Zimperium
Zimperium Mobile Threat Defense is an on‑device security engine that detects and prevents mobile threats across device, network, phishing and app attacks using machine‑learning.
Assets Types Fetched
This adapter fetches the following types of assets:
Devices |
Aggregated Security Findings |
Users |
Roles |
SaaS Applications |
Alerts/Incidents
Before You Begin
Authentication Methods
- API V1 uses and API Key
- API V2 authentication is based on JSON Web Tokens (JWTs), which are generated using a Client ID and Client Secret.
Required Permissions
The API key must be associated with a Role that grants the necessary View scopes for all required asset types.
- Users: users:view
- Roles: roles:view
- Devices: devices:view
- Vulnerabilities (Aggregated Security Findings): os_risk:view
- Alerts/Incidents: threats:view
APIs
Axonius uses the Zimperium zIPS API.
Supported From Version
Supported from Axonius version 4.7
Connection Parameters
To connect the adapter in Axonius, provide the following parameters.
Required Parameters
-
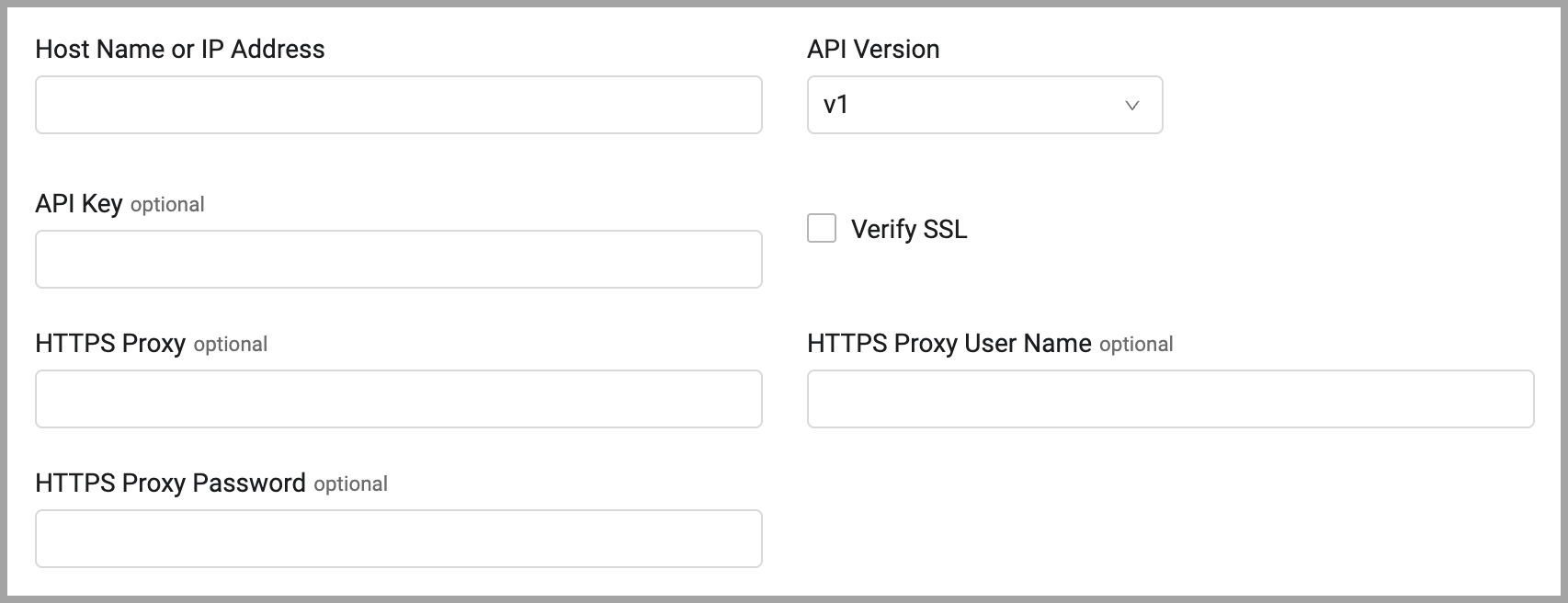
Host Name or IP Address - The hostname or IP address of the Zimperium server.
-
API Version - Select the API version you are using and enter the relevant parameters.
- API Key- An API Key associated with a user account that has permissions to fetch assets. To obtain the API Key: Contact the Zimperium Customer Success team and request an API Key value to access the API requests.
Optional Parameters
-
Verify SSL - Select whether to verify the SSL certificate of the server against the CA database inside of Axonius. For more details, see SSL Trust & CA Settings.
-
HTTPS Proxy (optional) - Connect the adapter to a proxy instead of directly connecting it to the domain.
-
HTTPS Proxy User Name (optional) - The user name to use when connecting to the value supplied in Host Name or IP Address via the value supplied in HTTPS Proxy.
-
HTTPS Proxy Password (optional) - The password to use when connecting to the server using the HTTPS Proxy.
To learn more about common adapter connection parameters and buttons, see Adding a New Adapter Connection.
Advanced Settings
Note
Advanced settings can either apply for all connections for this adapter, or you can set different advanced settings and/or different scheduling for a specific connection, refer to Advanced Configuration for Adapters.
- Fetch device vulnerabilities - Select whether to fetch vulnerabilities on devices.
- Fetch Roles (for API V2) - Fetch SecurityRoles from the roles endpoint.
- Fetch Incidents (Threats) (for API V2) - Fetch incidents from the threats endpoint.
- Fetch Incidents From Last X Days (default 30) (for API V2) - Fetch incidents from the previous X days.
Note
To learn more about Adapter Configuration tab advanced settings, see Adapter Advanced Settings.
Updated 19 days ago
