Have I Been Pwned
Have I Been Pwned is a website to check whether email accounts have been compromised in a data breach.
The Enrich User Data by Have I Been Pwned (HIBP) adapter uses the HIBP API to provide information on breaches, pastes and pwned password identified by the 'Have I Been Pwned' (HIBP) website for a given email account.
Note
For details on the breaches, pastes and pwned password identified by 'Have I Been Pwned' (HIBP) API, see HIBP API.
Types of Assets Fetched
This adapter fetches the following types of assets:
- Users
Parameters
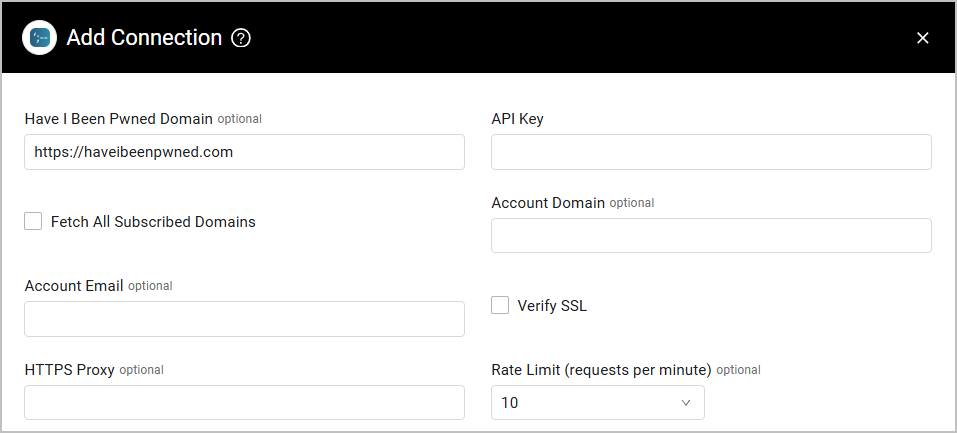
- Have I Been Pwned Domain - Specify the Have I Been Pwned (HIBP) domain or use the default configured HIBP public domain. This allows you to use the domain of a proxy instead of connecting directly to the server using the default domain of https://haveibeenpwned.com.
Note
The Domain field doesn't support multiple values. If you want to use multiple domains, you need to configure a separate adapter connection for each domain.
- API Key - Use the API key you purchased from 'Have I Been Pwned'.
- Fetch All Subscribed Domains - Select this option to fetch all subscribed domains under the API key.
- Account Domain (optional) - Specify the account domain.
Note
When Account Email is not supplied, Account Domain is required.
- Account Email (optional) - Specify a specific email account (e.g. [email protected]).
Note
When Account Domain is not supplied, Account Email is required. To run the HIBP query against multiple Account Emails, you must use the Enrich User Data with Have I Been Pwned Enforcement Center action.
- Verify SSL - Choose whether to verify the SSL certificate of the server against the CA database inside of Axonius. For more details, see SSL Trust & CA Settings.
- HTTPS Proxy (optional) - Connect the adapter to a proxy instead of directly connecting it to the domain.
- Rate Limit (requests per minute) (optional, default: 10) - Use this field to handle rate limit issues by HIBP documentation. It is possible to buy an account with a better rate limit.
To learn more about common adapter connection parameters and buttons, see Adding a New Adapter Connection.
Note
When configuring this adapter, set the value of 'Wait for a connection to the source for up to X seconds' on the Adapter Configuration Advanced Settings to at least 900.
Advanced Settings
Note
Advanced settings can either apply to all connections for this adapter, or to a specific connection. Refer to Advanced Configuration for Adapters.
- Fetch stealer logs - Select this option to enrich users with stealer logs.
Note
To learn more about Adapter Configuration tab advanced settings, see Adapter Advanced Settings.
Updated 5 months ago
