Security Findings Page
Use the Security Findings Assets Page to view specific CVEs and other vulnerabilities detected on specific assets. Learn about default fields and how to track remediation.
Use the Security Findings Assets Page to view specific CVEs and other vulnerabilities detected on specific assets.
Click the Assets icon and from the left pane, and under the Exposures category, select Security Findings.
Security Findings Assets Page
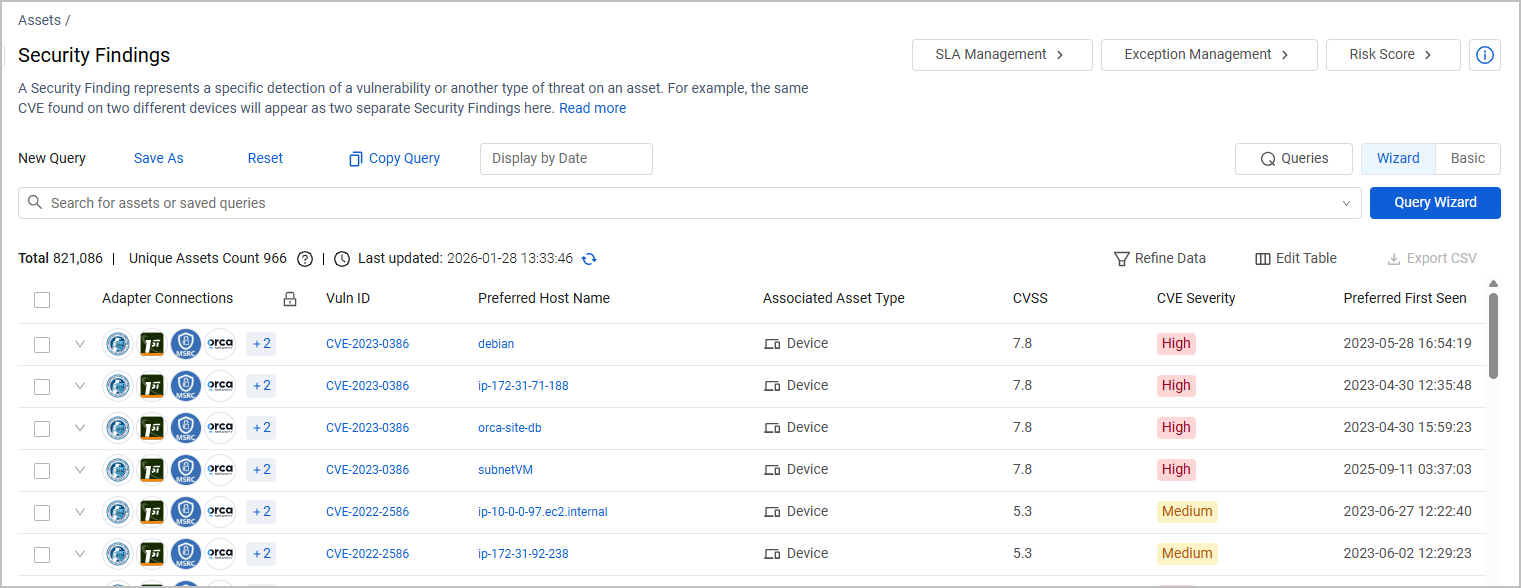
The fields on the Security Findings Assets table provide valuable information on the CVEs detected on your assets.
Note
All default and optional Security Findings fields, explained in the following sections, are also accessible from the Security Finding table in any asset's Profile Page. In this page, go to the left navigation menu, and under Tables, select Security Findings.
Default Fields
- Vuln ID - The identifier of the vulnerability, either the CVE ID number as provided by the NIST National Vulnerability Database (NVD), or a unique ID number provided by the adapter.
- Associated Asset Type - The asset type on which the vulnerability was detected: Device, Database, Compute Image, etc.
- CVSS - Common Vulnerability Scoring System (CVSS), a numeric score used to supply a qualitative measure of severity. The CVSS rating is fetched from the source (v2,0, v3.0, v4.0, etc.).
- CVE Severity - NONE, LOW, MEDIUM, HIGH, CRITICAL, UNTRIAGED, NEGLIGIBLE, INFO, MODERATE, SERIOUS, SEVERE, URGENT, or CRITICAL (based on the CVSS rating).
