Vulnerability Enrichment
Axonius uses a variety of sources to collect information on reported CVEs and other Security Findings, and enriches them with that information.
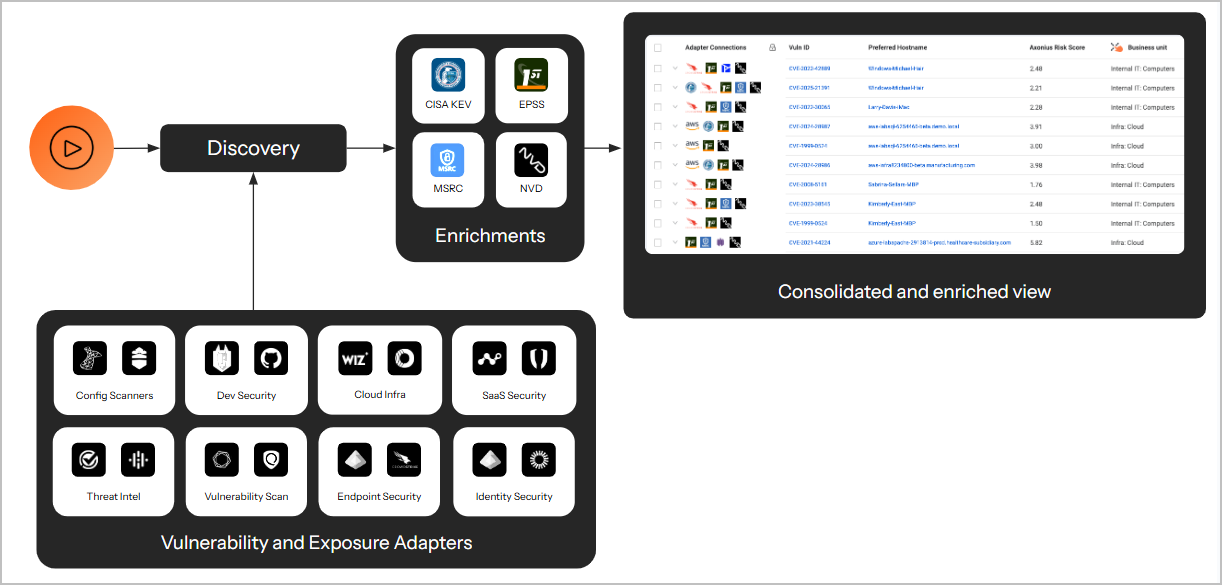
Below is the list of enrichment sources used by Axonius and their icons. When viewing a Security Finding on the relevant Assets page, the icon of the enrichment from which the vulnerabilities originate is displayed under the Adapter Connection column.
Out-of-the-Box Enrichment Sources
| Name and Icon | Indicates |
|---|---|
| NVD | Indicates Security Findings enriched with data from the NIST NVD database. |
| EPSS | Indicates software Security Findings enriched with details from the Exploit Prediction Scoring System EPSS from connected adapters. |
CISA  | Indicates Security Findings enriched with vulnerabilitiy information from your connected adapters with additional details from the CISA Known Exploited Vulnerabilities (KEV) Catalog. When relevant, the CISA fields and information are available for viewing and querying in the Security Findings and Devices modules. Only CVEs that are part of the CISA KEV Catalog will be enhanced. |
MSRC  | Indicates software Security Findings enriched with details from MSRC from connected adapters. |
EUVD | A platform that offers information on security vulnerabilities from the European Union Vulnerability Database. |
OSV (Open Source Vulnerabilities)  | A database to identify affected open-source packages, ecosystems, severity (when available), and references. |
Adapter Enrichments
Configure the following adapters in Axonius to enrich Security Finding assets with data fetched by them.
| Name and Icon | Indicates | |
|---|---|---|
VulnCheck | Indicates vulnerabilities enriched with data from the VulnCheck enrichment enforcement action. | |
Intel 471 Enrichment | Provides cyber threat intelligence to assess, identify, and manage potential risks. | |
Mandiant Enrichment | Offers threat intelligence, incident response, and security consulting services to detect and mitigate advanced cyber threats. | |
Bastazo | A security platform that offers comprehensive attack surface management solutions. | |
Qualys Cloud Platform | Qualys Cloud Platform monitors customers' global security and compliance posture using sensors. This adapter connects to the Qualys Cloud Platform service to import information about devices and vulnerabilities. | |
VulnDB Enrichment | VulnDB is a vulnerability intelligence platform that offers detailed information on software, hardware, and third-party library vulnerabilities to support risk assessment and remediation efforts. | |
Empirical Security Enrichment | Empirical Security provides vulnerability intelligence and exploitation activity data to enhance CVE analysis and prioritization. | |
GreyNoise  | GreyNoise collects, analyzes, and filters internet scan activity. |
Updated 2 days ago
