What's New in Axonius 6.1
Release Date: February 4th 2024
Axonius version 6.1 includes all of the features and enhancements from all the 6.0 minor releases since version 6.0.2. Read the release notes to learn what's new.
Ongoing Updates
Check out ongoing updates to Version 6.1:
- What's New in Axonius Asset Cloud 6.1.74
- What's New in Axonius Asset Cloud 6.1.73
- What's New in Axonius Asset Cloud 6.1.72
- What's New in Axonius Asset Cloud 6.1.71
- What's New in Axonius Asset Cloud 6.1.70
- What's New in Axonius Asset Cloud 6.1.69
- What's New in Axonius Asset Cloud 6.1.68
- What's New in Axonius Asset Cloud 6.1.67
- What's New in Axonius Asset Cloud 6.1.66
- What's New in Axonius Asset Cloud 6.1.65
- What's New in Axonius Asset Cloud 6.1.64
- What's New in Axonius Asset Cloud 6.1.63
- What's New in Axonius Asset Cloud 6.1.62
- What's New in Axonius 6.1.61
- What's New in Axonius 6.1.60
- What's New in Axonius 6.1.59
- What's New in Axonius 6.1.58
- What's New in Axonius 6.1.57
- What's New in Axonius 6.1.56
- What's New in Axonius 6.1.55
- What's New in Axonius 6.1.54
- What's New in Axonius 6.1.53
- What's New in Axonius 6.1.52
- What's New in Axonius 6.1.51
- What's New in Axonius 6.1.50
- What's New in Axonius 6.1.49
- What's New in Axonius 6.1.48
- What's New in Axonius 6.1.47
- What's New in Axonius 6.1.46
- What's New in Axonius 6.1.45
- What's New in Axonius 6.1.44
- What's New in Axonius 6.1.43
- What's New in Axonius 6.1.42
- What's New in Axonius 6.1.41
- What's New in Axonius 6.1.40
- What's New in Axonius 6.1.39
- What's New in Axonius 6.1.38
- What's New in Axonius 6.1.37
- What's New in Axonius 6.1.36
- What's New in Axonius 6.1.35
- What's New in Axonius 6.1.34
- What's New in Axonius 6.1.33
- What's New in Axonius 6.1.32
- What's New in Axonius 6.1.31
- What's New in Axonius 6.1.30
- What's New in Axonius 6.1.29
- What's New in Axonius 6.1.28
- What's New in Axonius 6.1.27
- What's New in Axonius 6.1.26
- What's New in Axonius 6.1.25
- What's New in Axonius 6.1.24
- What's New in Axonius 6.1.23
- What's New in Axonius 6.1.22
- What's New in Axonius 6.1.21
- What's New in Axonius 6.1.20
- What's New in Axonius 6.1.19
- What's New in Axonius 6.1.18
- What's New in Axonius 6.1.17
- What's New in Axonius 6.1.16
- What's New in Axonius 6.1.15
- What's New in Axonius 6.1.14
- What's New in Axonius 6.1.13
- What's New in Axonius 6.1.11
- What's New in Axonius 6.1.10
- What's New in Axonius 6.1.9
- What's New in Axonius 6.1.8
- What's New in Axonius 6.1.7
- What's New in Axonius 6.1.6
- What's New in Axonius 6.1.5
- What's New in Axonius 6.1.4
- What's New in Axonius 6.1.3
- What's New in Axonius 6.1.2
- Axonius 6.1 Ongoing Adapter and Enforcement Action Updates
Dashboard New Features and Enhancements
The following new features and enhancements were added to the Dashboards:
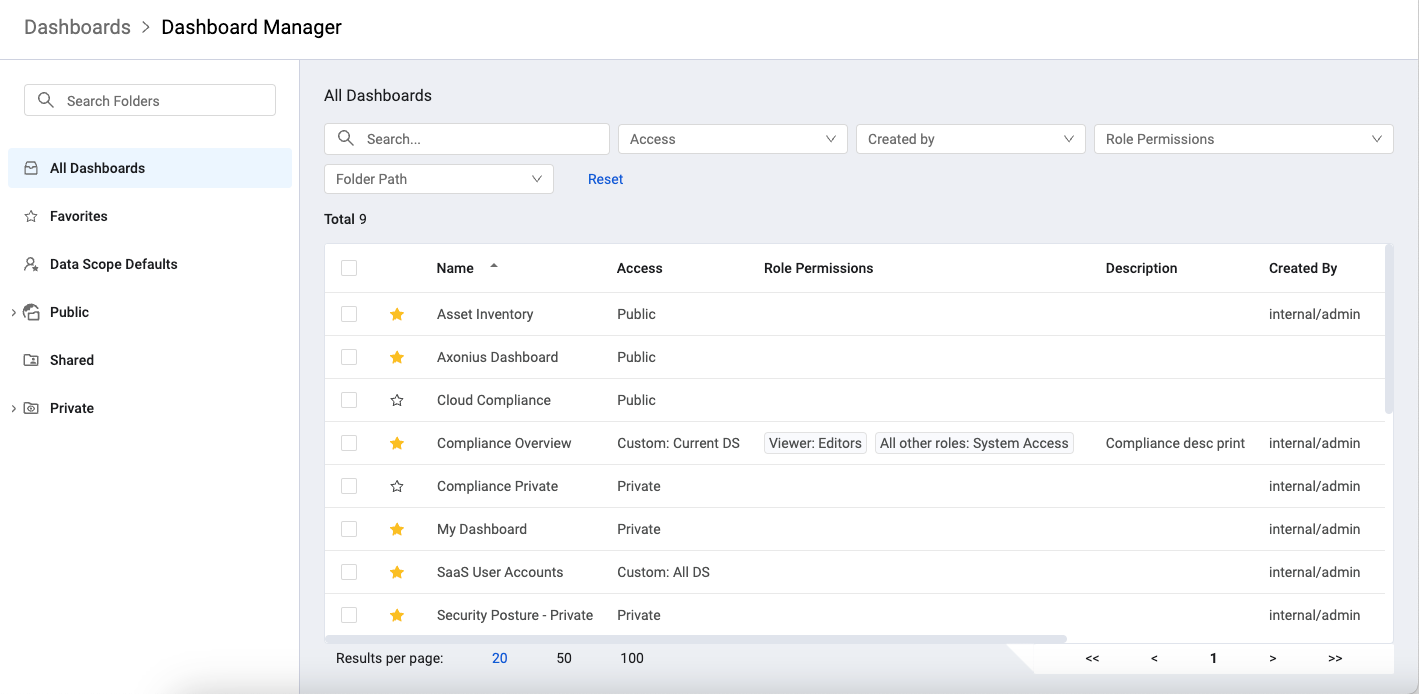
New Dashboard Manager
A new Dashboard Manager was added to the System. The Dashboard Manager page is used to manage the dashboards on the system. The Dashboard Manager table provides a centralized summary of information about all existing dashboards. Users can create, update, and delete dashboards as well as assign and arrange dashboard Favorites. It is also possible to define the default dashboards for the users' Data Scope.
- Subfolders created on the Dashboard Manager page, and dashboards placed in them, appear in the same arrangement on the Dashboards page.
- The Charts field in the Dashboard Manager allows users to view a list of charts for each dashboard.
Dashboard Import/Export Enhancements
Dashboards with Custom or Private access permissions can now be exported.
Chart Enhancements
Asset Table Widget
A new Asset Table widget was added. This allows users to view the results of a given query in an asset table format as part of the dashboard. View the result of a given query in a dashboard in the same way as in the asset tables (limited to aggregated view) with ability to set the columns displayed.
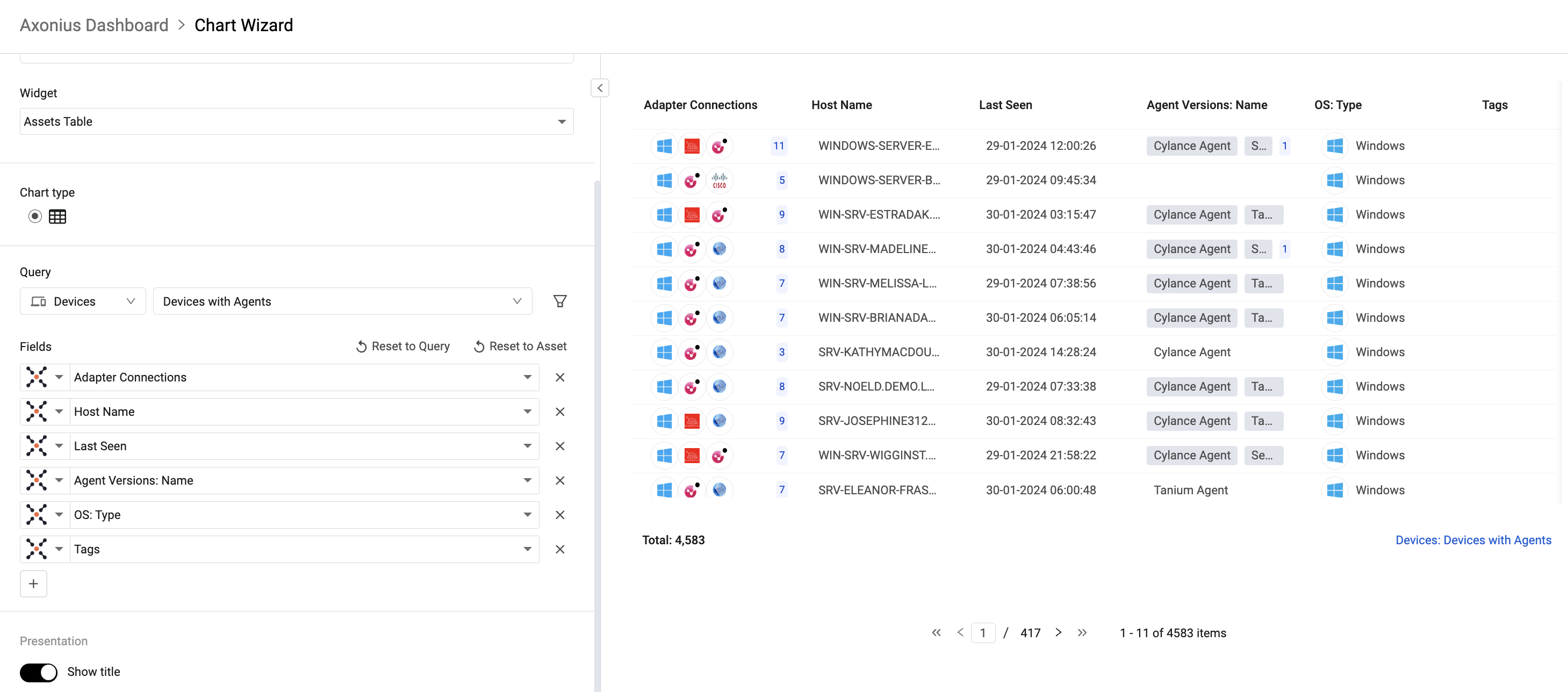
Chart Configuration Moved to the Left Side of the Chart When a chart is in Edit mode, the chart configuration now appears to the left of the chart.
Create a Query on the Fly from the Chart Configuration Users can now create a new query from within the chart configuration. Use filters to find the set of assets to represent on the chart and, using the Asset Preview pane, the filter can be used as a new saved query.
