CyberArk Privilege Cloud
CyberArk Privilege Cloud is a privileged access management (PAM) solution for securing, managing, and monitoring privileged accounts.
CyberArk Privilege Cloud is a privileged access management (PAM) solution for securing, managing, and monitoring privileged accounts.
Asset Types Fetched
- Users, Roles, Groups, Secrets, Application Resources
Before You Begin
Ports
- TCP port 443
Authentication Method
The adapter supports the following authentication methods:
- CyberArk, Windows, LDAP, RADIUS, SAML, or ISPSS
APIs
Axonius uses the CyberArk REST APIs.
Required Permissions
The user account used for the adapter connection:
- Must have Audit permissions.
- Must be a member of a Safe in a CyberArk Vault.
- Must have List Accounts permissions in the Safe.
In addition, each authentication method requires specific permissions. See Connecting the Adapter in Axonius for more information.
To assign the required permission to your Axonius user:
- Go to CyberArk -> Identity Administration -> Core Services -> Roles.
- Select Create a new Role.
- Select Administrative Rights and click Add.
- Add the following permission: Read Only System Administration.
- Click Save.
- Assign the new Role to the Axonius user.
Supported From Version
Supported from Axonius version 6.1
Connecting the Adapter in Axonius
To connect the adapter in Axonius, provide the following parameters:
Required Parameters - General
- Host Name or IP Address - The hostname or IP address of the CyberArk Privilege Cloud server.
- Authentication Method - Select the authentication method you want to use. The required parameters and permissions vary depending on the selected authentication.
Parameters and Requirements per Authentication Method
These methods are typically used for direct authentication to the CyberArk Privilege Cloud server.
Requirements
- Ensure the user account has the Audit, Safe membership, and List Accounts permissions.
- The selected network protocols must be properly configured for the CyberArk server.
Parameters
- User Name and Password - The credentials for a user account that has the required permissions to fetch assets.
- For more information on creating accounts within CyberArk Privilege Cloud, see Add and Manage Users.
- For more information about logging in, see CyberArk, LDAP, RADIUS.
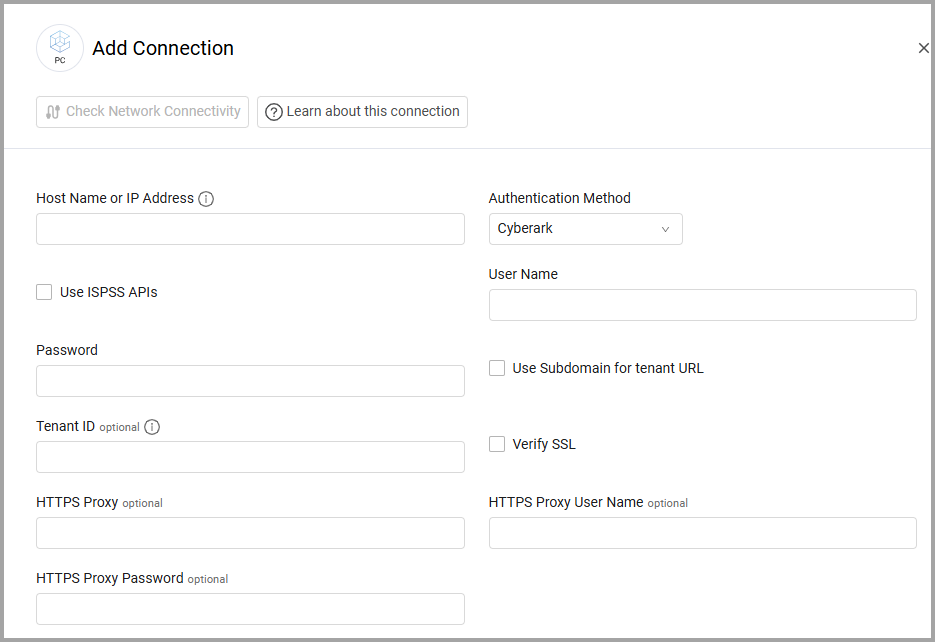
Optional Parameters
- Verify SSL - Select whether to verify the SSL certificate of the server against the CA database inside of Axonius. For more details, see SSL Trust & CA Settings.
