Darktrace
Darktrace Immune System protects workforce and data from sophisticated attackers, by detecting, investigating and responding to cyber-threats.
Types of Assets Fetched
This adapter fetches the following types of assets:
- Devices
Parameters
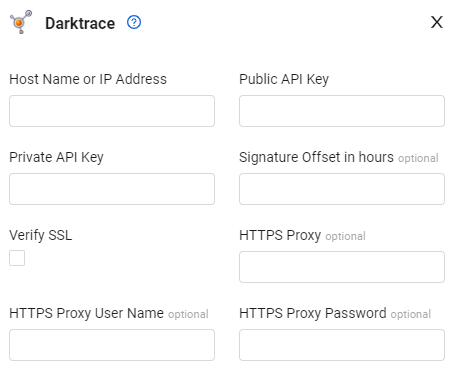
- Host Name or IP Address (required) - The hostname or IP address of the Darktrace server.
- Public API Key (required) - A public API Key associated with a user account that has the Required Permissions to fetch assets.
- Private API Key (required) - A private API Key associated with a user account that has the Required Permissions to fetch assets.
- Signature Offset in hours (optional) - Increase or decrease the number of hours to offset the timestamp of the Axonius client.
- If the client timestamp is less than the server timestamp, increase the number of hours to synchronize the values. For example, if the server timestamp is 16:00 and the client timestamp is 14:00, enter
2to synchronize the timestamp values. - If the client timestamp is more than the server timestamp, decrease the number of hours to synchronize the values. For example, if the server timestamp is 14:00 and the client timestamp is 16:00, enter
-2to synchronize the timestamp values.
- If the client timestamp is less than the server timestamp, increase the number of hours to synchronize the values. For example, if the server timestamp is 16:00 and the client timestamp is 14:00, enter
- Verify SSL - Select to verify the SSL certificate offered by the value supplied in Host Name or IP Address. For more details, see SSL Trust & CA Settings.
- HTTPS Proxy (optional) - A proxy to use when connecting to the value supplied in Host Name or IP Address.
- HTTPS Proxy User Name (optional) - The user name to use when connecting to the value supplied in Host Name or IP Address via the value supplied in HTTPS Proxy.
- HTTPS Proxy Password (optional) - The password to use when connecting to the value supplied in Host Name or IP Address via the value supplied in HTTPS Proxy.
To learn more about common adapter connection parameters and buttons, see Adding a New Adapter Connection.
Advanced Settings
Note
Advanced settings can either apply for all connections for this adapter, or you can set different advanced settings and/or different scheduling for a specific connection. Refer to Advanced Configuration for Adapters.
- Fetch model breaches for devices - Select whether to fetch an additional layer of data, the list of model breaches that run on each device.
- When enabled, all connections for this adapter also fetch model breaches for each device.
- When disabled, all connections for this adapter do not fetch model breaches for each device.
- Fetch only devices that have a MAC Address and Host Name - Select to only fetch devices with a MAC address and hostname. If cleared, all connections for this adapter will fetch devices even if they don't have a MAC address or hostname.
- Don't fetch devices without hostname - Select to exclude fetching devices without a hostname. If cleared, all connections for this adapter will fetch devices even if they don't have a hostname.
- Device types to fetch - Select the device types to fetch from the drop-down.
Note
To learn more about Adapter Configuration tab advanced settings, see Adapter Advanced Settings.
APIs
Axonius uses the Darktrace API.
Required Permissions
The value supplied in Public API Key and Private API Key must be associated with credentials that have API Access permissions.
Creating an Account with API Access Permissions
- Log in to the Darktrace Web app by using an Admin account.
- From the left menu, select Admin → Permissions Admin.
- Click Account Create to create an account for API integration.
- Activate the newly created account by clicking the Flags (
</>) icon on the right. A green icon confirms that the API access is enabled. - Acquire the public and private tokens required for the adapter setup, as detailed in the next section.
Acquiring the API Token Pair (Public and Private Token)
- Log in to Darktrace.
- From the left menu, select Admin → System Config.
- From the Settings dialog in the left, select API Token. The public token is displayed on the right side. To view the private token, click Remove.
Updated 4 months ago