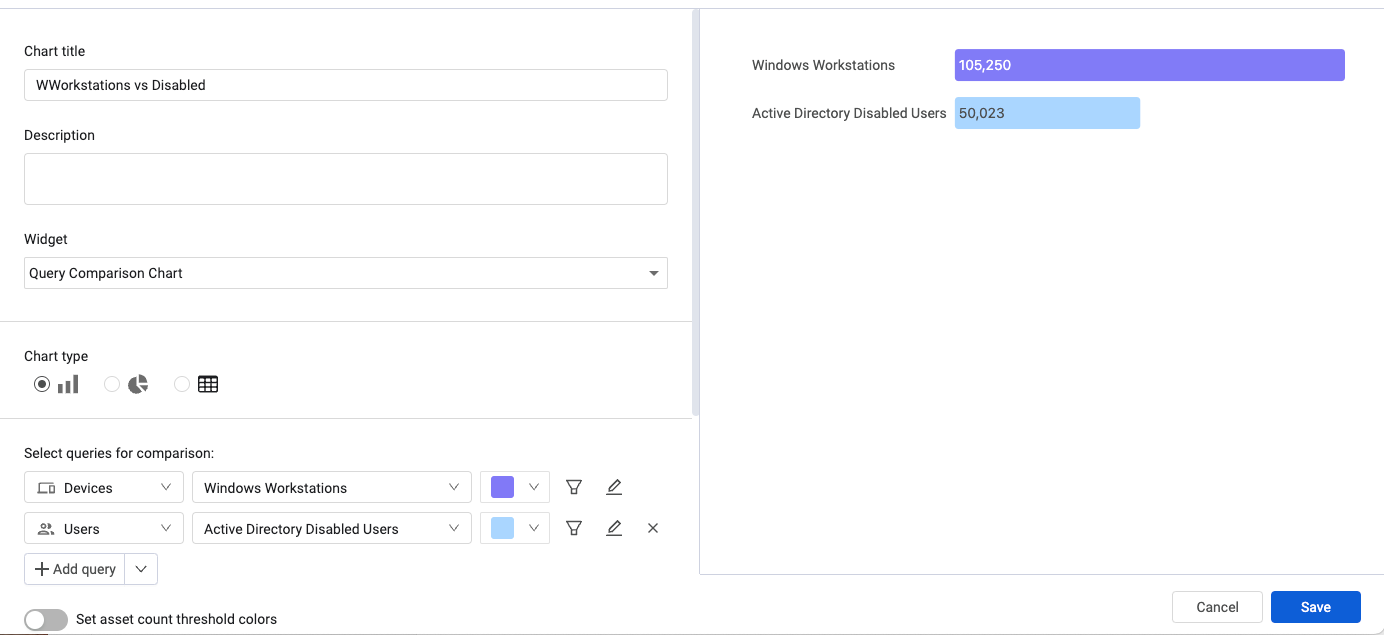
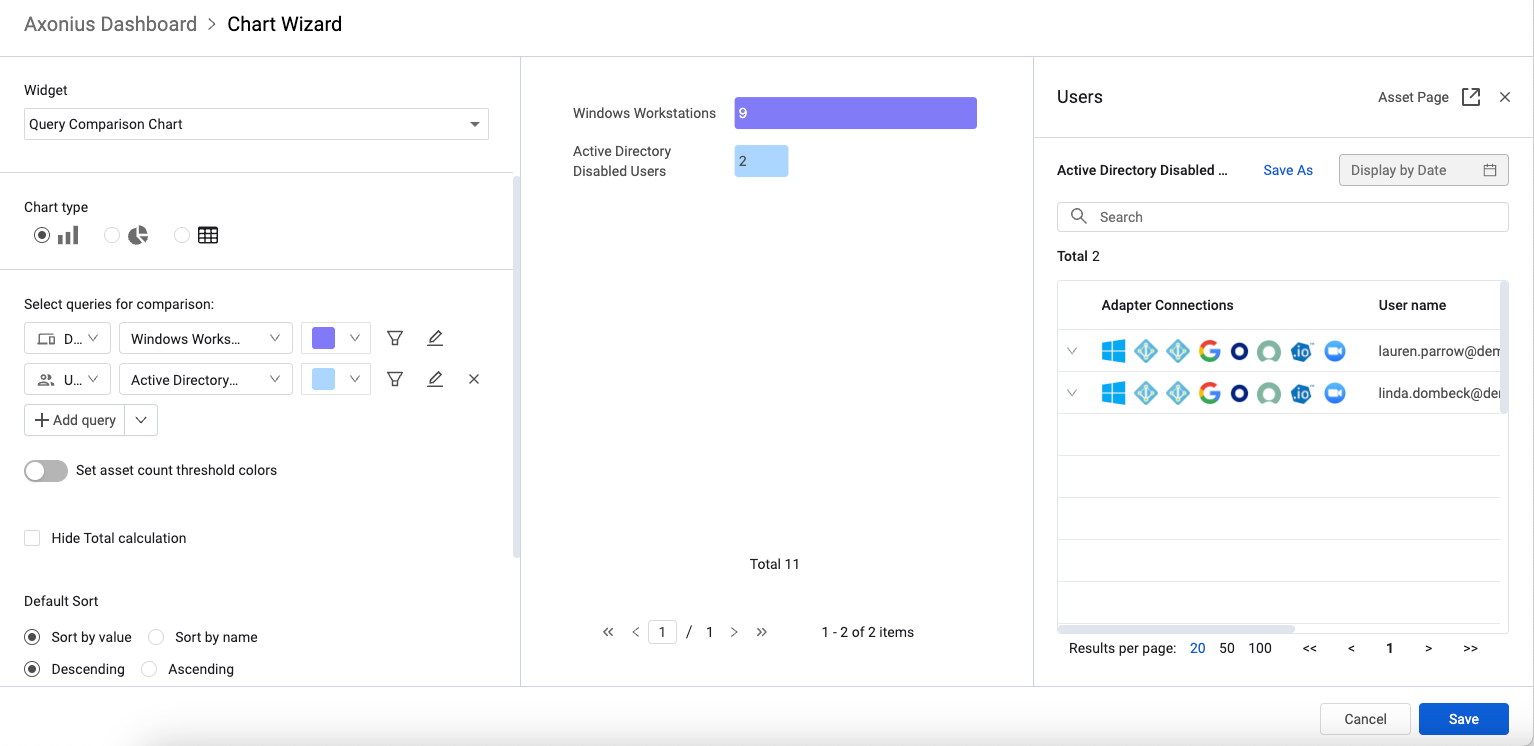
New Asset Preview Pane Lists the Assets in a Selected Segment The ability has been added to view a preview of assets represented in a chart. Clicking on a segment in the chart legend, or on the chart itself, opens the Asset Preview pane. From there, users can create a query from the list of assets, list the assets that match a specific date and search the assets in the list.
Aggregate Data by Hour and Quarter on Timeline Charts
The capability has been added to aggregate data in a chart by hour and quarter when using the Timeline visualization.

This is available on the following charts:
Adapter Segmentation Chart Adapter Segmentation chart now supports charts based on Vulnerabilities and Software queries.
Query Intersection Chart Query Intersection chart now supports charts based on Vulnerabilities and Software queries.
Pivot Chart - Set a Filter on the Measures
Added the option to set a filter on the selected Measures field.
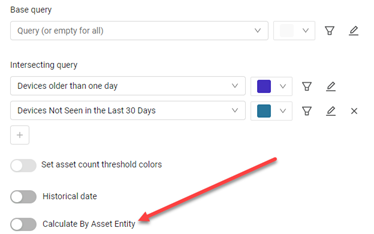
Query Intersection - Calculate by Asset Entity
Ability was added to calculate by asset entity instead of by the aggregated asset fields.
Assets Pages
The following features were added to all assets pages:
Asset Investigation
Tags Supported for Asset Investigation
It is now possible to use Asset Investigation to track changes made to tags on the system. Support of tags in Asset Investigation means that a user can track when a tag is added or removed from an asset, whether this is done manually, or using an Enforcement Action.
Asset Investigation Available for Additional Asset Types
Asset Investigation is now supported for all asset types in the system, Vulnerabilities, Vulnerabilities Repository, Software and Activities.
Filter Asset Investigation by Event Type
- It is now possible to filter Asset Investigation by Event Type: Earliest Value Added, Value Added, Value Removed or Value Changed.
Filtering Asset Investigation by Hours
It is now possible to filter Asset Investigation by a specified last number of hours or for a time range prior to the number of hours, in addition to already available filtering by days, weeks, months, or years.
Field Segmentation Chart
Asset Investigation queries can now be used in the Field Segmentation chart.
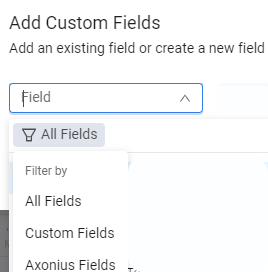
Adding Custom Fields from Asset Pages
When adding custom fields to assets (by selecting Actions> Add Custom Field for selected assets on an Assets page), it is possible to differentiate between adding custom data fields and adding values to existing Axonius fields. Custom fields can now be filtered by type:
-
Axonius Fields - Fields from the adapter.
-
Custom Fields - Tailormade fields created by users.
-
All Fields (default) - Axonius Fields and Custom Fields.
Additional Updates
New Asset Types The following asset types were added:
- Compute Images
- Secrets
Display List Fields as Tables on Asset Profile Page Fields which contain lists can now be displayed as tables on the Asset Profile page.
Data Refinement
- Data refinement is now supported for date fields.
- Data refinement now supports 'earlier than' and 'later than' fields for versions.
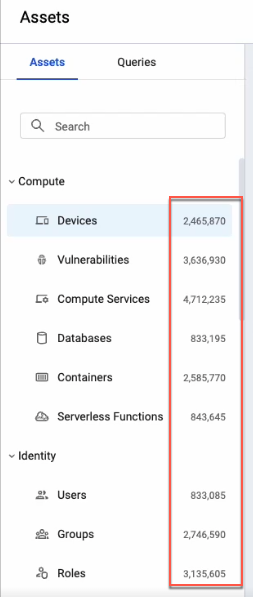
Asset Count Displayed for Each Asset Type On the Assets page, the number of assets of each type is indicated in the Asset tab.
Query Wizard Enhancements
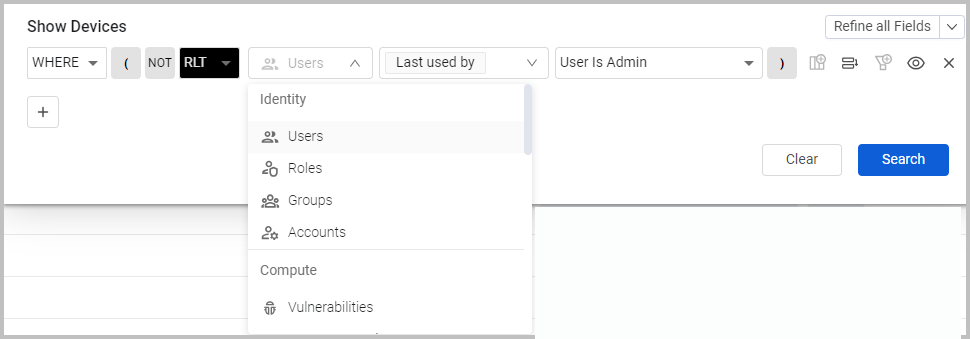
Asset Relationship Queries
It is now possible to create queries in the Query Wizard based on 'Relationship', that is to query on assets that are connected to each other based on the relationship between assets and by using a saved query from a different asset type. This creates powerful cross asset queries, as it is possible to easily create queries on assets connected to each other.
