What's New in Axonius Asset Cloud 6.1.65
Release Date: May 4th 2025
These Release Notes contain new features and enhancements added in version 6.1.65
-
Read What's New in Axonius 6.1 to see all Axonius 6.1 features.
Axonius Exposures
Axonius Exposures provides a comprehensive approach to managing and mitigating risk across your entire IT ecosystem. Axonius Exposures aggregates data from various sources and continuously discovers security findings, helping you stay on top of your environment in real time.
Here's how you can benefit from Exposures:
- Receive a unified view of all the vulnerabilities in your organization and their hosts.
- Improve prioritization - with asset, vulnerability, and network context.
- Visualize connections between threats and assets.
- Track vulnerability resolution status, and time to resolution.
- Set and track SLA and compliance.
- Identify internet-exposed assets for comprehensive risk score calculation.
Exposures offers the following:
Vulnerabilities
The Vulnerabilities page offers a consolidated view of all the vulnerabilities in your organization from all sources.
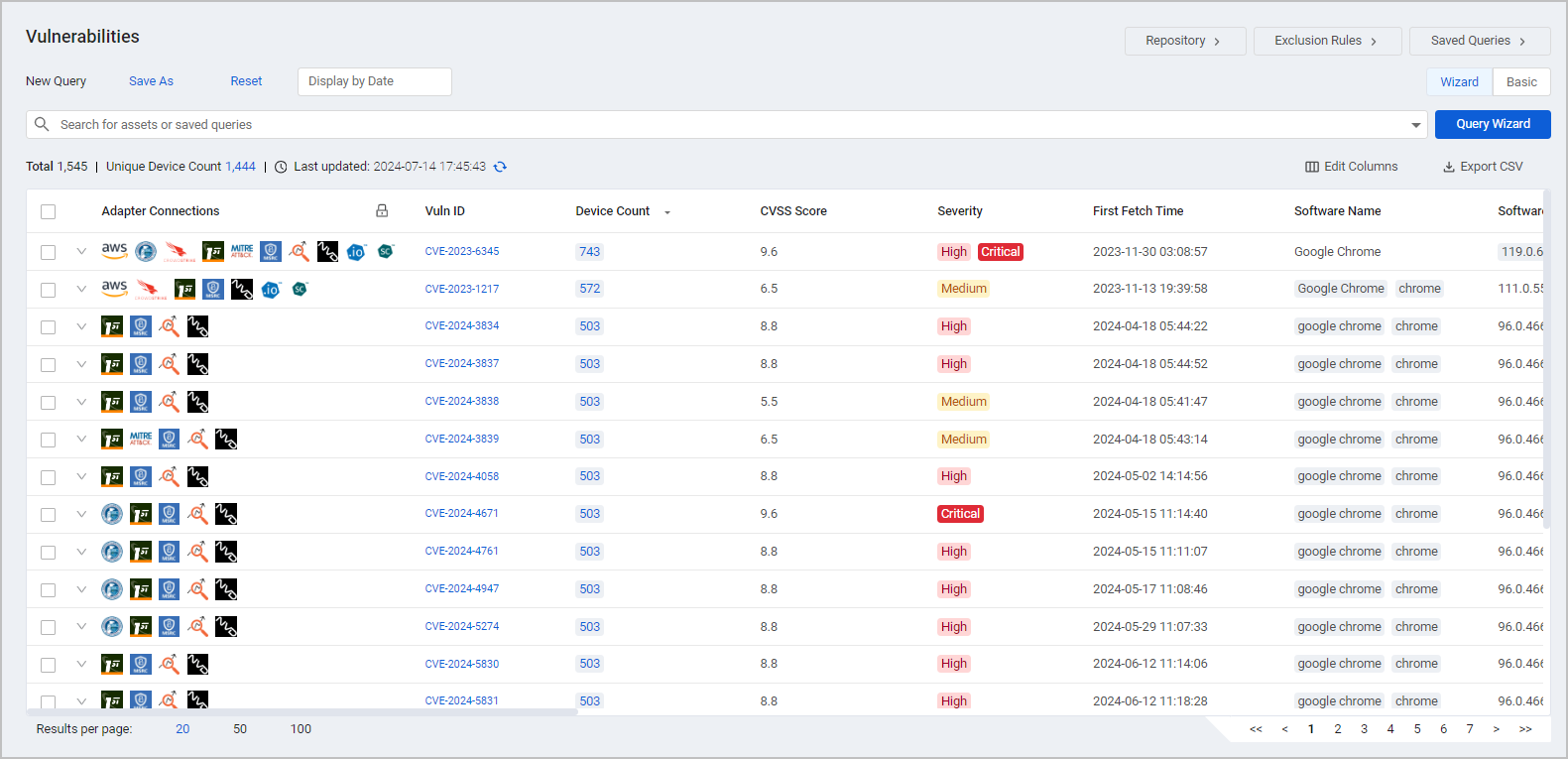
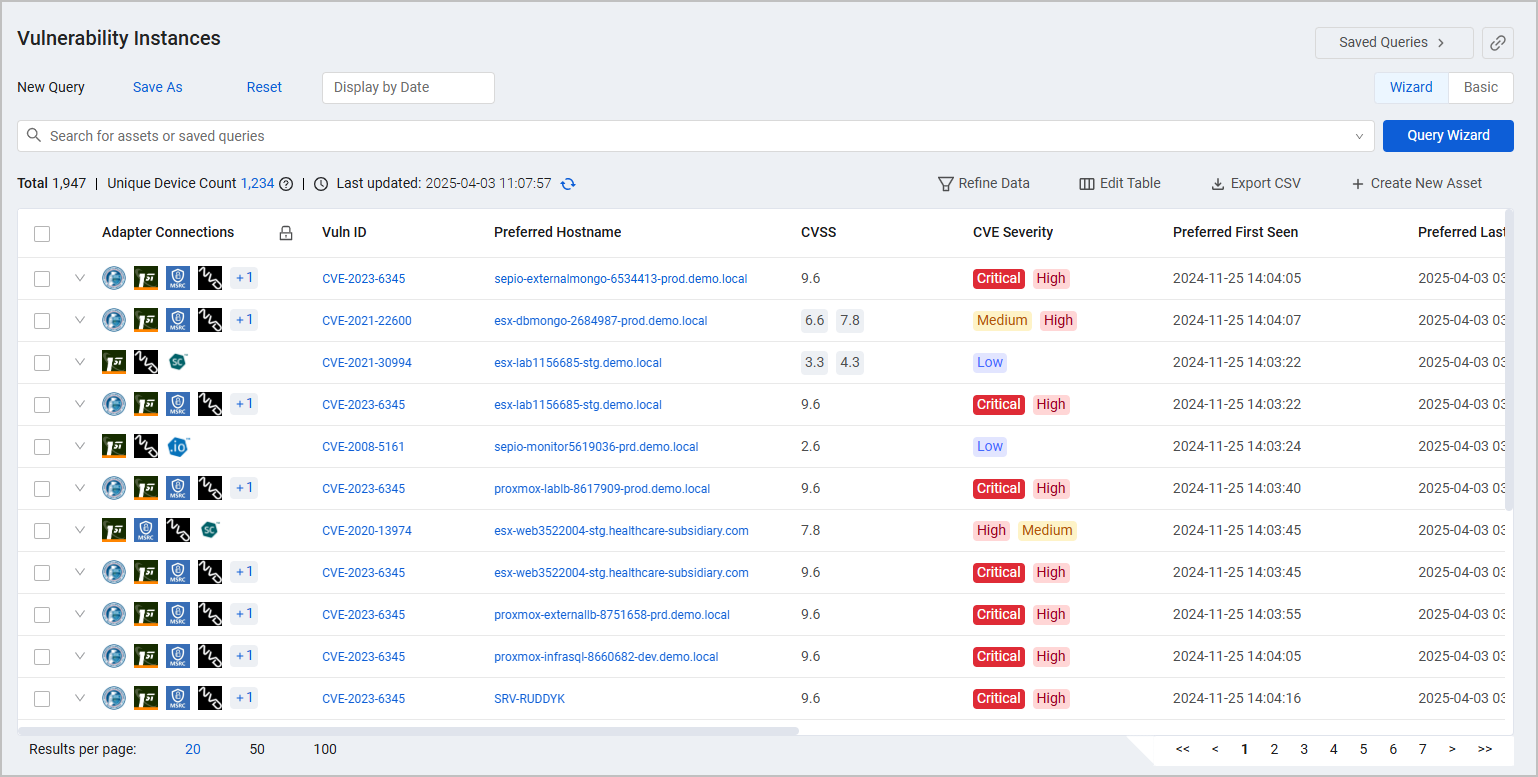
Vulnerability Instances
The Vulnerability Instances page lists vulnerabilities in the context of specific hosts. The Vulnerability Instances view helps security, IT, and risk teams identify vulnerabilities in specific devices, enabling them to prioritize vulnerabilities by combining security, asset, and business context from a single place.
Risk Score Calculation
Axonius Risk Score Calculation offers a robust solution to assess threat levels and prioritize remediation efforts. Users can calculate the risk scores of different asset types by creating custom conditions and parameters, based on account risk, business impact, and exploitability considerations.
