Zscaler Web Security
Zscaler Web Security is a secure Internet and web gateway service that stops malware, advanced threats, phishing, browser exploits, malicious URLs, botnets, and more.
This adapter is compatible with Zscaler Internet Access (ZIA).
Asset Types Fetched
This adapter fetches the following types of assets:
- Devices, Users, SaaS Applications, Network/Firewall Rules
Before You Begin
Authentication Methods
You can authenticate this adapter using either of the following methods:
- API Key
- OAuth 2.0 authentication (ZIdentity)
Note
This adapter won't be able to fetch Devices when using OAuth 2.0 authentication.
See Connecting the Adapter in Axonius for the connection parameters required for each authentication.
Required Permissions - Latest Zscaler Version
If you're using Zscaler's latest version:
-
In Zscaler, under the Edit Administrator Role section, select the Administration Controls tab.
-
Configure the permissions listed in this image:
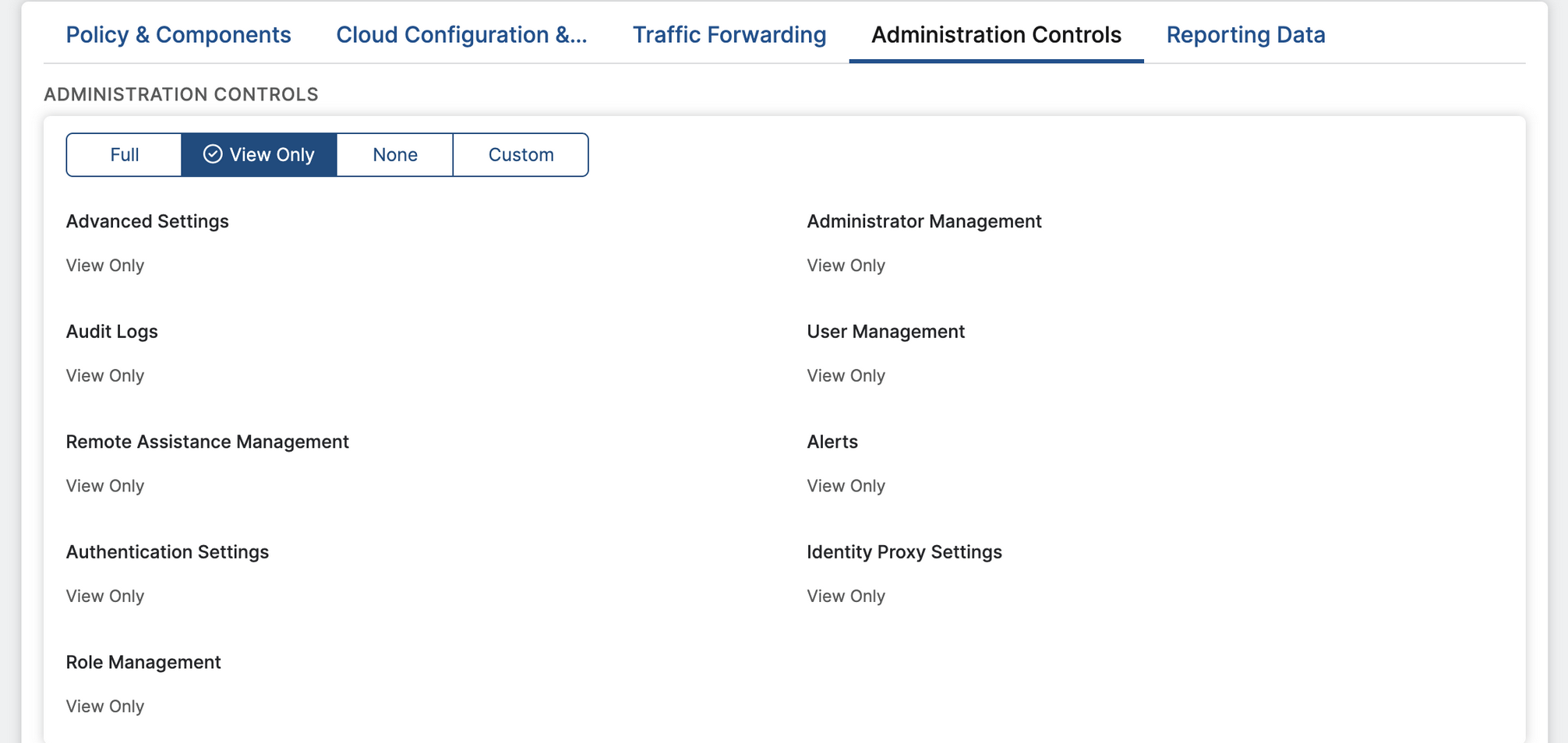
To fetch Devices:
To be able to fetch Devices, select the Traffic Forwarding tab and add the permissions listed in this image:
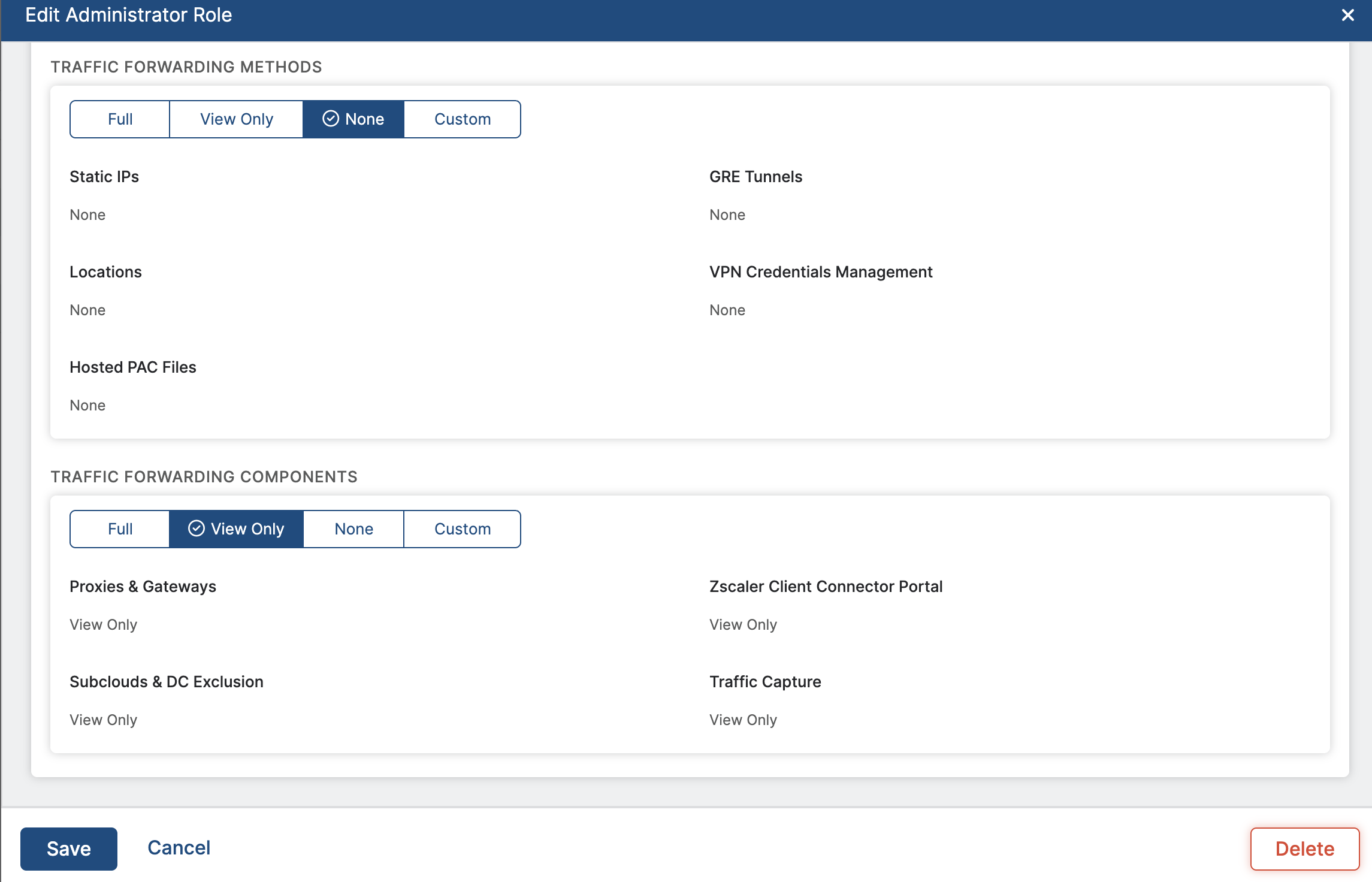
Required Permissions - Legacy Zscaler Version
If you're using an older version of Zscaler:
In Zscaler, under the Edit Administrator Role section, enable the following permissions:
- Access Control
- Policy and resource management
- Zscaler Client Connector Portal
- Traffic Forwarding
- Zscaler Client Connector Devices
- Authentication Configuration
- User Management
- Administrator's Access
- View Only
- Dashboard Access
- View Only
- Policy Access
- View Only
- Reporting Access
- View Only
Note
The value that you have in the Zscaler Domain parameter must be open in the firewall.