End of Life and End of Support Queries
You can create queries to find End of Life and End of Support for various OS versions using 'Preferred OS: End of Life' or 'OS: End of Life' and 'Preferred OS: End of Support' or 'OS: End of Support' . End of life and End of Support are aggregated values enriched by Axonius. Devices are enriched with data about the End of Life and End of Support for operating systems running on them.
IPv4 Count Operators
-
Count operators were added for IPv4.
Vulnerability Management Module and the Software Management Module:
The following new features and enhancements were added to both the Vulnerability Management Module and the Software Management Module:
Displaying Historical Data on the Vulnerabilities and Software Profile Pages It is now possible to use a date picker to display the data of a specific date on the Vulnerabilities Profile and the Software Profile pages. This enables users to look at various software or vulnerability assets for a specific date without having to go back to the relevant table to adjust the dates.
Edit Columns on Associated Devices Page Edit Columns was added to the Associated Devices Page on the Vulnerabilities Profile and the Software Profile pages to set the columns displayed so that columns related to the devices investigated are displayed.
Unique Devices The total number of unique devices on which Vulnerabilities and Software were found is now shown above the table.
Export CSV Includes Associated Devices When Export CSV is created from the Vulnerabilities or Software page, an option is now available to include the associated devices. When this option is selected, the user can then choose the device fields to include in the CSV file.
Vulnerability Management Module New Features and Enhancements
The following new features and enhancements were added to the Vulnerability Management Module:
Vulnerability Profile page
- A Vulnerability Profile page was now added to the system.
Associated Devices Tab
An Associated Devices tab was added to the Vulnerabilities Profile page. It shows the adapter connections and preferred hostname for the Device from which the Vulnerability was fetched.
Enrich Vulnerabilities from MSRC DB
Axonius now enriches vulnerabilities with data from MSRC via connected adapters. This option is set by default under System Settings>Enrichment.
-
Device related asset entities - refine by condition
-
In Refine data it is now possible to use Device related asset entities - refine by condition for the Device Count column to enable the adjustment of device count for specific device-based Vulnerability fields.
.png)
-
Additional Date Fields Added
- First Seen is an aggregated date field that shows the earliest date that a Vulnerability was seen on the source.
- Last Seen is an aggregated date field that shows the latest date that a Vulnerability was seen on the source.
NVD CVE status A new NVD CVE status column added to the Vulnerabilities page.
Software Management Module New Features and Enhancements
Software Profile Page Updates
-
The Software Profile page now contains all functionality of the regular Asset Profile pages.
-
The Associated Devices tab on the Software Profile pages now shows Installed Software: Software Name and Installed Software: Software Vendor
Export CSV from Software Profile page
- It is now possible to export CSV files from the Software Profile Page. On the Associated Devices tab it is possible to split the CSV file by Installed Software.
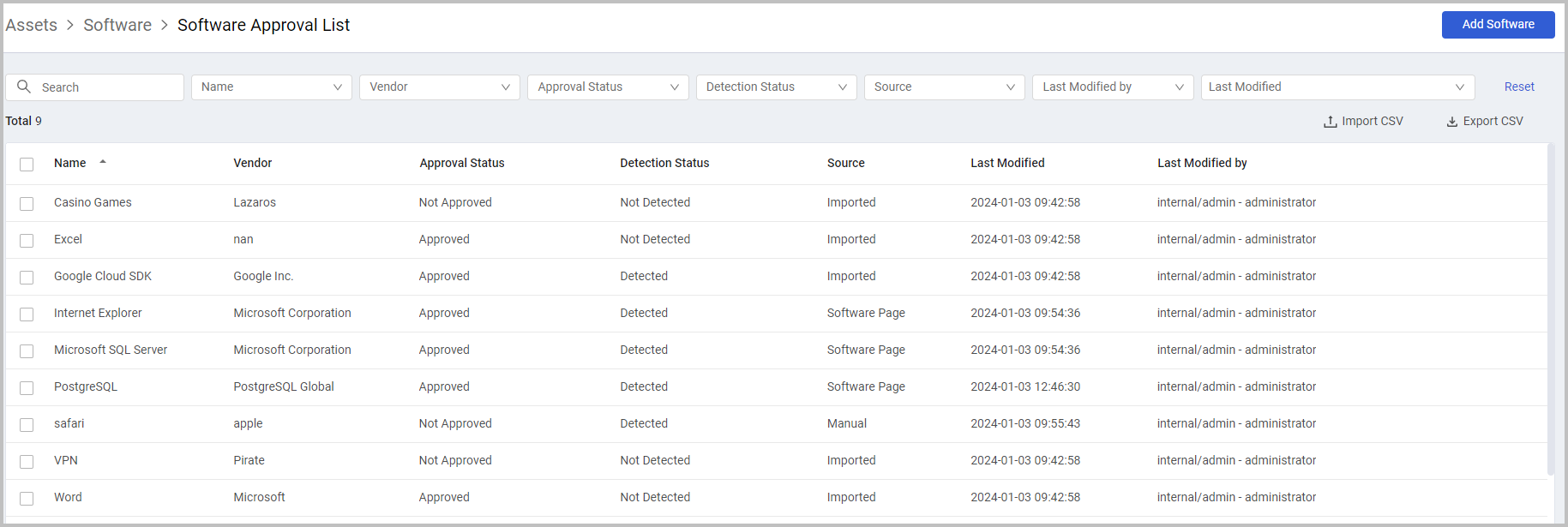
Software Approval List
New Software Approval list enables users to manage a list of Software categorized into Approved/Not-approved. As software is detected it is automatically assigned the Approved/Not-approved status on the Software Page. It is then possible to see this information in queries, charts, etc. and take appropriate action if required. The** Software List** can be created and updated either by:
- Importing a CSV file that contains a list of 'Software' and 'Approval Status'.
- Manually adding Software using the Add Software button.
- Updating the 'Approval Status' field in the Software page using Custom Fields, which is then synchronized with the Approval List.
New Fields Added
-
Preferred Software Name and Preferred Vendor Name fields were added and are displayed by default.
-
Axonius Catalog Enrichment Added
- The Installed Software: Name and Installed Software: Vendor fields are now enriched by Axonius Catalog.
- Software Category is now added as a default field, enriched by Axonius Catalog.
-
Version Count field added
New Version Count field added to the Software Management Module. This shows the number of software versions that a software has. This field can be queried, using <, > and =. Use the Version Count field in software to help identify software that have "older" versions of software on them by identifying software that have software greater than the number of versions back that permitted on the system.
- Software End-of-life and End-of-support Fields Added
The following fields, and filters for these fields were added to the Software Management Page and to the Software Versions tab on the Software Profile page as part of Axonius Catalog enrichment, which is expanded over time:
- End-of-life (date)
- Is End-of-life
- End-of-support (date)
- Is End-of-support
This allows users to track information about Software that reached or are about to reach End-of-life or End-of-support, and take appropriate action if required.
SaaS Management New Features and Enhancements
SaaS Applications - Clickable Counter Fields
Clickable Counter Fields
Users can click the number displayed in SaaS Applications' clickable counter fields to display the lists of items the number represents. For example: Clicking the number displayed in the 'Managed Users by SSO' counter field redirects the user to the Users table, filtered for 'Is Managed by SSO'.
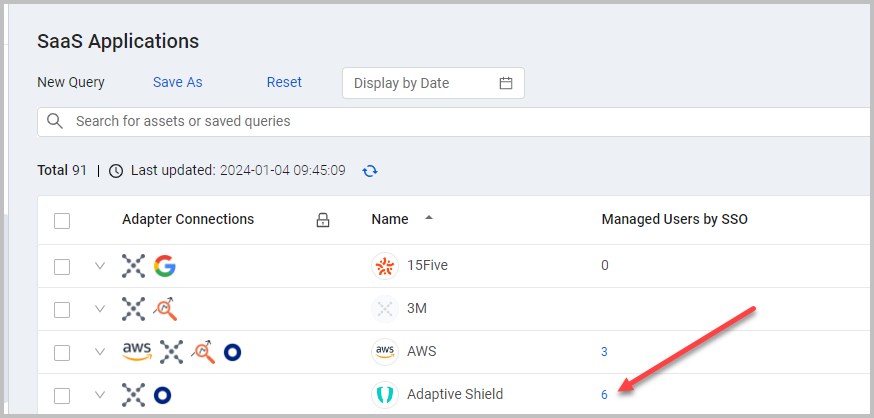
New Clickable Counter Fields The following new clickable counter fields provide an additional level of detailed insights on users, applications, and spending in your SaaS environment:
- Non Operational / Unknown Activity Status
- Last enrichment run
- Admins
- Operational Users
- Suspended Users
- Deleted Users
- Expense Amount
- License Cost
- External Users
- Paid Users
- User Extensions Used by App
- App User Extensions
- Upcoming renewals
- Total Misconfigured Settings
- Total Settings
- Total Accounts
Affiliated Users Clickable Counter Field A New 'Affiliated Users' clickable counter field was added to the SaaS Applications Asset page. This field counts all the users affiliated with a given SaaS application, including users coming from all available sources: the application’s adapter, user extensions, or DNS records.
Associated Licenses Field
A new 'Associated Licenses' User field displays all the licenses associated with a user, providing an easy way to query for licenses a user has across SaaS Applications. This complex field specifies the license names along with their pricing units and costs.
Associated Employees A new Associated Employees field was added to the Users page. This field lists the employees a manager has.
SaaS Application Extensions Module
The following new counter fields in the SaaS Application Extensions module provide an additional level of detailed insights regarding the usage of application extensions in the SaaS environments. When users click the number displayed in these fields, Axonius redirects them to the list of User Extensions that the number represents.
- User Count
- Activity Status - Active Count
- Activity Status - Inactive Count
- Activity Status - Unused Count
- User Activity Status - Active Count
- User Activity Status - Inactive Count
- User Activity Status - Unused Count
- Active Status But Inactive User Count
- Permissions - Is Admin count
- Permissions - Is Identity count
- Permissions - Mail count
- Permissions - Drive count
- Permissions - Calendar count
Tickets
New Tickets created as a result of an Enforcement Action are now created under the Axonius adapter connection. Tickets, which are no longer linked to assets existing in the system, are cleaned and deleted by an automated Ticket Cleanup process.
Asset Graph New Features and Enhancements
The Asset Graph was updated with the following new features and capabilities:
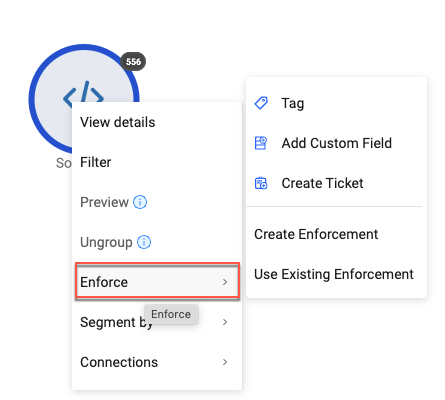
Enforcement Sets, Tags, Custom Fields and Create Tickets from the Asset Graph
- The ability has been added to create new Enforcement Sets based on the results of investigation in the Asset Graph. Existing Enforcement Sets can also be used. It is also possible to assign tags, add custom fields and create tickets directly from the Asset Graph.