- Preferred Host Name - a clickable field that allows you to navigate to the Profile Page of the asset the vulnerability was detected on. Note that you can also use the Asset Unique ID or Associated Asset ID fields for the same information.
- Preferred First Seen - An aggregated date field that shows the earliest date that a Security Finding was seen on the asset. Generally, the date represents the first time this vulnerability was fetched, unless there is a date when it was first seen by an adapter.
- Preferred Last Seen - An aggregated date field that shows the latest date that a Security Finding was seen on the asset. The value of this field depends on the vulnerability's state - Open or Closed.
- For a Closed vulnerability, the Preferred Last Seen date is either the remediation time reported by the adapter, or, if no remediation time is reported, the last time it was fetched as an Open vulnerability.
- For an Open vulnerability, the Preferred Last Seen date is the last time it was fetched or reported by an adapter.
- Preferred Age (Days) - How many days ago the vulnerability was open. This value is calculated by one of the following methods:
- (Default) Deducting the Preferred First Seen date from the Preferred Last Seen date
- Deducting the Preferred First Seen date from the current day's date To select the method you want to use to calculate the value of Preferred Age (Days):
- Navigate to System Settings > Data > Security Findings Data.
- Under Preferred Age configuration, select a calculation method. Your selection applies across all adapters.
Note
The information in the Preferred First Seen, Preferred Last Seen and Preferred Age (Days) fields is provided to allow for MTTR (Mean Time to Remediate) and SLA metrics calculations.
- CVE Impact Score - An evaluation of the "damage level" that might occur if the vulnerability is exploited, according to NIST.
- CVE Exploitability Score - How likely it is that a vulnerability will be exploited according to NIST.
- Mitigated - Whether actions were taken to reduce or eliminate the risk associated with the vulnerability (Yes/No).
Additional Fields
The following fields are not default in the Security Findings table. You can add them by clicking Edit Table > Edit Columns.
- CVE Description - A description of the vulnerability.
- Associated Asset Tags - Any tags assigned to this asset from its Assets page are also displayed in the Security Findings table.
- Status - a field showing whether the vulnerability is Open or Closed. Note that this field can be populated with additional values fetched from the adapter.
Remediation Tracking Fields
Some vulnerability adapters do not report vulnerabilities after they were remediated. To address this issue and maintain accurate calculation of key metrics such as Time to Remediate (TTR) and SLA, Axonius offers a mechanism to identify when a vulnerability is no longer being reported, indicating potential remediation. This mechanism compares the reported vulnerabilities in the latest discovery cycle with those reported in the previous cycle. When a vulnerability is reported in the previous cycle but is absent from the latest cycle, it is considered potentially remediated. The following fields pertain to tracking and calculating remediation times:
Adapter Fields
- First Seen, Last Seen - The time when an adapter first or last detected the vulnerability.
- Status - whether the vulnerability is Open or Closed.
- Remediation Time - When the vulnerability was remediated according to information reported by an adapter.
Axonius Fields
- First Fetch Time, Last Fetch Time - The time when an adapter first or last reported the vulnerability to Axonius.
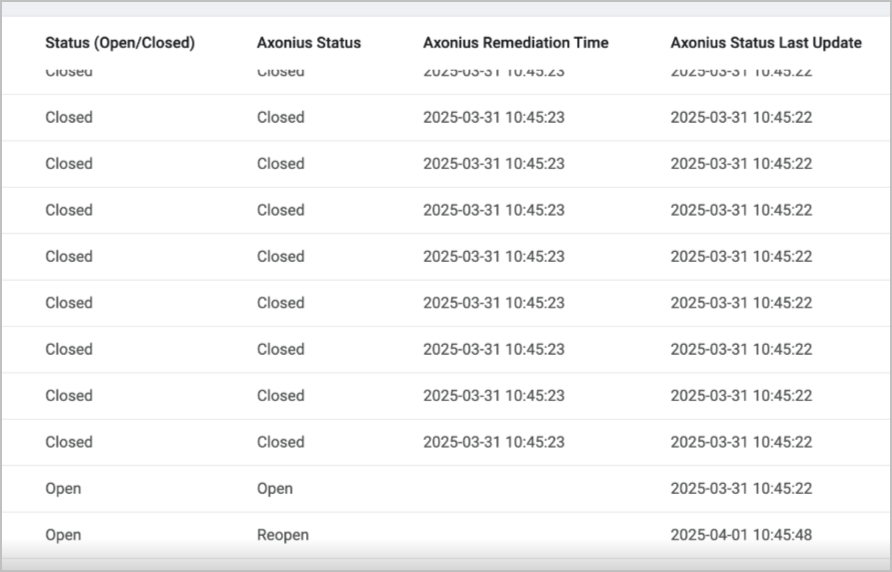
- Axonius Status - The vulnerability status: Open, Closed, or Reopen.
