SentinelOne
SentinelOne is an endpoint protection solution including prevention, detection, and response.
Asset Types Fetched
- Devices, Aggregated Security Findings, Users, Software, Roles, Groups, Application Settings, SaaS Applications, Alerts/Incidents
Before You Begin
Resources Required to Fetch Application Settings
All asset types require the same parameters and permissions, except for Application Settings, which require the following:
- Parameters: SentinelOne Domain, User Name, Password, and 2FA Secret (or API token in certain use cases)
- Advanced setting: Fetch Application Settings
- Permission: Site Viewer access to the management server
To set up multi-factor authentication:
- Enable 2FA in SentinelOne.
- Log in to SentinelOne.
- After entering the user name and password, the 2FA page displays a QR Code and a token. Copy the token.
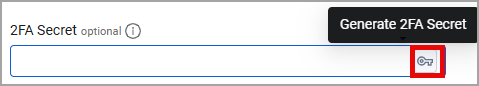
- On the adapter’** Add Connection** section in Axonius, click the Generate Secret Key icon from the 2FA Secret field.
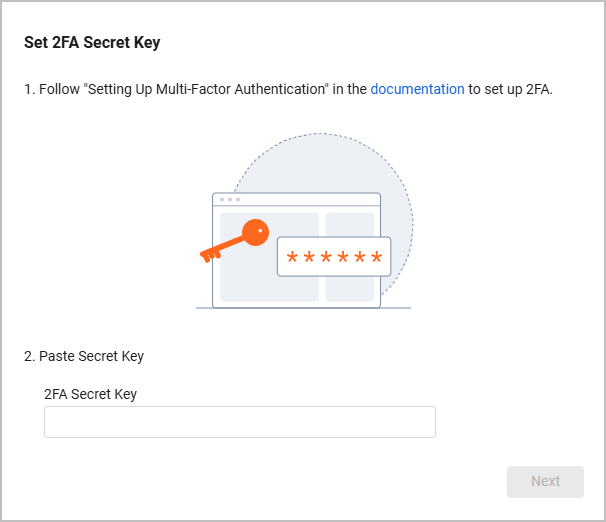
- The Set 2FA Secret Key screen opens. Enter the copied token into the 2FA Secret Key field and click Next.
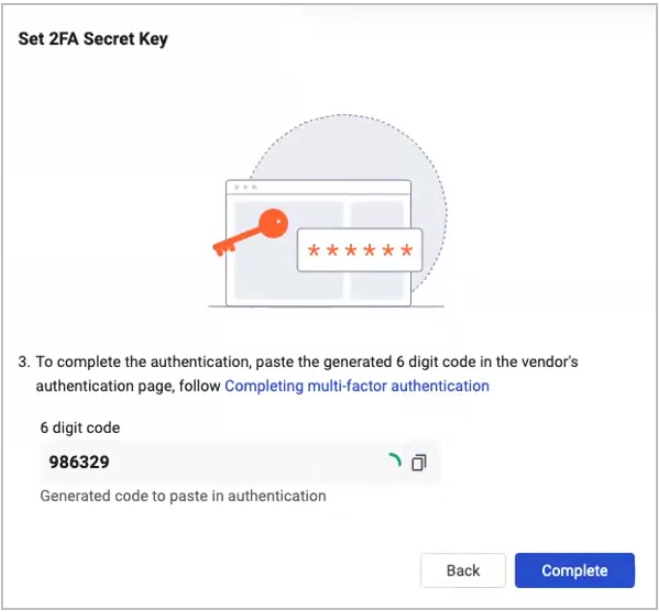
- Click the Copy icon to copy the 6-digit code displayed.
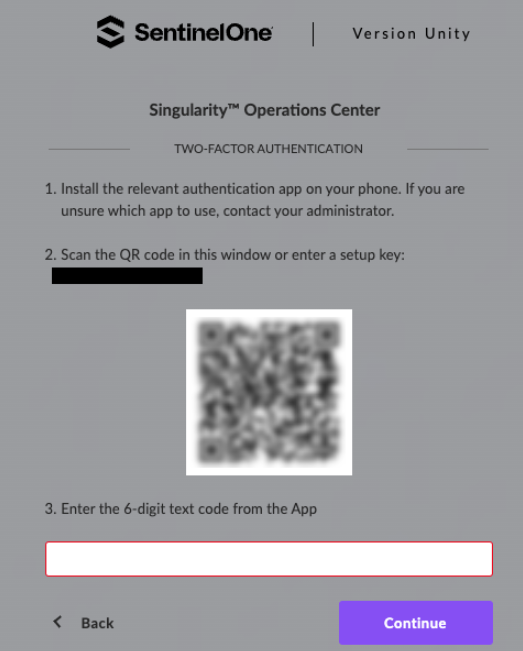
- On the SentinelOne Two-Factor Authentication screen, paste the code in the appropriate field and click Continue.