Exploring Connections between Assets
- Users can use the new Explore Connections pane to customize what connections to expand. It is also possible to select to show assets that have no connection to the selected asset. This is useful when looking for unmanaged assets and other scenarios where the lack of connection is important.
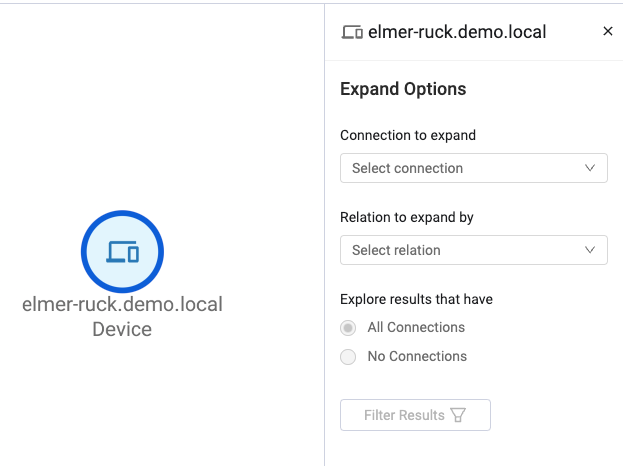
Expand by Single Asset's Adapter Connections
- The ability was added to segment a single asset node to view the node's adapter connections. Then, one or more of the connections can be explored.
Select Multiple Assets in the Asset Graph
-
It is now possible to select multiple nodes or asset groups in the Asset Graph and investigate them as a single entity. It is possible to do all of the following as long as the selected assets/groups are the same asset type:
- Expand connections
- Segment
- Filter
- Ungroup
- Preview
- View details
- View asset profile
- Enforce
-
It is possible to select multiple nodes and group them as you want to create custom asset groups. This helps reduce the clutter in their graph, and custom groups can be acted on as a single entity. For example, it is possible to select all the user nodes that belong to the same department and group them together. Then, they can Filter, Enforce, Segment, or explore further connections to the group with just a few clicks.
Save and Load Graphs
- The steps taken in an Asset Graph can now be saved and loaded at a later time to continue the investigation. This enables users to preserve work, resume their investigation, and share their graphs with others while being aligned with the roles and permission restrictions.
Asset Graph Look and Feel
Organize the Graph with Layouts
- It is now possible to choose between organic or hierarchical representations for personalized data visualization. Tailor the graph layout to match the logic of the node relationships, optimizing clarity and understanding. This enhances user control, improves visual representation, and boosts data comprehension by offering flexible graph layouts catering to individual preferences and specific use cases.
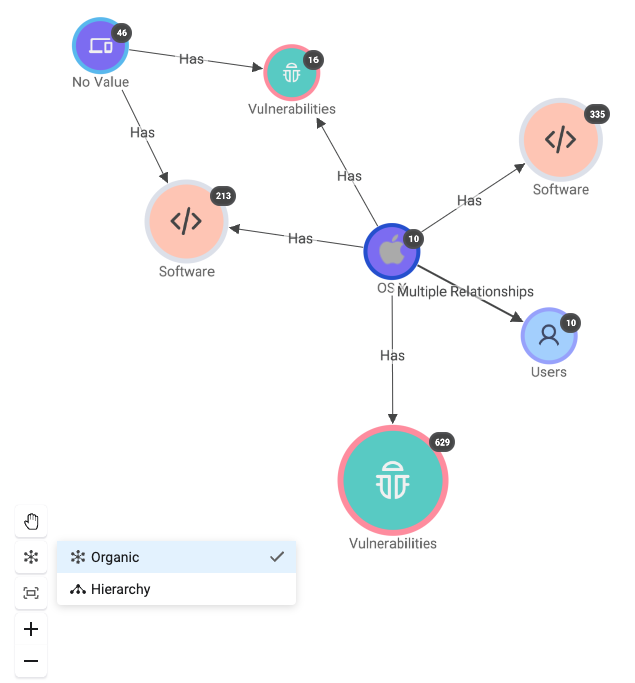
New Asset Graph Node Design and Color Scheme
- The Asset Graph nodes have been redesigned and given a new modern color scheme.
Color Coding of Icons for Asset Types
- The icons for the different asset types shown in the Asset Graph are now color coded.
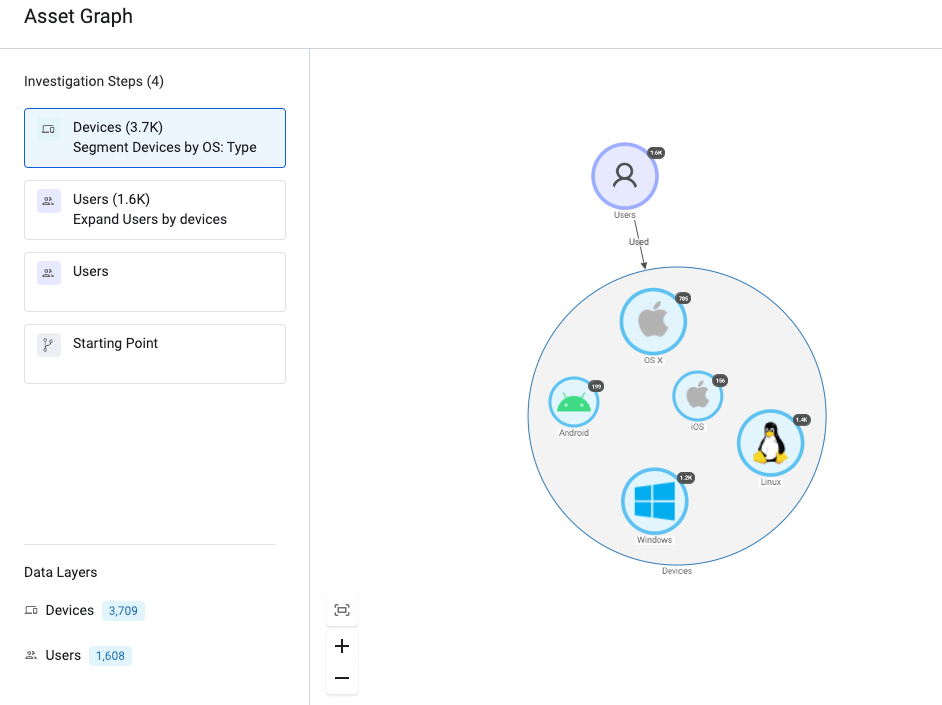
New sidebar
-
A new sidebar in the Asset Graph shows each step in the investigation with the Data Layers at the bottom. Breadcrumbs have been replaced by step tiles making it easier to move between investigation steps.
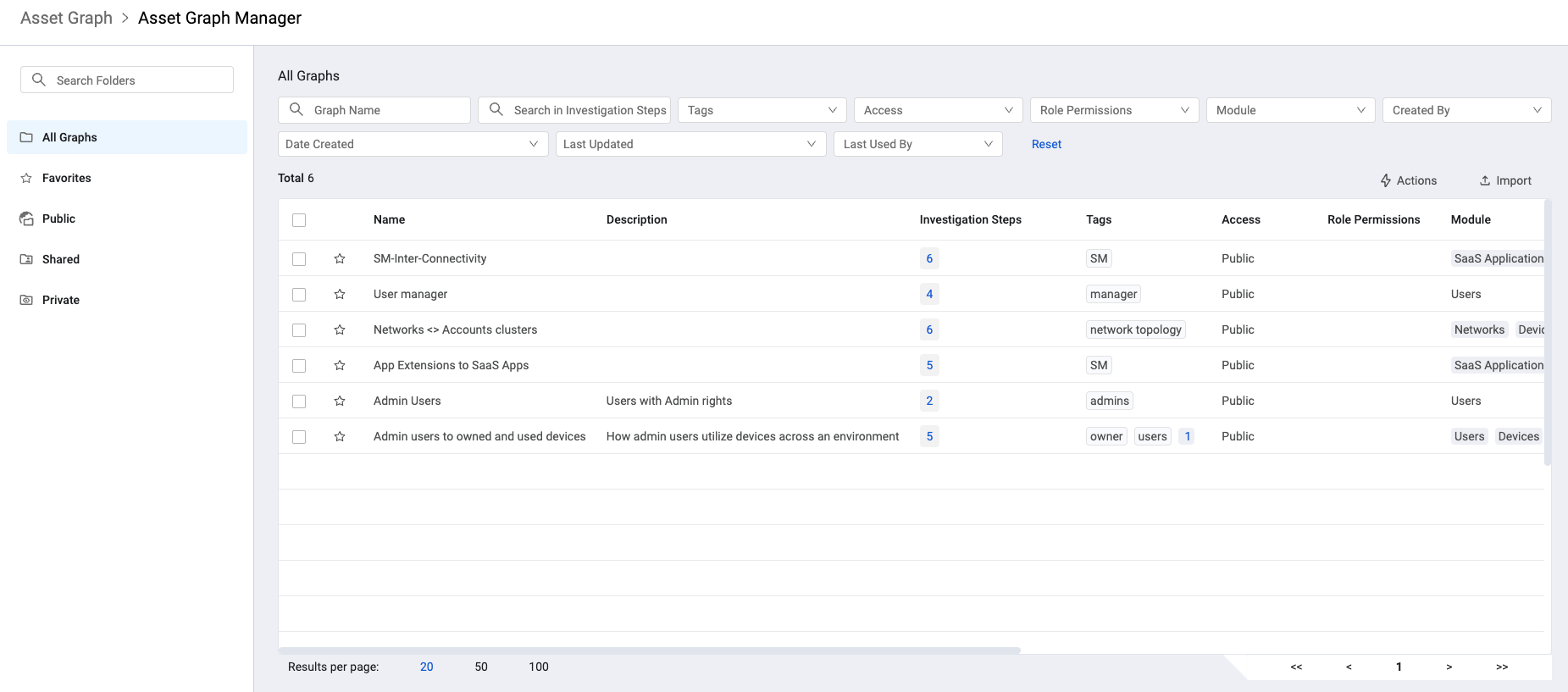
Asset Graph Manager
- The Asset Graph Manager helps users manage all their saved graphs in one place. It is possible to organize graphs into folders, mark them as favorites, search specific graphs based on the steps taken in each one, edit them, and more. Graphs can be accessed more easily and efficiently. A saved graph can be used like pre-defined content to help other users get started with an investigation.
