Splunk
Splunk captures, indexes, and correlates real-time data in a searchable repository.
Types of Assets Fetched
This adapter fetches the following types of assets:
- Devices, Users, Aggregated Security Findings, Software, Business Applications, SaaS Applications, Tickets
Parameters
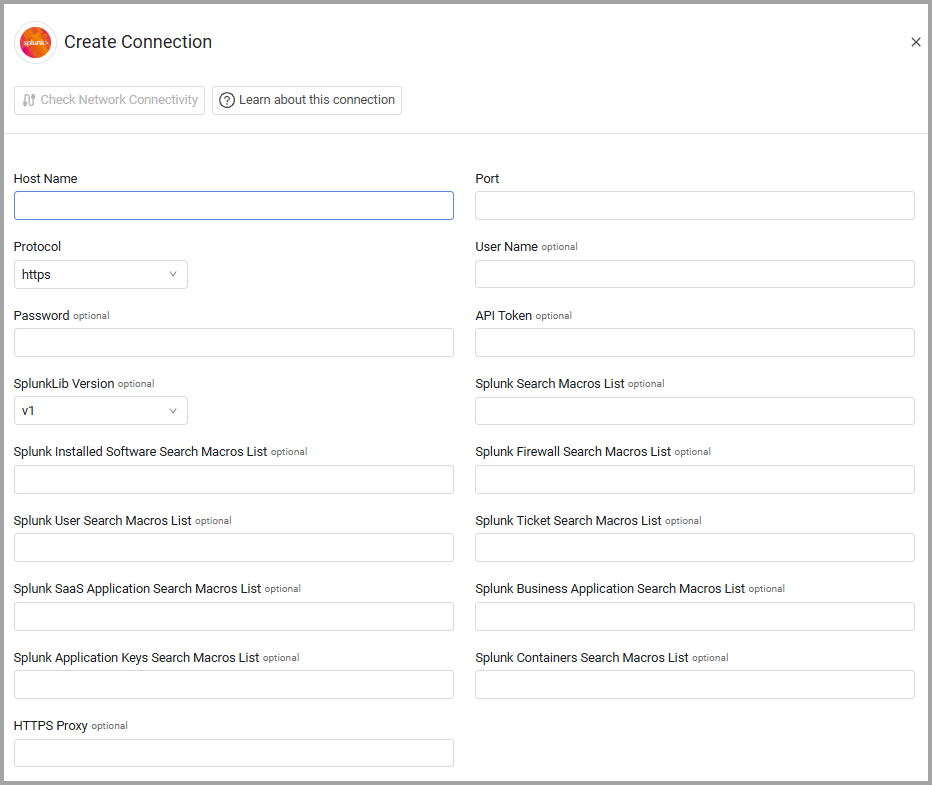
- Host Name (required) - The hostname of the Splunk search head.
To use Splunk Cloud, follow these steps:
- Ensure that the Axonius Instance Public IP address is whitelisted in Splunk Admin Config Service. To add the Public IP address of the Axonius Instance to the IP Allow List in Splunk Cloud, follow these steps:
Settings > Server Settings > IP Allow List > Search Head API Access
- For a single address (not a subnet), enter the address appended with a /32. Example: xxx.xxx.xxx.xxx/32 For more information, see Configure IP allow lists for Splunk Cloud Platform.
- Ensure that the user name has permission to query 'index' and '_internal'.
- Enter the host name in the following format:
customerName.splunkcloud.com
- Ensure that the Axonius Instance Public IP address is whitelisted in Splunk Admin Config Service. To add the Public IP address of the Axonius Instance to the IP Allow List in Splunk Cloud, follow these steps:
Settings > Server Settings > IP Allow List > Search Head API Access
Note
Make sure that the
customerNamedoes not contain HTTP or HTTPS.
- Port (required) - Specify an API port for the host. TCP/8089 is the typical default for both Splunk and Splunk Cloud. For more details, see Splunk Docs - Securing Splunk Enterprise. Open a ticket with Splunk to ensure port 8089 is open for your Splunk deployment.
- Protocol (required, default: HTTPS) - Select either HTTP or HTTPS protocol when using the specific adapter connection. Splunk Cloud can only use HTTPS protocol.
- User Name and Password (optional) - The user name and password for an account that has read access to the API. The user name must have read access to _internal index.
- To create a new user with read permissions, follow the tutorial in the official Splunk documentation. Splunk Cloud users should follow the steps detailed in Accessing the Splunk Cloud Platform REST API to access the API.
Note
When API Token is not supplied, User Name and Password are required.
- API Token (optional) - API token can be used instead of user name and password. The token must have read access to _internal index. If User Name and Password are not supplied, API Token is required. For more information, refer to Use Splunk Web to create authentication tokens.
Note
For the following Splunk Macro fields:
Titles cannot contain the following keywords: DHCP, Cisco, VPN, Windows Login, Splunk agent version, Nexpose, and Landesk.
Macro titles should follow the format:
|application_namespace:macro_name.The | (pipe) prefix is only needed for macros that begin with a generating command such as search, tstats, pivot, etc.
'application_name' is the name of the application if the macro is outside of the default Splunk search.
'macro_name is the name of the existing macro in Splunk that you want to use.
Examples:
|foreignApp1:Windows-axonius
|macrostartingwithsearch
simplemacro
- If the macro string begins with 'search ', the associated search query is used exactly as entered. This means you can enter Search Processing Language (SPL) queries directly, without needing to add extra logic.
- SplunkLib Version - Select the version of the Splunk library to use.
