Lookout Mobile Endpoint Security
Lookout Mobile Endpoint Security is a mobile security solution that provides comprehensive risk management across iOS and Android devices to secure against app, device, and network-based threats while providing visibility and control over data leakage.
Types of Assets Fetched
This adapter fetches the following types of assets:
- Devices
- Aggregated Security Findings
- SaaS Applications
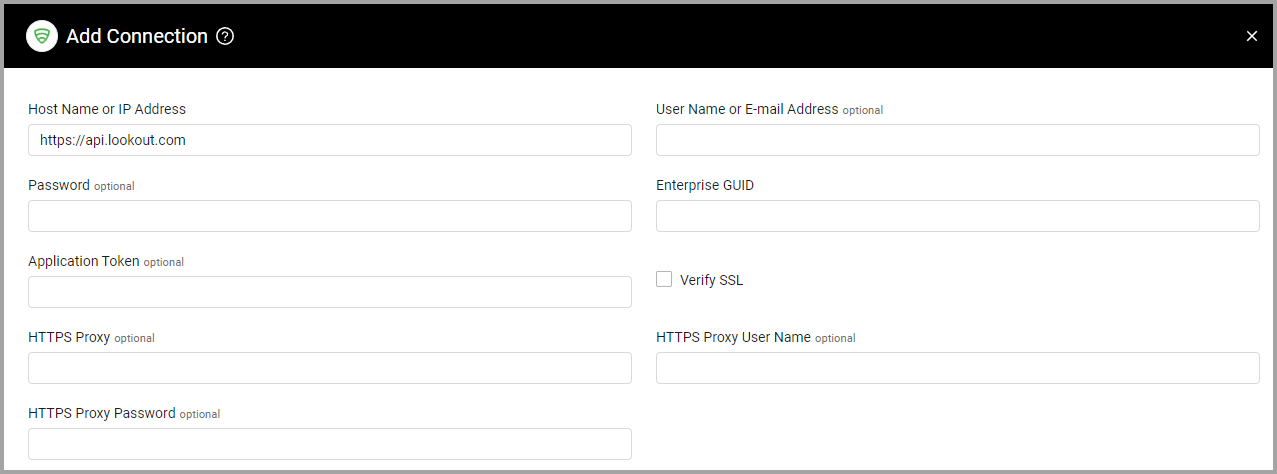
Parameters
- Host Name or IP Address (required, default:
https://api.lookout.com/) - The hostname or IP address of the Lookout Mobile Endpoint Security server. - User Name or E-mail Address and Password (optional) - The credentials for a user account that has the permissions to fetch assets. This can be a read-only access account.
Note
When Application Token is not supplied, User Name or E-mail Address and Password are required.
- Enterprise GUID (required) - The globally unique identifier associated with a user account that has permissions to fetch assets. Obtain the GUID from Lookout.
- Application Token (optional) - Specify the application token to fetch the threat data.
Note
When User Name or E-mail Address and Password are not supplied, Application Token is required.
To generate the application token:
- Log in to the Lookout MES Console as an administrator.
- In the left navigation bar, navigate to System
>Application Keys. - Click Generate Key in the upper-right.
- Specify a label name, then click Next.
- Copy the generated key clicking Click to Copy Application Key to Clipboard.
- Copy the key from the clipboard into the adapter Application Token parameter.
Note
Copy the generated key immediately to the Axonius adapter, as you cannot access the key again.
-
Verify SSL - Select whether to verify the SSL certificate of the server against the CA database inside of Axonius. For more details, see SSL Trust & CA Settings.
-
HTTPS Proxy (optional) - Connect the adapter to a proxy instead of directly connecting it to the domain.
-
HTTPS Proxy User Name (optional) - The user name to use when connecting to the value supplied in Host Name or IP Address via the value supplied in HTTPS Proxy.
-
HTTPS Proxy Password (optional) - The password to use when connecting to the server using the HTTPS Proxy.
To learn more about common adapter connection parameters and buttons, see Adding a New Adapter Connection.
Advanced Settings
Note
Advanced settings can either apply for all connections for this adapter, or you can set different advanced settings and/or different scheduling for a specific connection, refer to Advanced Configuration for Adapters
- Threat data time limit in hours (optional, default: 720) - Specify the threat data time limit in hours. The maximum value is 8760 hours (a year). The default is 720 (a month).
- Use API V2 - Select this option to use the version 2 of the API, which uses only the API key (without a username or password).