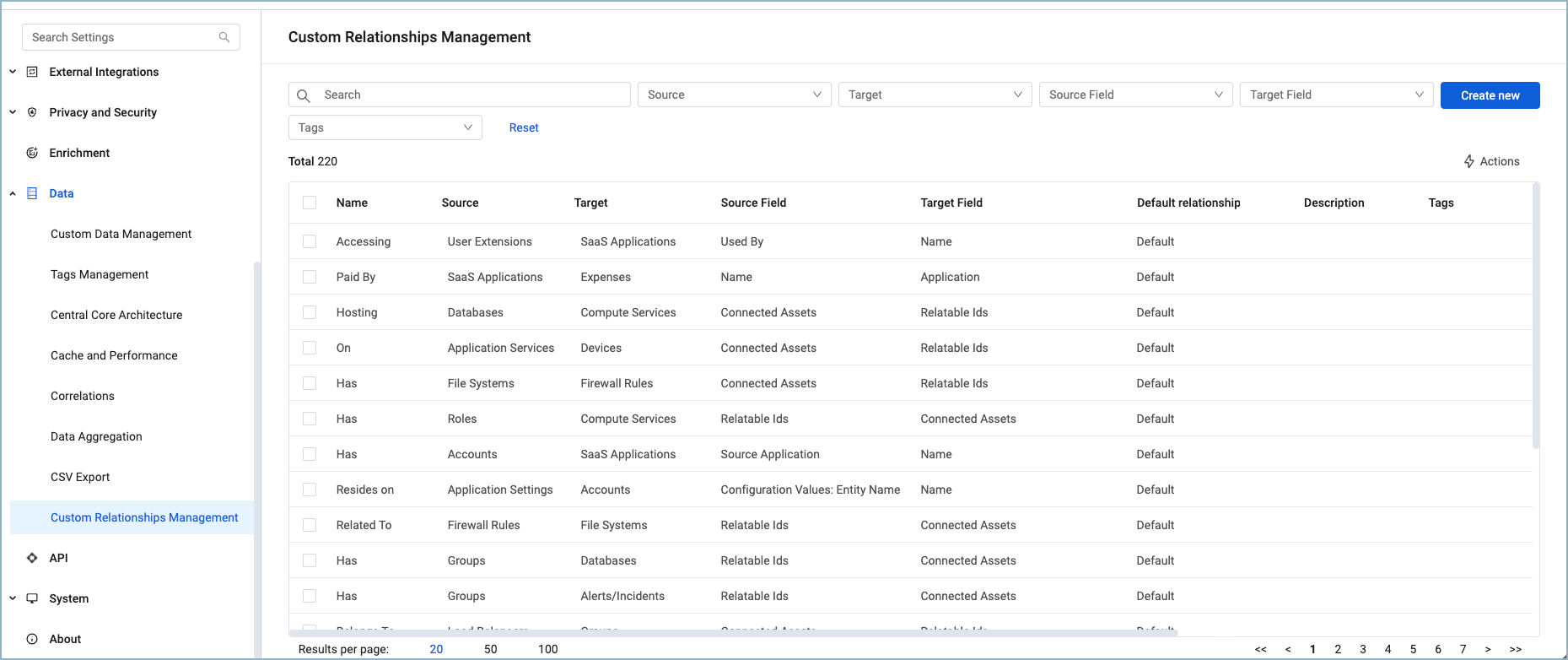
Custom Relationship Management
- It is now possible to create custom relationships between asset types and expand an Asset Graph according to the new relationship. Manage your Custom Relationships in the new Custom Relationships Management page under System Settings.
Query Management New Features and Enhancements
The following new features and enhancements were added to the Queries:
Export/Import Queries
It is now possible to export and import queries using the Axonius User Interface, from the Queries page.
Other Enhancements
Source IP Added to Query History Page The Source IP Address was added to the Query History page. This is the IP address that ran this query.
Query Search On the Queries page the Query search box now enables the user to type all or part of the Query name to make finding a query easier.
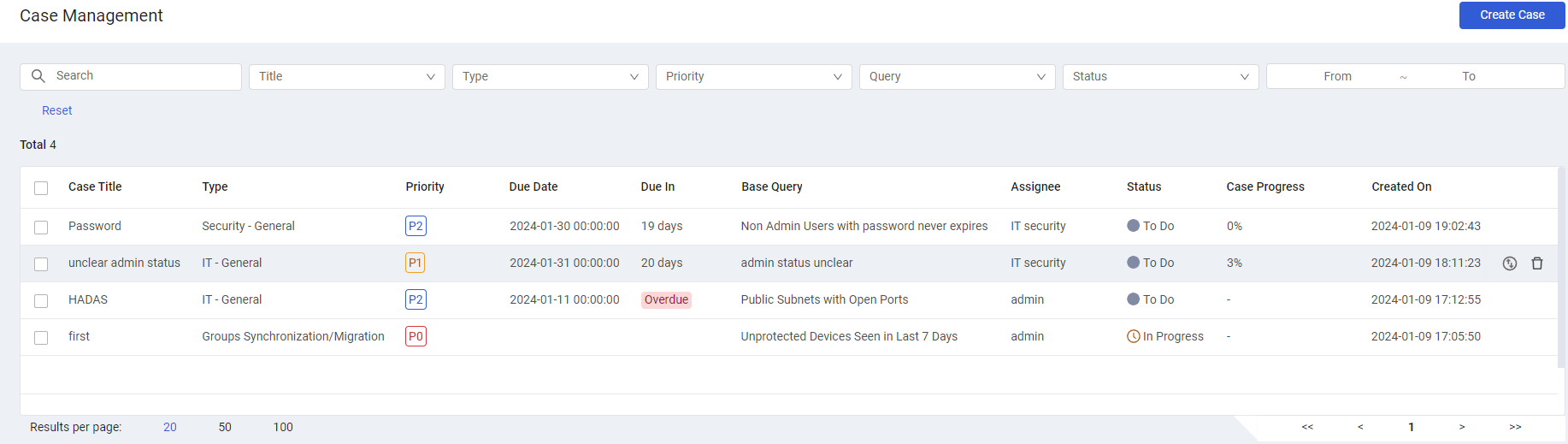
Case Management
When query results indicate a problem or anomaly in the system that requires fixing, it is possible for Axonius users to create a Case indicating the type of issue, assign the Case a priority, assign the case to a user or group of users, link it to an asset query, set a due date for resolving the case, and more. Once a Case is created, it can be managed together with already existing Cases from the new Case Management page, which shows a centralized summary of all cases, and enables opening any case to track its progress and change its status.
These Cases (similar to "in-house tickets") enable users to resolve issues of certain types from within Axonius, instead of opening a ticket in a third-party system.
Data Analytics New Features and Enhancements
The following new features and enhancements were added to Data Analytics:
- A new Export to CSV function was added to export data from the Data Analytics table to a CSV file.
Reports New Features and Enhancements
The following enhancements were added to reports. Adding Individual Dashboard Charts to a Report It is now possible to add individual charts to a report. This is useful when the user wants to add only the specific chart and not the whole dashboard.
New Report Editor
Use the new Report Editor drawer for a more streamlined experience for creating and editing reports.
Adapter Pages and Adapter Interface New Features and Enhancements
The following updates were made to the common functionality across all adapters:
Adapters Page Redesign
A new Adapter Catalog page now presents adapters as a tile view by default. Tiles show adapter name, description and connection status. In addition, supported assets for each adapter are now displayed. Configured adapters are now always shown at the top of the tile view/table. Adapter Profile page was redesigned. Links for advanced settings are now at the left side of the profile page. A new Search was added to the Profile side panel to easily search for any advanced adapter setting, whether general, or specific for that adapter.
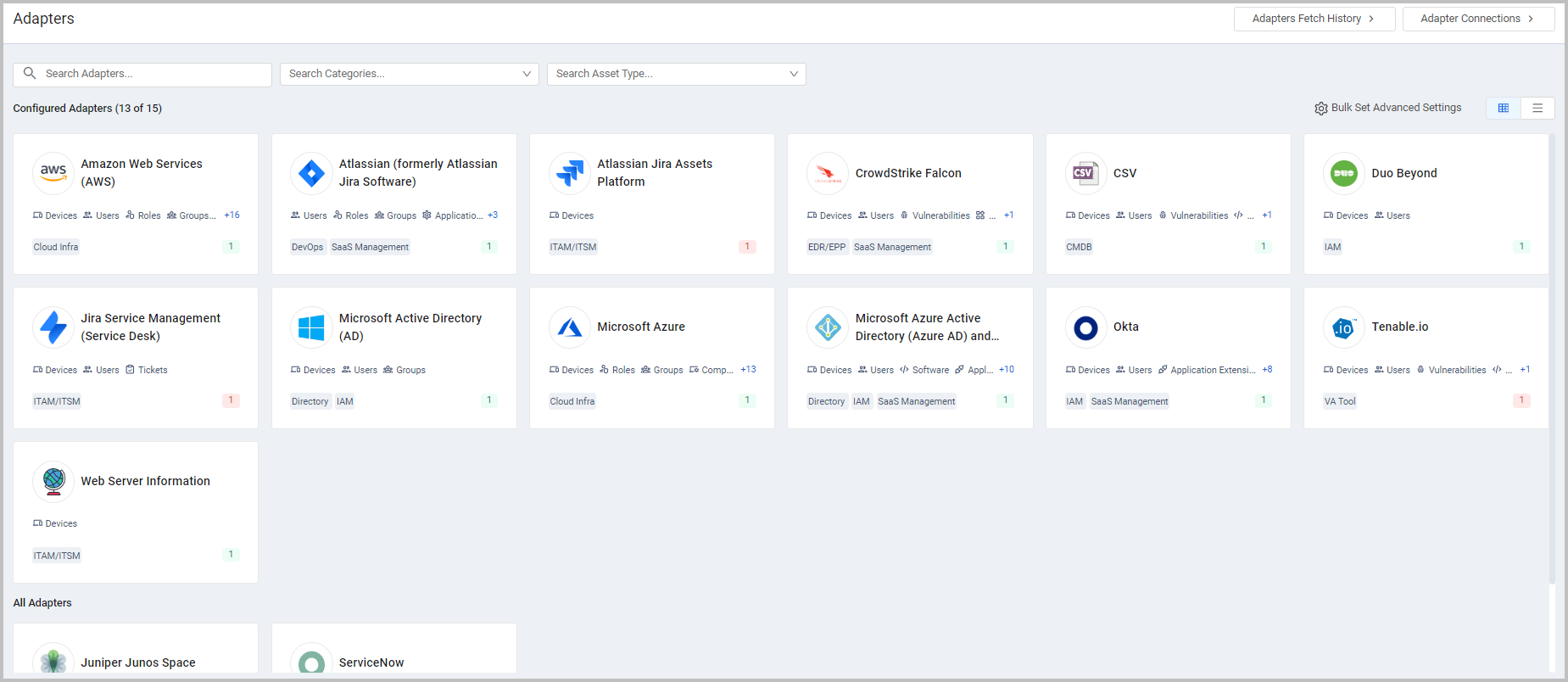
Additional Enhancements
- Manually Stopping and Starting a Discovery Cycle
When a user manually initiates a discovery cycle, the system now asks the user to confirm their action. When a user stops a discovery cycle, the system asks the user to confirm their action.
- Filtering Adapters Fetch History by Hours
It is now possible to filter Adapters Fetch History by a specified last number of hours or for a time range prior to the number of hours, in addition to already available filtering by days, weeks, months, or years.
- On Demand Cleanup for Adapters
It is now possible to run cleanup for a single adapter manually.
- Custom Adapter Value
New Adapter Advanced Setting added called Custom Adapter Value. This is a value that the user defines that will be displayed as part of every entity fetched from the adapter as an added field on the asset called Custom Adapter Value.
Instance Page New Features and Enhancements
Delete Collector Nodes from the Instances Page
- It is now possible to delete collector nodes from the Instances page. Deleting a node, completely removes it from the system and means that it needs to be installed again if required.
Add Collectors Using User Interface
Added the capability to seamlessly choose between the primary node and collector node during installation, and to add a collector node using the User Interface.
