Discovery Cycle
Axonius runs a periodic automatic global discovery cycle that consists of several phases to pull and correlate the data from all adapters. The global discovery cycle schedule (for example, every 12 hours) is determined based on the system Lifecycle Settings.
You can also manually initiate a new global discovery cycle by clicking Discover Now on the top right corner of any page. The Discover Now button is only visible once one adapter is connected.
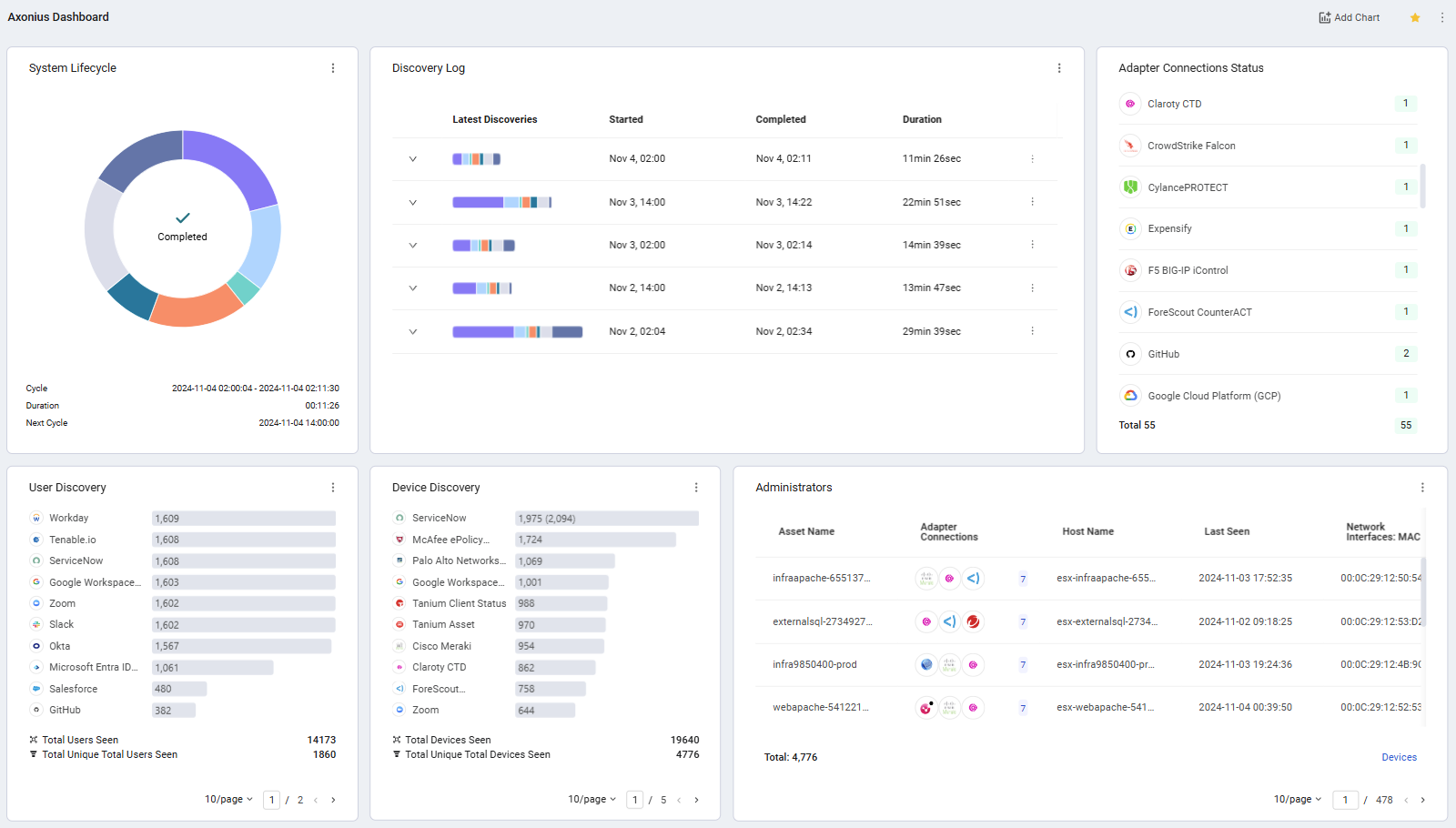
The latest global discovery cycle status is displayed in the System Lifecycle chart. The chart also displays the following details:
- The number of hours until the next automatic discovery cycle starts.