Setting Up ZScaler Web Security to Work with Axonius
To authorize using the API Key, you need to do the following:
Create a Local Admin Account
- Log into ZScaler Admin Portal
- Navigate to Administration > Role Management > Administrator Management
- Create a new local administrator (not SAML/SSO-linked)
- Set a strong password
- This account must be local, not federated through SAML/SSO
Assign the Role With the Required Permissions
- Navigate to Administration > Role Management > Roles
- Create or select a role with these permissions in the Administration Controls tab:
- Auditor Logs: Read-only
- Users: Read-only
- Client Connector Portal: Read-only
Retrieve the API Key
- Navigate to Administration > API Key Management.
- Copy the existing API key, or generate a new one.
- Store securely - this is needed for the adapter connection.
Connecting the Adapter in Axonius
Required Parameters - General
-
Zscaler Domain (default: admin.zscalerthree.net) - Specify the Zscaler cloud name that was provisioned for your organization. For example:
- admin.zscalerbeta.net
- admin.zscalerone.net
- admin.zscalertwo.net
- admin.zscaler.net
- admin.zscloud.net
- admin.zscalerdomain.net
- mobileadmin.zscalerdomain.net
- mobile.zscalerdomain.net
For more details, see 'Retrieve your base URI and API key' section under Zscaler API - Getting Started.
Note
Your organization may use a Zscaler domain for Single Sign On (SSO) that is different from the Base URL. This domain may need to be accounted for in firewall rule configurations to allow for a successful connection.
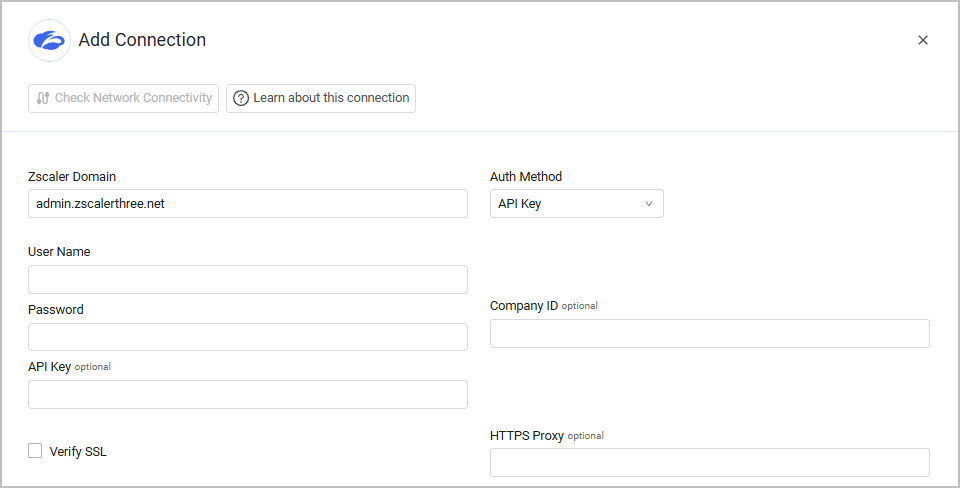
- Auth Method - Select either API Key (default) or ZIdentity.
- User Name and Password - The user name and password used to connect to Zscaler Web Security.
- API Key - Your organization's API key. The API key is mandatory to fetch user data from Zscaler. For more details about adding a new API key, see Zscaler documentation - About API Key Management.
Optional Parameters
- Company ID - Enter the Company ID. This parameter is required if the Fetch Zscaler Client Connector enrolled devicesadvanced setting is selected.
- Verify SSL - Select to verify the SSL certificate offered by the value supplied in Zscaler Domain. For more details, see SSL Trust & CA Settings.