- Splunk Search Macros List (optional) - Specify a comma-separated list of Splunk search macros names. For details on Splunk search macros, see Splunk Knowledge Manager Manual - Define search macros in Settings.
-
Axonius will run the Splunk search macros names and will consider the results as if those were received from a CSV file. This means the search macros must include at least one column of required data as specified in the CSV adapter - Which fields will be imported with a devices file?.
-
If supplied, Axonius will run the specified search macros and will fetch devices from the results for this adapter.
- To execute macros that are defined outside of the default 'Search' Splunk application, specify the application namespace name before any applicable macro name followed by a colon.
-
If not supplied, this adapter will not include any search macros results in the fetched data.
-
- Splunk Installed Software Search Macros List (optional) - Specify a comma-separated list of Splunk search macro names that provide installed software information. For details on Splunk search macros, see Splunk Knowledge Manager Manual - Define search macros in Settings.
-
Axonius will run the Splunk search macros names and will consider the results as if those were received from a CSV file with installed software information. This means the search macros must include at least one column of required data as specified in the Which fields will be imported with a software applications file?.
-
If supplied, Axonius will run the specified search macros and will fetch installed software from the results and associate them to device entities for this adapter.
- To execute macros that are defined outside of the default 'Search' Splunk application, specify the application namespace name before any applicable macro name followed by a colon.
- “if the results include the following columns, then Installed Security Patch data will be added to devices where available:
hostname(required),security_patch_name(required),state(optional),installed_on(optional),patch_id(optional)
-
If not supplied, this adapter will not include any search macros results in the fetched data.
-
- Splunk Firewall Search Macros List (optional) - Specify a comma-separated list of Splunk search macro names that provide firewall information.
- Splunk User Search Macros List (optional) - Enter a list of macros. When populated this field is used to to query the macros that are defined within it to create User objects that will be parsed into Axonius. The macro should return at least one of the following fields to be used as a unique identifier: 'id', 'username', 'mail', 'name', 'userprincipalname'. Other fields that are not used as the user id will be added dynamically, i.e. any field the macro fetches should be available in Axonius.
- Splunk Ticket Search Macros List (optional) - Specify a comma-separated list of Splunk search macro names that provide ticket information.
- Splunk SaaS Application Search Macros List (optional) (only for accounts with Axonius SaaS Applications) - To execute a macro defined outside of the default "Search" Splunk application, specify the application namespace name before any applicable macro name with colon appended.
- Splunk Business Application Search Macros List (optional) - Specify a comma-separated list of Splunk search macro names that provide business application information.
- Splunk Application Keys Search Macros List - Specify a comma-separated list of Splunk search macro names that provide application key information.
- Splunk Containers Search Macros List - Specify a comma-separated list of Splunk search macro names that provide container information.
- HTTPS Proxy (optional) - Connect the adapter to a proxy instead of directly connecting it to the domain.
To learn more about common adapter connection parameters and buttons, see Adding a New Adapter Connection.
Advanced Settings
Note
Advanced settings can either apply to all connections for this adapter, or to a specific connection. Refer to Advanced Configuration for Adapters.
- Number of days to fetch (required, default: 30) - Specify the query size by number of days Axonius will request to fetch data from all the connections of this adapter.
- Maximum amount of records per search (required, default: 100000) - Specify the maximum number of records Axonius should fetch from all the connections of this adapter.
- Windows login hours to fetch (required, default: 3) - Specify the Windows login data query size by hours Axonius will request to fetch from all the connections of this adapter.
- Fetch devices from the splunk-nexpose plugin - Select this option to fetch the devices data from splunk-nexpose plugin.
- Fetch devices from Cisco (required, default: true) - By default Axonius fetches the devices data from Cisco data in Splunk. Clear this option to not fetch the devices data from Cisco data in Splunk.
- Fetch DHCP data (required, default: true) - Select this option to fetch DCHP data. This option is only relevant for customers who have the
axonius_dhcpSplunk macro and theindex=winevents sourcetype=DhcpSrvLogSplunk search in their system. - Fetch Winlogon data (required, default: true) - By default Axonius fetches Winlogon data. Clear this option to not fetch Winlogon data.
- Fetch VPN data (required, default: true) - By default Axonius fetches VPN data. Clear this option to not fetch VPN data.
- Fetch Splunk agent version - Select this option to fetch information about the Splunk agent version.
- Fetch custom agents - Select this option to fetch agent versions using the Splunk Search Macros Listconnection parameter. For this parameter, enter a macro including the ‘name’ and ‘version’ fields. The results fetched from Splunk will be parsed under the aggregated Agent Versions field.
- Override default agent search timeframe to be one minute - Select whether to limit the agent search timeframe for Splunk devices to the most recent snapshot.
- Set time zone for last seen (+/- UTC) - Select a Splunk time zone to adjust the value last seen. If default '+0' is selected and last seen is a time in the future, the value will be skipped. If '+0' is not selected and last seen is a time in the future, the value will be used as last seen with the defined time difference.
- Query to parse browsed applications from web activity logs - Enter a query to parse browsed applications from web activity logs.
- Custom Parsing refer to Custom Parsing
Note
For details about general advanced settings under the Adapter Configuration tab, see Adapter Advanced Settings.
APIs
Axonius uses the following APIs:
- Splunk: Splunk Enterprise REST API
- Splunk Cloud: Splunk Cloud Platform REST API
Permissions
The value supplied in API Token must have the user role and read access to _internal index in order to fetch assets.
The credentials in use should have permission to use any specified macro.
For further information refer to Create authentication tokens.
Related Enforcement Actions
Updated 13 days ago