- Back in Axonius, click Complete in the Set 2FA Secret Field dialog.
- Click Save.
General Resources
APIs
Axonius uses the following APIs according to the asset type fetched:
Asset Type | API Endpoints |
|---|---|
Devices |
|
Users |
|
Aggregated Security Findings |
|
Software |
|
Roles |
|
Groups |
|
SaaS Applications + Events (Deep Visibility Events used to enrich Devices) |
|
Alerts/Incidents |
|
Permissions
- To connect this adapter, you can use the default Read-Only Viewer role that provides read-only access to the system.
- When connecting with Singularity Data Lake (SDL) API Key (see Optional Parameters), Log Read Access permission level is required.
Connecting the Adapter in Axonius
To connect the adapter in Axonius, provide the following parameters:
Required Parameters - All Asset Types
- SentinelOne Domain - The hostname or IP Address of the SentinelOne management server. This field format is
[instance].sentinelone.net.
Required Parameters - Application Settings
- User Name and Password - The credentials for an account that has site viewer access to the management server. For information on how to create users in SentinelOne, see Create a Single User.
- 2FA Secret Key - The secret generated in SentinelOne for setting up 2-factor authentication. See Resources Required to Fetch Application Settings for more information.
- API token - you must provide an API token only in the following cases:
- When you’re using API V1 and you don’t provide User Name and Password.
- When you’re using API V2 and 2FA authentication is enabled. In this case, leave the User Name and Password fields empty and enter an API token.
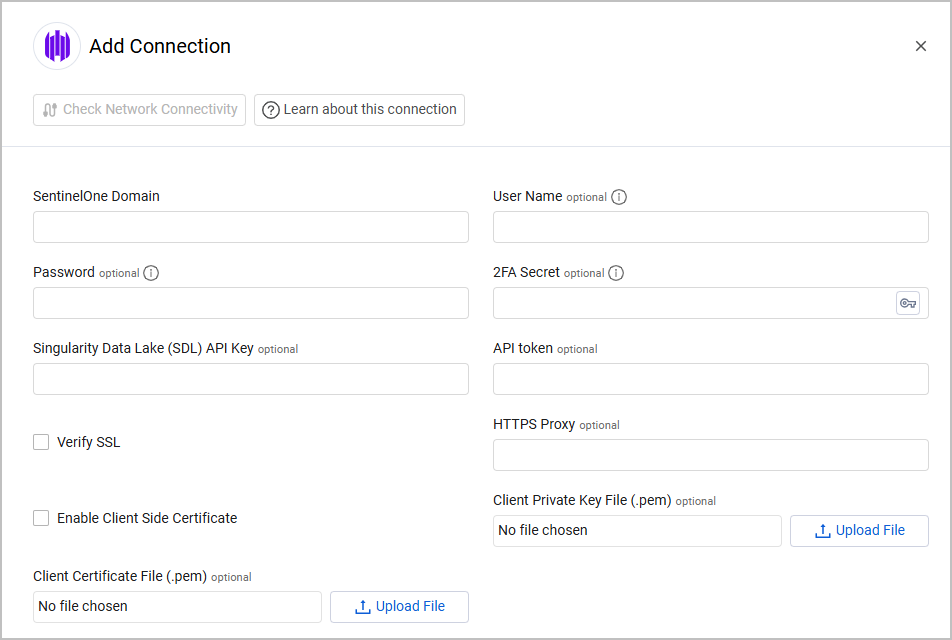
Optional Parameters
-
Verify SSL - Select whether to verify the SSL certificate of the server against the CA database inside of Axonius. For more details, see SSL Trust & CA Settings.
-
HTTPS Proxy - Connect the adapter to a proxy instead of directly connecting it to the domain.
-
Singularity Data Lake (SDL) API Key - To enable SDL queries in the Advanced Settings, enter the API Key from the Singularity Data Lake. Note: this requires Log Read Access permission.
-
Enable Client Side Certificate - Select to enable Axonius to send requests using the certificates uploaded to allow Mutual TLS configuration for this adapter. If you enable Mutual TLS on your SentinelOne environment, this parameter is required.