- The last discovery cycle's start and end timestamps.
- The duration of the cycle.
Note:
Axonius also lets you configure individual discovery cycles for specific adapters and for specific adapter connections.
Adapter custom cycle – This cycle includes only the following phases:
- Fetch Assets / Scanner Assets
- Clean
- Correlation
Connection custom cycle – This cycle includes only the following phases:
- Fetch Assets / Scanner Assets
For more details, see Adapter Discovery Configuration.
Global Discovery Cycle Phases
The global discovery cycle (automatic and manual) consists of several sequenced phases:
- Fetch Adapter Assets
- Data is pulled from all adapter connections, except for adapters of vulnerability assessment tools, and the Axonius adapter used for tickets.
Note
Adapters configured with a custom cycle are skipped.
Adapter connections configured with a custom cycle are skipped.
- Fetch Scanner Assets
- Data is pulled from all adapter connections of vulnerability assessment tools.
- Devices that have the same IP address and have no other unique identifier (no hostname, MAC address, etc.) are correlated together.
Note
Adapters configured with a custom cycle are skipped.
Adapter connections configured with a custom cycle are skipped.
- Clean Assets
- "Old" devices and other asset entities (excluding tickets) are cleaned and deleted. The definition of "old" asset entity may be different for each adapter, and determined based on the following adapter advanced setting:
- Then, "old" users asset entities are cleaned and deleted. The definition of "old" asset entity may be different for each adapter, and determined based on the following adapter advanced setting:
Note
- Tickets are linked to an Axonius pseudo adapter and not to the adapter connections of their linked assets.
- Adapters configured with a custom cycle are skipped.
- You can also run adapter cleanup manually for a single adapter.
- Clean Tickets
- Cleans tickets that have been opened for assets that are no longer seen by their vendor adapter. This means that tickets, which have no links to assets existing in the system, are cleaned and deleted.
-
Pre-Correlation
- ‘Equals’ values list is calculated.
- Cloud Asset Compliance rules are implemented, if enabled.
-
Correlation
- The correlation engine runs and correlates relevant assets together.
-
Post-Correlation
- User-device associations are created.
- Last Used Users field is populated on devices with the user names associated with each device.
- Last Used Users [XXXX] fields (for example, Last Used Users Email, Last Used Users Departments, and more) are populated based on the user fields and data of the Last Used Users associated with each device.
- User assets are enriched with 'Associated Devices'.
- Later you can query devices based on the associated user name or user department.
- Preferred fields are recalculated.
- Custom enrichment runs.
- Enforcement sets scheduled to run at the end of each discovery cycle are executed.
- Enforcement sets whose scheduled start times fell on the time that the discovery cycle was already running, but have the Wait until cycle ends option enabled, are executed now.
- Field Mapping Enforcement sets are triggered in the Post-Correlation phase of the Discovery Cycle after all other Enforcement sets runs have concluded, but continue running asynchronously outside the Discovery Cycle. This enables the Discovery Cycle to proceed to the next phase before the Field Mapping Enforcement set runs are completed.
- Findings rules are run.
- Reports are generated.
- User-device associations are created.
-
Save Historical
- Historical collected data is saved, based on the Historical Snapshot Scheduling Settings.
- Historical data can be used in the dashboard, in the asset pages, and in the Users page to show insights on historical data.
Note
- If historical snapshot data has been configured to be saved at a specific time and not at the end of a discovery cycle, this phase is skipped.
- Vulnerabilities details are enriched from the vulnerability enrichments such as NIST National Vulnerabilities Database (NVD), CISA, EPSS (Exploit Prediction Scoring System) etc.
Updated 4 months ago