- HTTPS Proxy - Connect the adapter to a proxy instead of directly connecting it to the domain.
- HTTPS Proxy User Name - The user name to use when connecting to the value supplied in Host Name or IP Address via the value supplied in HTTPS Proxy.
- HTTPS Proxy Password - The password to use when connecting to the server using the HTTPS Proxy.
To learn more about common adapter connection parameters and buttons, see Adding a New Adapter Connection.
Advanced Settings
Note
Advanced settings can either apply to all connections for this adapter, or to a specific connection. Refer to Advanced Configuration for Adapters.
- Endpoints Config - Click on
>to open the following settings for configurable endpoints:- Enrich Users with User Roles - Enable this option to enrich the Users endpoint with User Roles. This setting is relevant only when using the ISPSS authentication method.
- Enrich Users with Safe Members - Enable this option to enrich the Users endpoint with Safe Members.
- Fetch Users of sub type account from Accounts - Enable this option to fetch users of the subtype 'account' from the Accounts endpoint. When enabled, the following settings can be configured:
- Enrich Accounts with Account Activities - Enable this option to enrich the Accounts endpoint with Account Activities.
- Enrich Accounts with Account Extended Data - Enable this option to enrich the Accounts endpoint with Account Extended Data.
- Fetch Users of sub type users_from_safe_members from Users From Safe Members - Enable this option to fetch users of the subtype 'users from safe members' from the Users From Safe Members endpoint. This setting is relevant only when using the ISPSS authentication method. When enabled, the following settings can be configured:
- Enrich Users From Safe Members with Safe Members - Enable this option to enrich the Users From Safe Members endpoint with Safe Members.
- Enrich Users From Safe Members with Role Members - Enable this option to enrich the Users From Safe Members endpoint with Role Members.
- Fetch Users of sub type users_from_role_members from Users From Role Members - Enable this option to fetch users of the subtype 'users from role members' from the Users From Role Members endpoint. This setting is relevant only when using the ISPSS authentication method. When enabled, the following settings can be configured:
- Enrich Users From Role Members with Safe Members - Enable this option to enrich the Users From Role Members endpoint with Safe Members.
- Enrich Users From Role Members with Role Members - Enable this option to enrich the Users From Role Members endpoint with Role Members.
- Fetch Groups from Groups - Enable this option to fetch groups from the Groups endpoint. When enabled, the following settings can be configured:
- Enrich Groups with Safe Members - Enable this option to enrich the Groups endpoint with Safe Members.
- Fetch Secrets from Safes - Enable this option to fetch secrets from the Safes endpoint. When enabled, the following settings can be configured:
- Enrich Safes with Safe Members - Enable this option to add safe members data to Safes.
- Fetch ApplicationResources of sub type safe from Safes - Enable this option to fetch application resources of the subtype 'safe' from the Safes endpoint. When enabled, the following settings can be configured:
- Enrich Safes with Safe Members - Enable this option to add safe members data to Safes.
- Fetch ApplicationResources of sub type account from Accounts - Enable this option to fetch application resources of the subtype 'account' from the Accounts endpoint.
- Fetch SecurityRoles from Built-in Roles - Enable this option to fetch security roles from the Built-in Roles endpoint. This setting is relevant only when using the ISPSS authentication method. When enabled, the following settings can be configured:
- Enrich Built-in Roles with Role Members - Enable this option to enrich the Built-in Roles endpoint with Role Members.
- Enrich Built-in Roles with Safe Members - Enable this option to enrich the Built-in Roles endpoint with Safe Members.
- Parser Config - Click on
>to open the following settings for configurable endpoints:- Parse the Domain value as an associated device - Select this option to parse the domain value as an associated device.
- Account Domain Source - Choose the source for the account domain parsing.
Note
To learn more about Adapter Configuration tab advanced settings, see Adapter Advanced Settings.
Updated 12 days ago