.png)
Axonius uses a variety of sources to collect information on reported CVEs and enriches them with that information, including severities and details on the vulnerable software or vendor. The enrichment sources used by Axonius are as follows:
| Source name | Details |
|---|---|
| NVD | Indicates Vulnerabilities enriched with data from the NIST NVD database. |
| EPSS | Indicates software vulnerabilities enriched with details from the Exploit Prediction Scoring System EPSS from connected adapters. |
CISA  | Indicates Vulnerabilities enriched with vulnerabilities information from your connected adapters with additional details from the CISA Known Exploited Vulnerabilities (KEV) Catalog. When relevant, the CISA fields and information are available for viewing and querying in the Vulnerabilities module and Devices module. Only CVEs that are part of the CISA KEV Catalog will be enhanced. |
MSRC  |Indicates software vulnerabilities enriched with details from MSRC from connected adapters. |
|Indicates software vulnerabilities enriched with details from MSRC from connected adapters. |
| VulnCheck 
 | Provides cyber threat intelligence to assess, identify, and manage potential risks.
| Mandiant Enrichment
| Provides cyber threat intelligence to assess, identify, and manage potential risks.
| Mandiant Enrichment 
Axonius Static Analysis identifies CVEs within the installed software reported by adapters. To achieve this, Axonius leverages Common Platform Enumerations (CPEs) and the National Vulnerability Database (NVD). The process includes mapping every installed software on each device, normalizing the data, converting it into the calculated CPE of the installed software, and then - based on the information received from NVD - listing all CVEs associated with the software installed on each device.
The Publicly Exposed by table shows assets that are reachable by external attackers as network traffic changes IP through subnets, load balancers, and firewalls. Axonius compiles the Public Exposed By information by reading configuration from your network equipment, such as load balancers and firewalls.
Software Assets New Features and Enhancements
The following new features and enhancements were added to Software Assets:
The "Is Excluded" field was added to the Software page. This aggregated field exists only if certain adapters (for example: Jamf Pro) have the "Installed Software: Is Blacklisted" field in the Devices page.
Axonius Platform New Features and Enhancements
Dashboard New Features and Enhancements
The following new features and enhancements were added to the Dashboards:
Chart Enhancements
Compare Results to Previous Date on Adapter Segmentation Chart
The Adapter Segmentation chart now supports comparing query results to a previous date. This provides additional context for your data and highlights changes in the results.
Dashboard-Level Filters Are Applied in the Chart Wizard Preview
When a filter is applied to a dashboard, that same filter is displayed, but cannot be edited, in the Chart Wizard preview for each of the charts in that dashboard.
Adapter Pages and Adapter Interface New Features and Enhancements
The following updates were made to the common functionality across all adapters:
Adapter Interface
Adapter Fetch History Enhancements
-
A Refresh button was added to the Adapter Fetch History page that allows users to refresh the data on the page without losing the filters configured.
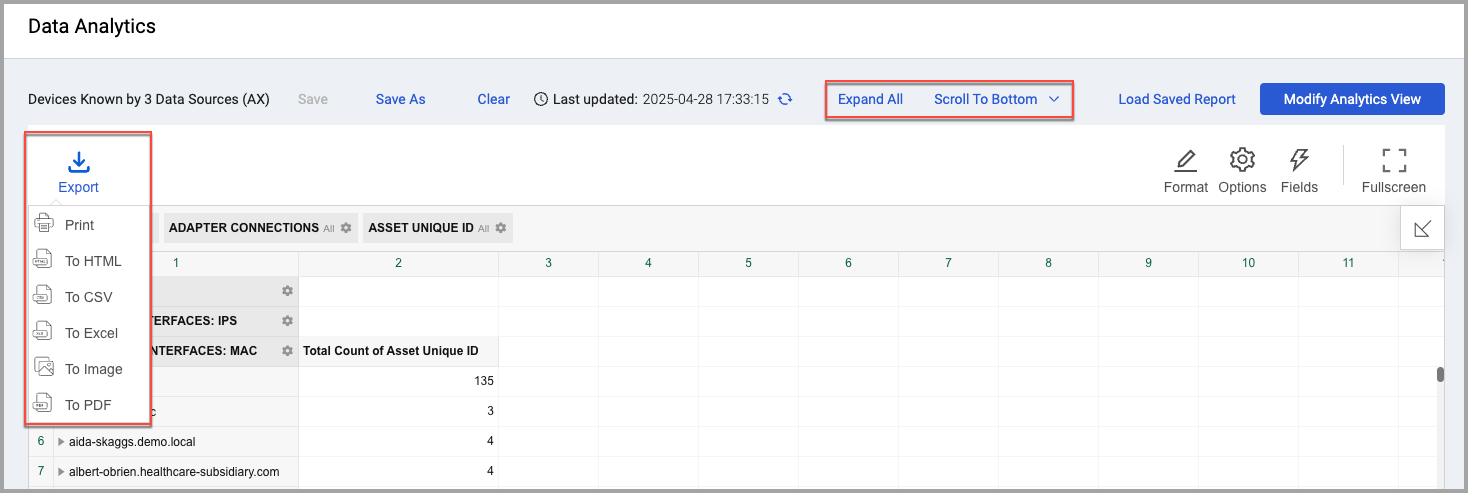
Data Analytics New Features and Enhancements
The following updates were made to the Data Analytics module:
- All rows can be expanded or collapsed at the same time.