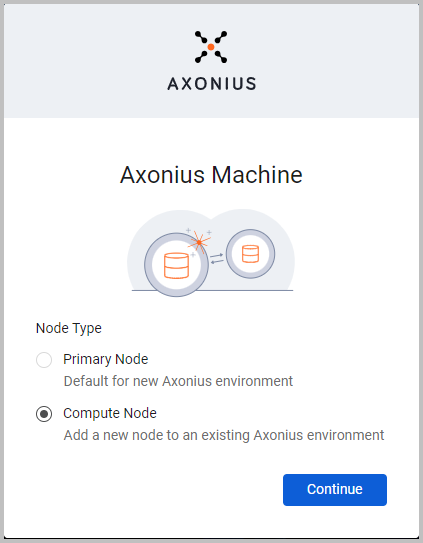
Activity Log New Features and Enhancements
The following new features and enhancements were added to the Activity Logs:
Filtering Activity Logs by Hours
It is now possible to filter Activity Logs by a specified last number of hours or for a time range prior to the number of hours. This is in addition to already available filtering by days, weeks, months, or years.
Administrator Settings New Features and Enhancements
The following updates were made to various Administrator settings:
AI Query Assistant The AI Query Assistant can now use a local version of ChatGPT as well as the Microsoft Azure version, in addition to the standard ChatGPT.
Activity Logs Settings It is now possible to configure in the Activity Logs Settings (accessible from System Settings> System> Activity Logs) whether or not access (read) activities are written to activity logs and displayed in the Activity Logs page.
Service Account Settings For each service account(i.e., accounts that can connect to Axonius only using API), added an option to configure one or more IP address ranges in CIDR notation (accessible from System Settings> User and Role Management> Service Accounts> Add Service Account). This provides extra validation that service accounts are accessed via REST API calls only for known IP addresses.
Role-based Access Control (RBAC)-Connect to Data Scopes in a Streamlined Way
You can now easily move between Data Scopes in a streamlined manner for easier management of data scopes. Click on the avatar and then Connect To. Select a Data Scope from the list.
Azure Authentication Added to Email Settings Azure Authentication (using MS Graph API), was added as an option under 'SMTP Authentication Type' for Email Settings.
Unique IDP Field is Persistent in SAML Configurations When configuring SAML parameters for multiple SSO providers, the IDP field where each provider is named, remains visible but disabled once the configuration is saved.
SAML Configuration Examples Updated The following examples for using SAML for Single Sign-on were updated:
- SAML Based Authentication with Okta
- SAML Based Authentication with Microsoft Entra ID - Includes instructions on how to download the PEM format certificate.
Data Aggregation Settings
Preferred OS fields: Allow the following adapters
-
New Preferred OS fields: Allow the following adapters setting - This settings allows users to enter a comma separated list of adapters to include in the Preferred_OS calculations.
Preferred Fields Device Model
- New Preferred Fields Device Model Setting - This setting allows users to select an option for converting the case of the value of the preferred device model in Axonius.
Add all Extensions to SaaS Applications New option to add all extensions to SaaS applications even when the vendors aren't recognized by Axonius's internal Vendors database.
Enterprise Password Management Settings
New Enterprise Password Managers
-
CyberArk Privilege Cloud Vault Password Manager
-
Thycotic Secret Server was renamed to Delinea Secret Server
-
Tunnel Support Added to the Following Enterprise Password Managers
Added capability to select the tunnel through which to connect to the following Enterprise Password Managers under Enterprise Password Management Settings.
-
Delinea Secret Server(renamed from Thycotic Secret Server).
-
- Namespace is now supported for this vault.
- Role name parameter changed to Role ID
-
Dialog for fetching the password was updated.
General Updates
Link to the Release Notes for the Current Version You can open the release notes of the current version of Axonius using the new link on the Viewing System Information page(the About page) in System Settings. The release notes for the current version are opened in a new browser tab.
Resize Table Columns
It is now possible to resize table columns on asset tables. Columns that contain logos with text fields cannot be resized.
Open Page in New Tab
Open Page in New Tab or Window using Browser Context Menu It is now possible to right click the following items and open a regular browser context menu with the option to open the page in a new tab or a new window:
- Main side panel navigation items
- Findings top panel icon
- Settings icon
Open Page from Link Button in New Tab
Right click any link button at the top of any page to open the linked page in a new tab.
Open Page in New Tab Using Actions Menu
It is now possible to open various pages in Axonius in a new tab using the Actions menu
- Asset Profile pages from the Asset page.
- Enforcement Sets with more than one action.
- Reports
Actions on Table Rows
Actions are now displayed as icons at the right side of the row when the user hovers over any row in the table. When there are four actions or more, on hover, only the first three Actions are displayed; a More Actions icon shows the rest of the available actions. Once one or more rows are selected, the available actions are displayed at the top of the table. Actions are displayed in the same order whether displayed by hovering or by selecting items in the table.
Findings Center New Features and Enhancements
The following new features and enhancements were added to the Findings Center:
Alerts
-
Bulk Marking Alerts as Seen - It is now possible to mark a bulk selection of Finding Center alerts that are in 'Unseen' status as seen (i.e., change their statuses to 'Open') using a single action - Mark as unseen from the Actions menu.
-
A Mute icon was added near muted alerts inside the Alerts drawer - Name field to enable easy differentiation between triggered alerts and muted ones.
-
For Query comparison and Query change over time trigger conditions, the Alerts drawer - Count 1 and Count 2 fields display the number of assets that were compared in the Query comparison or Query change over time condition that triggered the alert.
.png)
Findings Rules
-
Findings Rules Execution - Findings rules are now executed after Enforcement Sets are executed, in the Post-Correlation phase of the Discovery Cycle.
Enforcement Center New Features and Enhancements
The following new features and enhancements were added to the Enforcement Center:
New Enforcement Action Trigger
The Enforcement Set Run History now shows Notify enforcement actions that are initiated by Findings Rules (new Trigger Type) that are preconfigured to send an external notification when triggering an alert.
Defining the Default Enforcement Sets Table View
Users can filter the Enforcement Sets table to show only those Enforcement Sets of interest to them, and save that view as their default table view instead of the system default table view, which displays all Enforcements created by all users in their data scope. Users can revert to their saved default view from any other view, and also reset the filters and restore the unfiltered view as the default view.
Setting Enforcement Set Run Priority
It is now possible to control the order of running Enforcement Sets scheduled to run every Discovery cycle, by assigning them a run priority level. This is especially useful when multiple Enforcement Sets running at the same time are dependent on each other.
Enforcement Action Delay Mechanism
It is possible to delay the execution of a Post, Success, or Failure action(but not a Main action) by a defined amount of time. For example, an Enforcement Action can be configured to send an email to a user about losing access to an application, and trigger a Revoke action a week later.
Dynamic Value Statement Updates
The following updates were made to the Dynamic Value statement functionality:
Dynamic Values Wizard
You can now create Dynamic Value statements using the Wizard. You can also convert from Wizard to Syntax and Syntax to Wizard. The following screen shows the Wizard used to build an All statement.
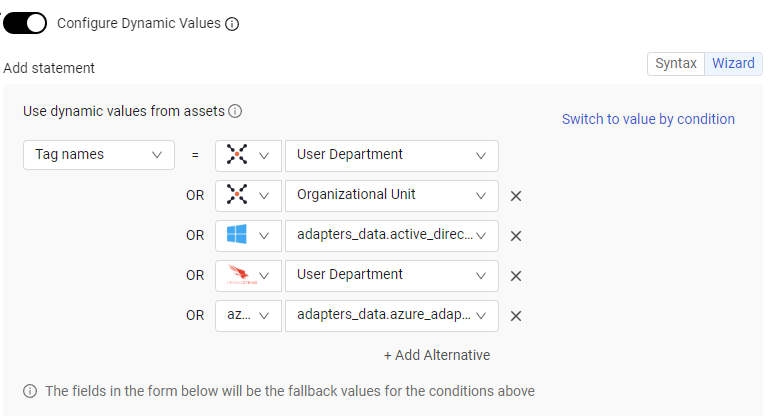
New Functions and Operators
The following functions and operators can now be used in a Dynamic Value statement:
-
average function
- The new average function returns the average of the number values in a list field.
Syntax: average([adapter.arrayfield])
- The new average function returns the average of the number values in a list field.
-
date-format function
- The new date-format function formats a date field using a specified format for the date and time. Syntax: date_format([adapter.field], "format")
-
field_not_exists operator
- The new field_not_exists operator tests whether an adapter field exists. Syntax: field_not_exists
-
in_net operator
- The new in_net operator tests whether the IP addresses in an adapter list field or in an adapter string field are in the specified IP address range. Syntax: in_net (IP address range)
-
not_contains operator
- The new not_contains operator added to Dynamic Value Statements.
-
not_in_net operator
- The new not_in_net operator tests whether the IP addresses in an adapter list field or in an adapter string field are not in the specified IP address range. Syntax: not_in_net (IP address range)
-
now function
- The new now function can be used in a Dynamic Value statement to return the current day's date and time. Syntax: now ()
-
substring function
- The new substring function for string manipulation returns a substring of the field value, beginning from the specified start position in the string until the specified end position in the string. For example: substring('first last', 6, 10) = last Syntax: substring([adapter.field], start_index, end_index)
-
subtract function
- The new subtract function can be used in a Dynamic Value statement to return the result of subtracting item2 from item1. Syntax: subtract(item1, item2)
-
to_lower function
- The new to_lower function for string manipulation converts the string in the adapter field to lowercase. Syntax: to_lower([adapter.field])
-
to_upper function
- The new to_upper function for string manipulation converts the string in the adapter field to uppercase. Syntax: to_upper([adapter.field])
-
unique function
- The new unique function can be used in a Dynamic Value statement to remove all duplicate elements in a list (array) and keep only the unique values. Syntax: unique ([list field]).
- Added the option to apply the unique function on another function. Syntax: unique (nested function)
Enhancements to Axonius Actions
####Manage Custom Enrichment - Enrich Assets with CSV File
- Custom Enrichment is supported for Vulnerabilities and Software.
- It is now possible to validate the syntax of a custom enrichment statement to verify that it is valid before running the enrichment.
- Added the ability to add or remove custom enrichment data contained in a SQL Server table to or from assets.
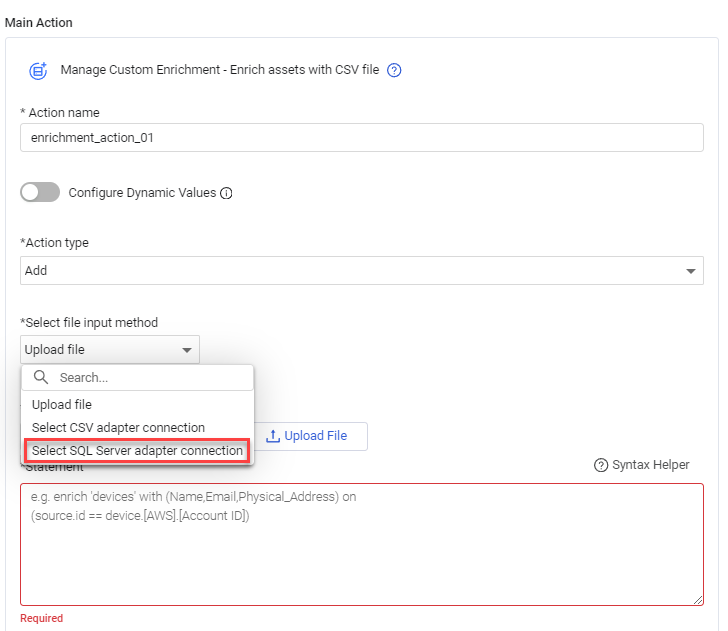
####Axonius - Add Custom Data to Assets
It is possible to add an existing custom field (name and value) to assets by selecting it from a filtered dropdown of existing Custom Fields or Axonius Fields. When selecting a field, its field type and value type are automatically filled in to the action fields.