- Fetch Vulnerabilities from API V2 - Select this option to fetch vulnerabilities from
/mra/api/v2/os-vulns/androidand/mra/api/v2/os-vulns/iosand add them to devices with the same OS version.
Note
To learn more about Adapter Configuration tab advanced settings, see Adapter Advanced Settings.
APIs
Axonius uses the Lookout API.
Required Permissions
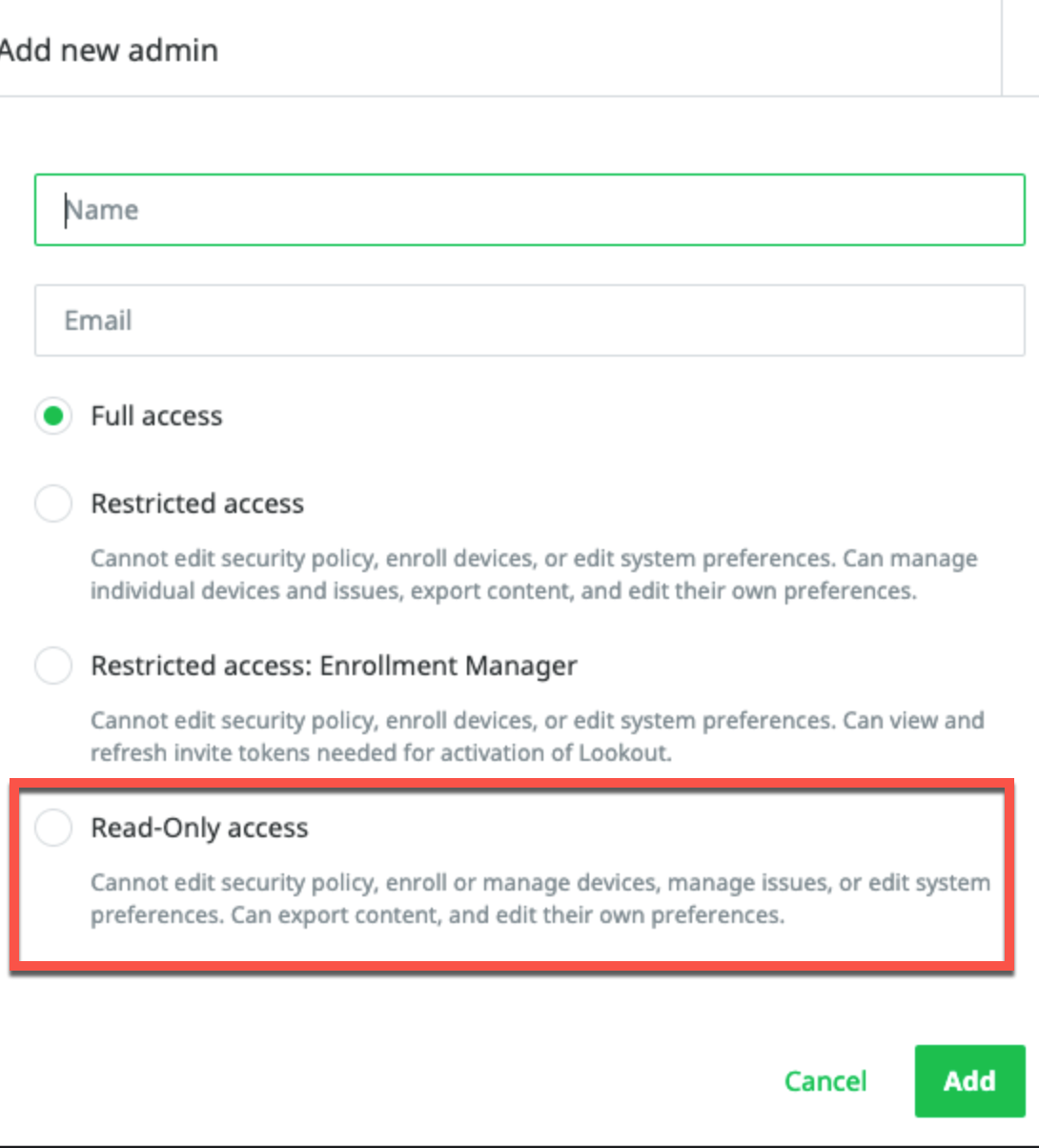
The value supplied in User Name must have permissions to fetch assets. You can use a local account with Read-Only access as long as it is identity-managed by Lookout and not by an external services provider.
Updated about 1 month ago