- A Closed status appears either when this vulnerability was reported closed by an adapter, or when it stopped being reported by an adapter.
- A Reopen status appears when the vulnerability was reported again by an adapter after a period of time when it was not reported. In this case, the First Fetch Time field value matches the date when it was re-opened. Note that this might also affect the Preferred Age field value.
- Axonius Status Last Update - When the Axonius Status field was last updated, reflecting the most recent status change.
- Axonius Remediation Time - When the status was changed from Open to Closed or from Reopen to Closed. This field is populated only when the Axonius Status field value is Closed.
Notes
The Axonius fields are populated by values from the adapter only if the adapter indeed reported this information. Otherwise, these values are generated by Axonius.
This logic does not apply to manually closed vulnerabilities.
Data Enrichments
Axonius uses a variety of sources to collect information on reported CVEs and other Security Findings, and enriches them with that information. The icon of the enrichment from which the vulnerabilities originate is displayed under the Adapter Connection column. See Vulnerability Enrichment for detailed information on the enrichment sources.
Security Findings Queries
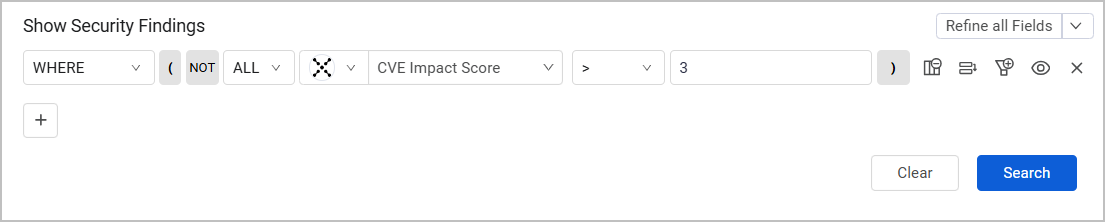
Use the Query Wizard to build queries on the Security Findings page. For example, you can build a simple query that shows only CVEs with a certain range of CVE Impact Score, as demonstrated here:
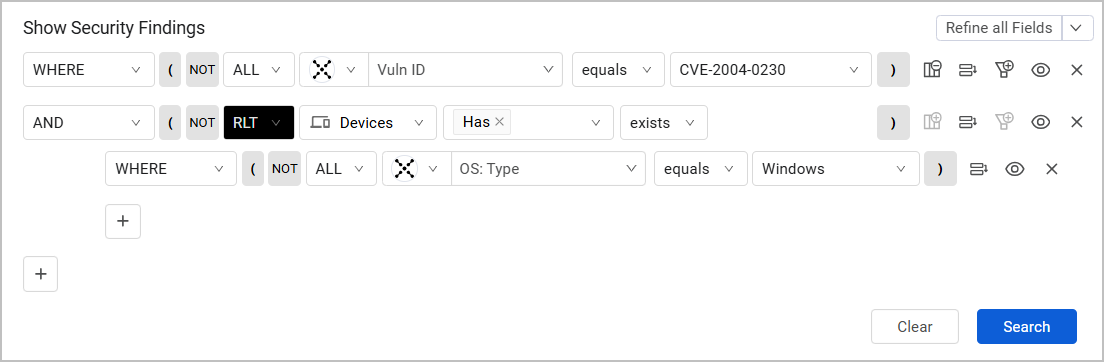
You can also use build relationship queries based on the relationship between a Security Finding and the asset it was detected on. In the following example, we want to show instances of a specific Vuln ID only on devices that have a Windows OS type:
Security Findings Profile Page
Click on a Security Finding row to view its Asset Profile page. The Security Finding Profile page provides detailed information about the Security Finding selected. The Security Finding Profile page is identical to the Asset Profile page with all of its relevant capabilities. Refer to Asset Profile Page to learn more.
Updated 6 days ago