CSV for Vulnerabilities or Software
-
Enforcement Actions which Send CSV for Vulnerabilities or Software Include Selection of Associated Devices Fields
-
For Enforcement Sets which send CSV files for Vulnerabilities or Software. When Include associated devices is selected, the user can choose the device fields to include in the CSV file.
-
It is now possible to include the associated devices with preferred hostname as a predefined field for each software or vulnerability for relevant Enforcement Actions that create a CSV file.
-
- Added the ability to set a name for the CSV file instead of using the default file name set by Axonius.
- Custom messages can be up to 10000 characters long.
- The email message body can now include data extracted from fields in Queries based on filters (such as Activity Logs and Adapters Fetch History) results.
- Added the option to hide adapter icons in the table.
Cloud Asset Compliance New Features and Enhancements
The following updates were made to Axonius Cloud Asset Compliance:
Support for CIS Microsoft Azure Foundations Benchmark v2.0
Support for the CIS Microsoft Azure Foundations Benchmark v2.0 has been added to the Cloud Asset Compliance Center.
New Adapters
The following new adapters were added to this release:
- 1Password
- 1Password is a password manager providing a place for users to store various passwords, software licenses, and other sensitive information in a virtual vault. (Fetches: Users)
- Aircall
- Aircall is a cloud-based phone system. (Fetches: Users)
- Akeyless
- Akeyless is a SaaS-based solution that provides secrets management and zero-trust access. (Fetches: Devices, Users)
- Alloy
- Alloy Software provides IT Service Management, IT Asset Management, and Network Inventory software. (Fetches: Devices)
- Anomali ThreatStream
- Anomali ThreatStream is a threat intelligence management platform. (Fetches: Devices)
- Asimily Insight
- Asimily provides a vulnerability management platform that scans for devices, vulnerabilities and attack paths, and helps organizations prioritize and manage risk for IoMT, IoT, and laboratory devices. (Fetches: Devices)
- AttackIQ
- AttackIQ is a breach and attack simulation that allows for remote testing and continuous security validation. (Fetches: Devices)
- Autodesk Cloud Platform
- Autodesk Cloud Platform is comprised of the Forma, Fusion and, Flow industry clouds. (Fetches: Devices, Users)
- Backblaze
- Backblaze provides cloud backup and storage services. (Fetches: Devices and Users)
- BGProtect DNS Guard
- BGProtect DNS Guard provides DNS monitoring to help detect changes to DNS records. (Fetches: Devices)
- BGProtect Route Guard
- BGProtect Route Guard provides BGP analysis, route geographical analysis, network ownership, and reachability to detect IP hijacks. (Fetches: Devices)
- BILL
- BILL is a leading provider of cloud-based software that digitizes and automates back-office financial processes. (Fetches: Users, SaaS data)
- Bitwarden
- Bitwarden is an open-source password manager. (Fetches: Users)
- BloxOne Threat Defense
- BloxOne Threat Defense uses the cloud to detect threats while tightly integrating with companies' on-premises ecosystem. (Fetches: Devices)
- Breachsense
- Breachsense monitors the dark web, private hacker forums, and criminal marketplaces to detect data leaks. (Fetches: Devices, Users)
- CDW
- CDW is a multi-brand technology solutions provider. (Fetches: SaaS data)
- CHG Meridian
- CHG-Meridian develops, finances, and manages technology usage.
- CipherTrust Manager(Fetches: Devices)
- Thales CipherTrust Manager is a key management solution for the CipherTrust Data Security Platform. (Fetches: Devices)
- Cisco AppDynamics
- Cisco AppDynamics is an application performance monitoring tool. (Fetches: Devices, Users)
- Cisco CX Cloud
- CX Cloud combines Cisco technology with AI/ML-driven insights, use cases, and contextual learning. (Fetches: Devices)
- Claroty Cloud
- Claroty Cloud is a cyber-physical security (CPS) platform for IoT security. (Fetches: Devices)
- Com Laude
- Com Laude is a domain name registrar, providing domain name management services. (Fetches: Devices, Users)
- Cradlepoint
- Cradlepoint develops cloud-managed wireless edge networking equipment. (Fetches: Devices)
- Cribl
- Cribl is a vendor-agnostic observability pipeline used to collect, reduce, enrich, normalize, and route data. (Fetches: Devices, Users)
- CSI Leasing
- The CSI Adapter tracks hardware contract expiration details. (Fetches: Devices)
- CyberArk Alero
- CyberArk Alero secures remote access to critical systems for employees and third-party vendors. (Fetches: Devices, Users)
- Dell Boomi
- Dell Boomi’s iPaaS platform enables businesses to discover, manage, and orchestrate data while connecting applications, processes, and people. (Fetches: Devices)
- Dell RecoverPoint
- Dell RecoverPoint is a data protection and disaster recovery solution. (Fetches: Devices)
- Docker
- Docker is a platform designed to help developers build, share, and run container applications. (Fetches: Devices)
- Eagle Eye Networks
- Eagle Eye Networks provides cloud-based video surveillance products for physical security and business operations applications. (Fetches: Devices)
- Ekran
- Ekran System is a cybersecurity software vendor delivering a full-cycle insider risk management platform. (Fetches: Users)
- Elastic Defend
- Elastic Defend (formerly Endgame) is a tool for malware prevention, detection, and response. (Fetches: Devices)
- Entrust
- Entrust provides identity, payment, and data security solutions. (Fetches: Devices)
- ESET PROTECT
- ESET is an Endpoint Protection Platform (EPP) for Windows, Mac, Linux, Android, and iOS operating systems. (Fetches: Devices)
- ExtremeCloud IQ Site Engine
- ExtremeCloud IQ Site Engine is an IT operations tool for web-based reporting, network analysis, troubleshooting, and helpdesk. (Fetches: Devices)
- Eyeinspect
- ForeScout eyeInspect is a compliance and threat analysis tool for ICS and OT environments. (Fetches: Devices)
- Feedly
- Feedly is a news aggregator application for various web browsers and mobile devices. (Fetches: Devices)
- FireEye Endpoint Security Logon Tracker
- FireEye Endpoint Security Logon Tracker enables the investigation of lateral movement within Windows enterprise environments. (Fetches: Devices)
- Flexera SVM
- Flexera Security Vulnerability Manager (SVM) is a vulnerability assessment, patch management, and vulnerability intelligence platform. (Fetches: Devices)
- Forcepoint Insider Threat
- Forcepoint Insider Threat is a security analytics tool for searching, detecting and mitigating malicious actors or insider threats. (Fetches: Users)
- Forescout Switch Plugin
- Forescout Switch Plugin is a component of the ForeScout CounterACT Network Module and provides switch to endpoint information as well as VLAN and ACL management capabilities. (Fetches: Devices)
- Google BigQuery
- BigQuery is a serverless, highly-scalable, and cost-effective cloud data warehouse with an in-memory BI Engine and machine learning built in. (Fetches: Devices)
- Greenhouse
- Greenhouse is a talent acquisition software company that offers its suite of tools and services to help businesses with the hiring process. (Fetches: Users, SaaS data)
- HashiCorp Nomad
- HashiCorp Nomad deploys new and legacy applications across multiple datacenters, regions, and clouds. (Fetches: Devices)
- HP Anyware
- HP Anyware supports hybrid work environments allowing users to access their digital workspaces without a VPN. (Fetches: Devices)
- HPE Switches
- HPE Switches provide switch inventory and ARP table information. (Fetches: Devices, ARP table)
- Huawei eSight 21.x
- Huawei eSight is an enterprise operation and maintenance (O&M) platform that provides cross-vendor and cross-product converged management, visualized monitoring, and intelligent analysis for enterprise ICT devices. (Fetches: Devices)
- Huawei OceanStor Dorado V3
- Huawei OceanStor Dorado V3 is an all-flash storage solution. (Fetches: Devices)
- HYCU
- HYCU is a SaaS-based data management product including data protection, migration and disaster recovery. (Fetches: Devices)
- IBM License Metric Tool
- IBM License Metric Tool (ILMT) helps manage license allocation services on supported systems. (Fetches: Devices)
- Intel EMA
- Intel® Endpoint Management Assistant (Intel® EMA) software provides the ability to remotely and securely manage Intel® Active Management Technology (Intel® AMT) devices beyond the firewall, via the cloud, on known Wi-Fi networks. (Fetches: Devices)
- Ivanti for Patch Management
- Ivanti Neurons for Patch Management continuously senses, discovers, and remediates security threats. (Fetches: Devices)
- Ivanti Neurons
- Ivanti Neurons is a unified endpoint management tool that discovers and remediates security threats. (Fetches: Devices)
- Jamf Trust
- Jamf Trust provides enterprise-level security and remote access for mobile devices. (Fetches: Devices)
- Jenkins
- Jenkins is an open-source automation server for continuous integration and delivery, facilitating software building, testing, and deployment. (Fetches: Users)
- Keeper
- Keeper is a password and secrets management solution that helps protect and monitor passwords, secrets, and remote connections. (Fetches: Users)
- Lenel OnGuard
- Lenel OnGuard is an integrated access control and alarm monitoring system. (Fetches: Users)
- ManageEngine Network Configuration Manager
- ManageEngine Network Configuration Manager is multi-vendor network change & configuration management software for switches, routers, and firewalls. (Fetches: Devices, Users)
- ManageEngine PasswordManagerPro
- ManageEngine PasswordManagerPro is a complete solution to control, manage, monitor, and audit the entire life cycle of privileged access. (Fetches: Devices)
- Microsoft Defender External Attack Surface Management (Defender EASM)
- Microsoft Defender External Attack Surface Management discovers and maps the digital attack surface and provides an external view of a company’s online infrastructure. (Fetches: Devices)
- Microsoft Defender for Endpoint for GCC
- Microsoft Defender for Endpoint for GCC helps enterprise government networks prevent, detect, investigate, and respond to advanced threats. (Fetches: Devices, Users)
- Moogsoft
- Moogsoft is an AI-driven observability platform for monitoring solutions. (Fetches: Devices, Users)
- MuleSoft Anypoint Platform
- The MuleSoft Anypoint Platform is a single solution for developing, deploying, securing, and managing APIs and integrations. (Fetches: Users)
- NetWitness NDR
- NetWitness provides real-time network forensics with automated threat detection, response, and analysis solutions. (Fetches: Devices)
- Nexthink Infinity
- Nexthink Infinity provides digital workplace experience management software that provides real-time visibility and insights into application performance. (Fetches: Devices)
- Nutanix Cloud Manager (NCM) Cost Governance
- Nutanix Cloud Manager (NCM) Cost Governance (formerly Beam) provides visibility into cloud spend across multiple cloud environments. (Fetches: Users)
- Opal
- Opal is an access management platform that helps enterprise companies scale least privilege. (Fetches: Users)
- OpenText ZENworks
- OpenText ZENworks is a unified endpoint management and protection solution. (Fetches: Devices)
- Oracle Netsuite
- Oracle Netsuite is a cloud-based ERP solution that provides global business management solutions.
