Google Cloud Platform (GCP)
Google Cloud Platform (GCP) is a suite of cloud computing services. Alongside a set of management tools, it provides a series of modular cloud services including computing, data storage, data analytics and machine learning.
Types of Assets Fetched
This adapter fetches the following types of assets, some may need to be selected as advanced options:
- Devices, Users, Software, SaaS Applications, Compute Services, Application Services, Networks, Load Balancers, Databases, Object Storage, Accounts/Tenants, Serverless Functions, Disks, Compute Images, Network/Firewall Rules, Application Resources
Related Enforcement Actions:
- GSuite - Add Users
- GSuite - Remove Users
- GSuite - Add Users to Group
- GCP - Add or Remove Tags to/from Assets
Parameters
-
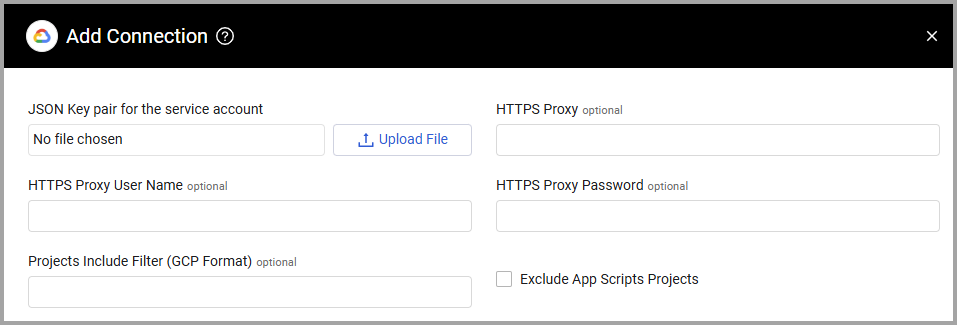
JSON Key pair for the service account (required) - A JSON-document containing service-account credentials to GCP. For details, see Connect Axonius to Google Cloud Platform.
-
HTTPS Proxy (optional) - A proxy to use when connecting to the GCP APIs.
-
HTTPS Proxy User Name (optional) - The user name to use when connecting to the value supplied in Host Name or IP Address via the value supplied in HTTPS Proxy.
-
HTTPS Proxy Password (optional) - The password to use when connecting to the server using the HTTPS Proxy.
-
Projects Include Filter (GCP Format) (optional) - Filter by projects accessible by the active account, as per the Gcloud Topic Filters.
-
Exclude App Scripts Projects - Select this option to exclude App Script projects from the projects data fetched by this adapter.
To learn more about common adapter connection parameters and buttons, see Adding a New Adapter Connection.
Advanced Settings
Note
Advanced settings can either apply to all connections for this adapter, or to a specific connection. Refer to Advanced Configuration for Adapters.
- Email domain include list (optional) - Enter a comma-separated list of email domains to include in the fetch. If left empty, all connections for this adapter will fetch all users unless the Email domain exclude list is populated.
- Email domain exclude list (optional) - Enter a comma-separated list of email domains to exclude from the fetch when the Email domain include list is empty.
- Fetch Google Cloud Clusters - Select this option to fetch Cluster devices and display them in the Devices page.
- Fetch Google Cloud SQL database instances - Fetch all Google Cloud SQL instances.
- If enabled, all connections for this adapter will fetch Google Cloud SQL database instances.
- If disabled, all connections for this adapter will not fetch Google Cloud SQL database instances.
Note
Fetching Google Cloud SQL database instances also requires the following:
- Fetch Google Cloud Routers - Select to fetch Google Cloud routers.
- Fetch Google Instance Groups - Select to fetch Google Instance Groups as Compute Services.
- Fetch Google Cloud VPCs - Select whether to fetch VPCs from Google Cloud as assets.
- Fetch Subnets as assets - Split subnets of a VPC network into individual assets.
- Fetch Google Cloud Storage buckets Select to fetch all Google Cloud Storage buckets.
- If enabled (default), all connections for this adapter will fetch the GCP Storage buckets.
- If disabled, all connections for this adapter will not fetch the GCP Storage buckets.
Note
Fetch all Google Cloud Storage buckets also requires the following:
- Google Cloud Storage JSON API
- Storage Object Viewer role
- Fetch Google Cloud Compute Images (Images, Snapshots and Templates) - Select whether to fetch all Google Cloud Compute Disk Images, Snapshots and Templates.
