an incident as quickly and efficiently as possible. Finding pertinent information regarding a Device or User improves the chances of containing the incident and promptly remediating it before any further harm is done. Working with the IR team to develop charts and dashboards will help to achieve this goal.
Visibility
How do I visually explain this use case?
For Incident Response, the Asset Profile Dashboard allows you to create investigative dashboards focused on a specific asset of any given asset type. Additionally, the Asset Graph helps you explore relationships between assets. Together, these tools provide a visual foundation for conducting the research necessary for detection, containment, investigation, remediation, and recovery.
Recommended Visualizations
Below are some visualizations that give us pertinent information regarding the asset being investigated quickly and efficiently by creating an IR dashboard within Dashboard Overview.
- Device Users – Who was last on this device? Are they associated with any other devices?
- OS Status – What OS, version, EOS, EOL?
- IR Team Data – Data points the IR team wants to quickly see
Asset Investigation
View changes over a period of time through the use of Asset Investigation. This view can either be accessed for a single Asset, via its profile page, or for all assets through Asset Investigation on the side menu.
- What ports are open and when were they discovered?
- When were new users first seen on the device?
- Were any applications recently installed or updated?
Asset Graph
Explore the asset's relationship to all other Asset types known to Axonius.
Further expand your search to identify associated Users and Devices that may need to be investigated.
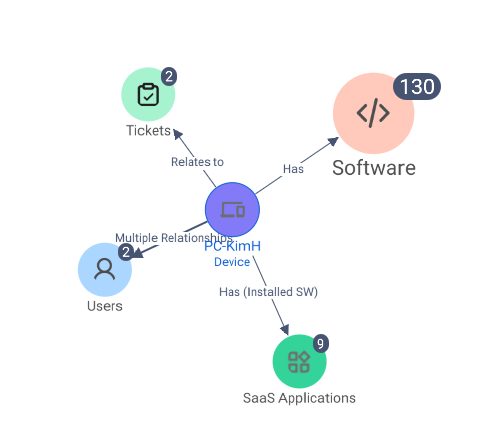
The graphics can be used as part of an incident postmortem. View the asset profile from within the Asset Graph.
Actionability
How do I automate this use case?
Execute Enforcement Center Actions to automate different tasks in response to the incident. Automations can be configured in advance and used on demand.
Updated 5 months ago