- Ordr
- Ordr provides visibility and security of all connected devices, including unmanaged IoT, OT, and IoMT. (Fetches: Devices)
- Ostendio
- Ostendio is a security, compliance, and risk management platform. (Fetches: Devices)
- Pentera
- Pentera recons and maps web-facing attack surface assets. This includes domains, web interfaces, IPs, networks, and gateways. (Fetches: Devices)
- PeopleSoft
- Oracle PeopleSoft is a suite of applications that provides solutions for human resources, finance, business operations, and more. (Fetches: Users)
- Perimeter 81
- Perimeter 81 is a cloud-based secure access service edge (SASE) platform. (Fetches: Devices, Users)
- Pritunl
- Pritunl is an enterprise distributed OpenVPN, IPsec and WireGuard server. (Fetches: Devices, Users)
- Prey
- Prey is a cross-platform, open source tool that allows you to track and recover your devices. (Fetches: Devices, Users)
- Proofpoint PoD
- Proofpoint on Demand (PoD) Email Security classifies types of email, while detecting and blocking threats. (Fetches: Devices)
- Quadrant
- Quadrant is a Managed Detection and Response solution operating at the intersection of People and Product. (Fetches: Devices)
- Qualys Container Security
- Qualys Container Security provides the ability to discover, track, and secure containers. (Fetches: Devices)
- Qualys PCI Compliance
- Qualys PCI Compliance evaluates compliance with the Payment Card Industry Data Security Standard (PCI DSS). (Fetches: Devices)
- Rackspace Cloud
- Rackspace Cloud is a set of cloud computing products and services for building, hosting, and managing cloud-based infrastructures. (Fetches: Devices)
- RingCentral
- RingCentral provides cloud-based communication and collaboration products and services including phone, messaging, video meetings, and contact center. (Fetches: Devices, Users)
- RiskRecon
- RiskRecon is a cloud-based third-party risk management solution. (Fetches: Users)
- Rundeck
- Rundeck is an open-source tool that helps to define build, deploy and manage automation. (Fetches: Devices, Users)
- SAP Concur 4.x
- SAP Concur provides travel, expense and invoice management. (Fetches: Users)
- SAP S/4HANA Cloud
- SAP S/4HANA Cloud is a modular enterprise resource planning (ERP) software that streamlines various business functions. (Fetches: Users)
- SAP SuccessFactors
- SAP SuccessFactors manages various aspects of HR operations, including recruitment, employee performance, HR analytics, payroll, and learning. (Fetches: Users)
- SecPod SanerNow
- SecPod SanerNow is an integrated platform that helps businesses secure system devices and monitor potential threats across digital assets. (Fetches: Devices)
- SmartSimple
- SmartSimple is a grant management and business process solution. (Fetches: Users)
- SnapComms
- SnapComms is an internal communications software solution. (Fetches: Users)
- Splashtop
- Splashtop is a remote access and remote support tool. (Fetches: Devices, Users)
- StackRox
- StackRox is a container security platform that protects cloud-based applications, detects threats, and manages vulnerabilities, compliance requirements, and configurations. (Fetches: Devices)
- Statseeker
- Statseeker is a network performance monitoring solution. (Fetches: Devices)
- SureMDM
- 42Gears SureMDM is a Unified Endpoint Management (UEM) solution for company-owned and BYOD devices. (Fetches: Devices)
- SUSE Manager
- SUSE Manager is an open-source infrastructure management tool for Linux systems. (Fetches: Devices)
- SymphonyAI Summit
- SymphonyAI Summit is an ITSM solution that provides automation libraries for automating repetitive and manual tasks. (Fetches: Devices)
- Sysdig
- Sysdig is a monitoring, troubleshooting, cost-optimization, and alerting suite for containers, cloud, and Kubernetes environments. (Fetches: Devices, Users)
- Tenable.asm
- Tenable Attack Surface Management (formerly Tenable.asm) continuously maps the internet and discovers connections to internet-facing assets. (Fetches: Devices)
- Tenable.io Scan Export CSV
- Tenable Vulnerability Management CSV File (Formerly Tenable.io) provides the ability to import a Tenable Vulnerability Management (Formerly Tenable.io) scan CSV.
- Tenable Identity Exposure (formerly Tenable.ad)
- Tenable Identity Exposure (formerly Tenable.ad) provides real-time security monitoring for Microsoft Active Directory (AD) infrastructures. (Fetches: Users)
- Teramind
- Teramind is an employee monitoring, user behavior analytics, and insider threat detection solution. (Fetches: Devices, Users)
- Tesma
- Tesma provides a central database for business information and makes it available in real-time. (Fetches: Devices)
- Tines
- Tines is a no-code Security Orchestration Automation & Response (SOAR) solution. (Fetches: Users)
- ThreatLocker
- ThreatLocker is a zero-trust endpoint protection platform. (Fetches: Devices)
- TruffleHog
- TruffleHog is a security tool that scans code repositories for vulnerabilities related to secret keys, such as private encryption keys and passwords. (Fetches: Devices)
- Trustwave
- Trustwave is a managed security services provider focused on managed detection and response. (Fetches: Users)
- United Security Providers
- United Security Providers is a Managed Security Services provider. (Fetches: Devices)
- VMware Tanzu
- The VMware Tanzu for Kubernetes Operations bundle allows platform operators to build, manage, and monitor Kubernetes environments across multiple platforms. (Fetches: Devices)
- Wasabi
- Wasabi is a cloud data storage company focused on high-performance object storage services. (Fetches: Devices, Users)
- watchTowr
- The watchTowr platform provides Continuous Automated Red Teaming (CART) and Attack Surface Management (ASM) to help businesses discover high-impact vulnerabilities. (Fetches: Devices)
- Wiz Reports
- Wiz Reports provides additional data for Wiz assets. (Fetches: Devices, Users)
- Workspace One - Intelligence Report API
- Workspace ONE Intelligence reporting uses a cloud-based report storage system to gather data and create the reports. (Fetches: Devices)
- xAssets
- xAssets provides IT asset management software. (Fetches: Devices)
- Zscaler Client Connector
- Zscaler Client Connector enables secure access to business applications from any device. (Fetches: Devices)
For more details:
-
Explore the entire list of supported and integrated adapters.
New Enforcement Actions
The following Enforcement Actions were added:
-
Azure AD - Role Assignment Actions - Adds or deletes role assignments in Azure AD.
-
Azure AD - Revoke Users Session - Triggers a "revoke session" command on a user account in Azure AD.
-
Asset Panda - Create And Update Assets - Creates and/or updates assets in Asset Panda.
-
Axonius - Delete System Users - Deletes accounts of system users that match the results of the selected query. This requires the Axonius Users adapter to be configured for the current Axonius environment.
-
Axonius Network Discovery - Enrich Asset Data - Enriches the assets with network discovered data, such as hostname, using the IP address for devices without a hostname.
-
Azure AD - Forward Email Rule - Adds a forwarding email address and other related email information for relevant users.
-
BambooHR - Suspend Employee - Deactivates the BambooHR account for assets that match the results of the selected saved query and match the Enforcement Action dynamic statement, if defined, or assets selected on the relevant asset page.
-
BeyondTrust BeyondInsight - Send Block Policy to SCP - Sends a block policy in the form of an XML file for identified software.be
-
CA Service Management - Create Ticket - Creates a ticket in the CA Service Management system.
-
CyberInt - Enrich Asset Data - Enriches each of the assets that are the result of the query with additional data from CyberInt, such as: ports open to the world, address information (country, region, city), ASN, and more.
-
Cylance - Delete Devices - Deletes device assets in Cylance.
-
Enrich Asset Data - EPEAT - Enriches assets with EPEAT information.
-
Exabeam - Update Context Table - Updates and/or creates a context table in Exabeam.
-
Flexera - Uninstall Software - Uninstalls software from devices.
-
Forescout CounterACT Assign Assets to Group Policy - Assigns assets to a Forescout group policy.
-
Github - Remove User Extensions - Removes GitHub user extensions.
-
GSuite - Change Users OU - Moves a user account into an OU in GSuite.
-
GSuite - Remove Users From Group - Removes users from a GSuite group.
-
GSuite - Reset Users Logon Cookies - Resets user logon cookies for GSuite.
-
GSuite - Role Assignments Actions - Adds or deletes role assignments in GSuite.
-
GSuite - Send Message - Sends a message via an adapter connection or a webhook.
-
Jira Service Management - Update Tickets - Updates the relevant tickets for assets matching the Enforcement Set query. For example, if the action is triggered on asset=Users, the ticket updates tickets linked to each user.
-
Jira Software - Create User - Creates a user in Atlassian (formerly Jira Software).
-
Jira Software - Delete User - Deletes a user in Atlassian (formerly Jira Software).
-
JumpCloud - Run Command - Runs JumpCloud commands.
-
Kandji - Update Device Blueprint - Updates device blueprints in Kandji.
-
ManageEngine ServiceDesk Plus - Create Request - Creates one ManageEngine ServiceDesk Plus request that includes all relevant assets.
-
ManageEngine ServiceDesk Plus - Create Request per Asset - Creates a ManageEngine ServiceDesk Plus request for each asset individually.
-
Offboard Assets - Microsoft Defender ATP - Offboards assets from Microsoft Defender ATP.
-
Microsoft Teams - Send Direct Message to Assets - Sends direct messages in Microsoft Teams.
-
Onelogin - Logout User - Logs a user out of a OneLogin session.
-
Onelogin - Lock User - Locks a user out of a OneLogin session.
-
Onelogin - Set a New Password for User - Creates a password for a user in OneLogin.
-
OpenCTI - Enrich Asset Data - Enriches OpenCTI assets.
-
Qualys - Add IP Addresses to Asset Group - Adds IP addresses to assets within asset groups.
-
Rapid7 - Remove IP Addresses from Asset - Removes IP addresses from Rapid7 assets.
-
Sailpoint - Disable Users - Disables users in Sailpoint.
-
Salesforce - Delete Extensions - Deletes an extension in Salesforce.
-
CSV - Send to SFTP - Sends a CSV file including the relevant assets via SFTP.
-
ServiceNow - Disable or Remove Assets - Suspends or removes ServiceNow assets.
-
Set Unit Count - Gradient - Passes to Gradient the number of devices that have been seen by the selected adapter / adapter connection and sets the unit count in Gradient, which tracks customer billing data.
-
Slack - Send Direct Message to Assets - Sends a direct message to Assets.
-
Slack - Suspend User - Deactivates a user's Slack account.
-
SymphonyAI Summit - Create or Update Assets - Creates and/or updates SymphonyAI Summit assets.
-
Authorize Asset - Tailscale - Authorizes assets in Tailscale.
-
Tenable.io - Add IP Addresses to Scan - Adds IP addresses to an existing Tenable.io scan.
-
Tenable.io - Delete Asset - Deletes an asset from Tenable.io.
-
Thycotic - Suspend User - Suspends a user in Thycotic Secret Server.
-
Update ServiceNow Tickets - Updates the relevant tickets for assets matching the Enforcement Set query.
-
Update Zendesk Tickets - Updates existing Zendesk tickets.
-
WMI - Forward Email Rule - Sets or unsets email forwarding.
-
Zendesk - Create Ticket Per Entity - Creates a ticket for each asset that matches the query parameters.
-
Zoom - Send Message - Sends a message in Zoom Team Chat.
For more details:
- See the complete Enforcement Action Library.
Updated 4 months ago