- The number of rows displayed automatically fits the size of the screen.
- View the total row at bottom of the table using Scroll to Bottom and return with Scroll to Top.
- Blank values are removed with the empty field not "blank".
- Export data analytics reports to the following formats: Print, HTML, CSV, Excel, Image, and PDF.
- Apply color scheme to the table.
Enforcement Center New Features and Enhancements
The following new features and enhancements were added to the Enforcement Center:
Enhancements to Axonius Actions
Axonius - Export Assets to Instance
Added the option to only export assets from the asset type that is queried.
Axonius - Send Email per Asset
Added the option for the Plain-text mail to include the custom message only.
Adapter and Enforcement Action Updates
New Adapters
The following new adapters were added:
- Bently Nevada
- Bently Nevada is a condition monitoring system that provides asset protection and predictive maintenance solutions. (Fetches: Devices)
- Cisco Nexus Dashboard
- Cisco Nexus Dashboard is a platform that offers centralized management and monitoring for network operations. (Fetches: Devices)
- Mandiant Enrichment
- Mandiant is a cybersecurity platform offering threat intelligence, incident response, and security consulting services to detect and mitigate advanced cyber threats. (Fetches: Devices)
- ZipHQ
-
ZipHQ License Management is a comprehensive software solution designed to streamline and automate the management of software licenses across an organization. (Fetches: Licenses, SaaS Applications)
-
Adapter Updates
The following adapters were updated:
-
Active Directory Certificate Services (AD CS)
- Added the capability to enter a semicolon-separated list of templates to exclude from the fetch.
- Added the capability to set a future expiration date to filter certificates by.
-
Akamai Kona WAF - Added the option to fetch Rules tree and hostname list from Property Manager.
-
Amazon Web Services (AWS) - Added the option to enrich RDS assets with KMS information.
-
BeyondTrust Remote Support - Added the option to not parse public IPs to Network Interfaces.
-
Burp Suite - This adapter now fetches domains and URLs as assets.
-
CyberArk Privileged Account Security - Added the option to enrich Users and Groups with permitted safes.
-
Forcepoint ONE - Added support for OAuth authentication.
-
Google Cloud Platform (GCP) - Added the option to fetch Google Instance Groups as Compute Services.
-
HPE Switches - SNMP Protocol was added to connection parameters.
-
- The name of the 'IBM Guardium' adapter was changed to IBM Guardium Data Protection.
- Added the option to fetch STAP configuration.
-
Ivanti Service Manager - URL Base Prefix was added to connection parameters.
-
LogicGate - Added the option to enrich users with records.
-
ManageEngine Network Configuration Manager
- This adapter now fetches vulnerabilities and SaaS applications.
- Added the option to enrich the device summary with device vulnerabilities.
-
Microsoft Azure - This adapter now fetches Traffic Manager Profiles as Load Balancers.
-
- Software Query ID was added to connection parameters.
- This adapter now fetches software and SaaS applications. An optional advanced setting can be configured to do this.
-
Nutanix AHV - Added the option to parse the serial field from the 'block_serial' raw data instead of 'serial'.
-
Oracle Fusion HCM Cloud - Added the option to parse user assignments as Security Roles.
-
Proofpoint Endpoint DLP - Added an option to parse
Last Seen (Updater)and 'Last Seen' fields with the same value. -
ServiceNow - Added the new Devices: Unset Downstream and Upstream fields if not populated in fetch results option to automatically clear existing field values in the Downstream and Upstream complex object fields on devices when no new values are returned during a ServiceNow fetch. This is useful for optimizing 'delta fetches' (double fetching).
-
Tenable.io - Added an option to prevent the adapter from duplicating plugins.
New Enforcement Actions
The following Enforcement Actions were added:
- Google Workspace - Delete / Wipe Cloud Device - Removes and wipes devices from Google.
- Azure DevOps - Update Task - Changes the status of a DevOps work item to a status defined by a user.
- SysAid - Update Ticket - Updates SysAid tickets.
Updated Enforcement Actions
The following Enforcement Actions were updated:
-
Axonius - Export Assets to Instance - Added the Export only the queried asset type field that when selected, only assets of the asset type selected when creating the Enforcement Action are exported.
-
Microsoft Teams - Send message - Added the option to replace message body under Additional text in message body section.
-
ServiceNow - Create Asset
- Added IRE Configuration
- Moved mapping of Axonius fields to ServiceNow IRE fields
- Reorganized other configuration fields
-
Zendesk - Create Custom Object per Asset - Added the option to create a custom object key if it does not exist
Updated 4 months ago