- Click Upload File next to Client Private Key File to upload a client private key file in PEM format.
- Click Upload File next to Client Certificate File to upload a public key file in PEM format.
To learn more about common adapter connection parameters and buttons, see Adding a New Adapter Connection.
Advanced Settings
Note:
Advanced settings can either apply to all connections for this adapter, or to a specific connection. Refer to Advanced Configuration for Adapters.
- Fetch applications - Select to fetch SentinelOne applications.
Note
To fetch SentinelOne applications, you must configure Application Scanning in your SentinelOne environment. This is relevant for every Axonius version starting from 6.1.13.
- Fetch application CVEs - Select whether to fetch CVE security vulnerability information for software.
Note
SentinelOne can also fetch non-CVE threats and parse them into the Security Findings table. To enable this capability, contact Axonius support.
- Ignore vulnerabilities from ubuntu packages - Select to ignore vulnerabilities of software detected as an ubuntu package.
- Fetch decommissioned devices - Select whether to fetch devices that are decommissioned.
Note
To fetch decommissioned devices, you must have the Endpoints View Credentials permission.
- Fetch threats for infected devices - Select this option to fetch threats of a device when the infected value on the SentinelOne server is set to True. When you enable this setting, the adapter also fetches MITRE ATT&CK techniques from threat indicators to the device.
- Fetch threats only for selected incident statuses - Select which threat incident statuses should be fetched: Unresolved, In Progress, or Resolved. (You can select more than one)
- Fetch device control events - Select this option to fetch the device control events for each device.
- Fetch Application settings - Select this option to fetch application settings for users.
- Fetch last installed software version only - Select this option to fetch only the version with the most recent installed date for each software.
- Deep Visibility query - Enter a SentinelOne Deep Visibility query name to fetch the query events and parse them inside the devices as “Deep Visibility Events“.
- Remove old tags - Select this option to remove old tags that are no longer being fetched from SentinelOne.
- Background fetch tasks - Select tasks from the drop-down that will be fetched in the background.
- Background fetch interval (Hours) (default: 72 (3 days)) - Set the interval in hours for background fetch.
- Background fetch data maximum age (Days) (default: 7 days) - Select this option to limit the maximum age of data retrieved during background fetches.
- Enable fetch from Skylight query - Toggle on to enable fetch from the Skylight query.
Note
When Enable fetch from Skylight query is enabled, enter the SDL query to fetch events. This requires you to configure the Singularity Data Lake (SDL) API Key parameter and have the Log Read Access permission.
- Ignore public IPs from externalIp field - Select this option to ignore public IPs from the externalIp field.
- Fetch uninstalled devices from V1 - Select this option to fetch uninstalled devices from V1.
- Parse Device Model without Manufacturer info - Select this option to parse the device model field without the manufacturer information in the model name.
- Enable real-time asset updates (Supported events: Recently activated devices) - Enable this option to fetch devices that have been recently activated and to trigger the respective event. All workflows configured with this event are then triggered.
- Fetch users - Uncheck this to disable user fetch.
- Fetch Last Reboot Date - Enable to fetch and display the Last Reboot Date for SentinelOne devices. The adapter will collect this information from an additional endpoint.
- Deduplicate devices by computer name and keeping greater agent version - Select this option to avoid fetching the same device with several agent versions by keeping the device with the latest agent version. The adapter will use the device’s "computer name" as the key to index data. Note that this process might increase disk usage and fetch time.
- Fetch firewall rules - Enable to fetch firewall rules for Devices. The results are written into the Firewall Rules table on the Device's Profile page.
- Fetch pending third-party application patches - Select to fetch OS Available Security Patches detected in third-party applications that are installed on devices.
- Fetch ransomware detections - Select to fetch ransomware detections, the results will be parsed into the device's Ransomware Detection field.
- Enrich devices with Deep Visibility events - Add Deep Visibility events you want to enrich Device data with. You can select more than one option from the menu.
- Last Interactive User Logons: timeframe (days) (default: 10) - Set the number of days to look back for to enrich devices with interactive user logons.
Note:
To learn more about Adapter Configuration tab advanced settings, see Adapter Advanced Settings.
Related Enforcement Actions
SentinelOne - Add or Remove Tag to/from Assets
SentinelOne - Execute Remote Script Orchestration
SentinelOne - Isolate/Unisolate a Device
SentinelOne - Change Asset Site
SentinelOne - Change Asset Group
Updated about 6 hours ago