- HTTPS Proxy - A proxy to use when connecting to the value supplied in Zscaler Domain.
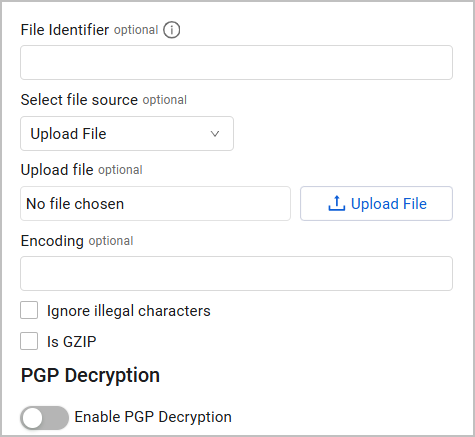
Optional File Upload
When fetching SaaS Application, you have the option to fetch these applications based on logs listed in a remote location. To do so, select the File Source from the Upload File dropdown and provide the relevant parameters. For more information, see connection parameters for the Custom Files adapter and the list of available file sources.
Note
To fetch logs from a remote location, you must enable the Enable real-time asset updates (Zscaler Nanolog Streaming Service) advanced setting.
To learn more about common adapter connection parameters and buttons, see Adding a New Adapter Connection.
Advanced Settings
Note
Advanced settings can either apply to all connections for this adapter, or to a specific connection. Refer to Advanced Configuration for Adapters.
Selecting Asset Types
In Advanced Settings, at the top of the Advanced Configuration, you can choose asset types that are relevant to specific advanced configurations.
- From the dropdown, select one or more asset types.
- The relevant advanced configurations are displayed.
- Next to certain configurations, you can find a small
.png) icon. Hover over the icon to see more information.
icon. Hover over the icon to see more information. - The Advanced Configuration page is divided into sections, which can be collapsed to make it easier to navigate.
Data Enrichment
- Fetch users (default: true) - Select this option to fetch users data. Each user is added as a user asset in Axonius.
- Enrich devices service status - Select this option to enrich device information with Service Status data.
- Add last used users information for duplicated devices (if "Avoid hostnames duplications" is enabled) - Select this option to add the last used users information for duplicated devices. This is applicable only when “Avoid hostnames duplications” is used.
- Add Device Manufacturer Serial for Zscaler devices - Select this option to extract the device manufacturer serial number from the UDID and add it to the device.
- Discover Application Users (default: true) - By default this adapter fetches SaaS application users. Clear this option to not fetch SaaS application users.
Fetch and Parse
- Ignore duplicated MAC addresses - Select this option to ignore MAC addresses that are associated with more than one device fetched from Zscaler.
- Avoid hostnames duplications - Select this option to avoid returning duplicate hostname fetches.
- Fetch Zscaler Client Connector enrolled devices - Select this option to fetch enrolled devices from the Zscaler Client Connector.
Note
When Fetch Zscaler Client Connector enrolled devices is selected, you must enter a value in the Company ID parameter.
- Fetch Firewalls - Select this option to fetch firewall policies data.
- Filter SaaS Applications data by timeframe - Filter the SaaS Apps report by the selected time period.
- Ignore SaaS Applications without users - Select this option to not fetch SaaS applications not assigned to any user.
- Ignore SaaS Applications Repository and parse all applications - Select this option to fetch all applications even if they are not in the Axonius SaaS Applications Repository.
- Filter out applications by name - Enter a name to filter out applications.
- Filter out applications by category - Enter a category to filter out applications.
- SaaS Applications Source - Select the source from with to fetch SaaS Applications: Shadow IT Report, Inferred by Insight Logs, or Both.
- Include Linux devices - Select this option to include devices that have the Linux operating system on the device fetch.
- Device Types to be Fetched - Filter the devices you want to fetch by registration status. Select between All states except Removed, Registered (default), Removal Pending (default), Unregistered, Removed, and Quarantined.
- Enable real-time asset updates (Zscaler Nanolog Streaming Service) - Enable this if you want to fetch Zscaler Logs from a remote location.
Advanced Configuration
- RateLimit (requests/hour) (optional, default: 700) - Enter the maximum rate of requests per hour by Axonius to the Zscaler server.
Note
For details on general advanced settings under the Adapter Configuration tab, see Adapter Advanced Settings.
Related Enforcement Actions
Updated 2 days ago