- Fetch Object metadata in Google Cloud Storage buckets (0: disabled, max supported: 1000) (optional, default: 0) - Fetch Object metadata in GCP Storage buckets that includes: name, size, and links to objects within each bucket.
- If supplied, all connections for this adapter will fetch 1000 objects or the specified number, the smallest of the two.
- If not supplied, all connections for this adapter will not fetch Object metadata in GCP Storage buckets.
Note
Fetch object metadata in GCP Storage buckets also requires the following:
- Google Cloud Storage JSON API
- Storage Object Viewer role
- Fetch IAM permissions for users - Fetch IAM permissions and associate those to the users roles. This includes permissions for build-in roles as well as Subscription-level and Project-level custom defined roles.
- If enabled (default), all connections for this adapter will fetch IAM permissions and will associate those to the users roles. These permissions will be represented as the Role Details complex field. This must be enabled to use the Axonius - Send Email to Assets action to send emails to GCE account administrators.
- If disabled, all connections for this adapter will not fetch IAM permissions.
Note
Fetch IAM permissions and associate those to the users roles requires the following:
- Role Viewer
- Only Fetch SCC Assets with associated SCC Findings - Select this option to only fetch SCC assets that have findings.
- Fetch organizational tags - Select this option to enrich VM instances with organizational tags or project tags associated with them.
- Fetch users (optional, default: true) - Unselect this option to exclude user data from the fetch.
- Security Command Center (SCC) Organizations (optional) - Specify a comma-separated list of organization IDs.
- If supplied, all connections for this adapter will fetch Security Command Center device assets and their associated vulnerabilities from the specified list of organization IDs.
- If not supplied, all connections for this adapter will not fetch any Security Command Center device assets.
Note
Fetch Security Command Center device assets and their associated vulnerabilities requires the following organization-level roles to each of the specified organizations:
Alternatively, Security Center Admin is required.
-
Fetch SCC findings from the last X days (0: disabled, max supported: 90) (optional, default: 90) - Specify the number of days SCC findings data is to be fetched.
- If supplied, all connections for this adapter will fetch SCC findings data gathered in the last number of days as specified.
- If not supplied, all connections for this adapter will fetch SCC findings data gathered in the last 90 days.
-
Custom filter expression for SCC findings (optional) - Specify an expression that defines the filter to apply across assets fetched from SCC.
- If supplied, all connections for this adapter will apply the specified filter when fetching SCC assets.
- If not supplied, all connections for this adapter will not apply any filter when fetching SCC assets.
-
Number of parallel connections (required, default: 20) - Specify the number of connections to be opened to control the performance of the data fetch.
-
Fetch only compute devices that are turned on - Select this option to not fetch compute devices that are turned on.
-
List of tags to parse as fields (optional, default: empty) - Specify a comma-separated list of tag keys to be parsed as device or user fields. Each tag is a key-value pair that is part of the Adapter Tags complex field.
- If supplied, all connections for this adapter will parse any of the listed tags that are associated with the fetched device or user as:
- Values of the Adapter Tags field.
- Designated field with the name of the tag key and the value of the tag value.
- If not supplied, all connections for this adapter will only parse all tags as values of the Adapter Tags field.
- If supplied, all connections for this adapter will parse any of the listed tags that are associated with the fetched device or user as:
-
Fetch Google Cloud Serverless Functions - Select this option to fetch Serverless Functions from the 'Cloud Functions' service using the Method: projects.locations.functions.list API.To fetch Google Cloud Serverless Functions the following permissions need to be granted:
- OAuth scope:
https://www.googleapis.com/auth/cloud-platform - IAM permission on the specified resource parent:
cloudfunctions.functions.list
- OAuth scope:
-
Fetch Google Cloud APIs - Select this option to fetch APIs from Apigee. To enable this, the following IAM permission on the specified resource parent is required:
apigee.proxies.list -
Fetch Google Cloud Run Services - Select this option to fetch Cloud Run Services and parse them as Compute Services.
-
Fetch Google Cloud Projects - Select this option to fetch Google Cloud Projects and parse them as Account/Tenants.
Note
For details on general advanced settings under the Adapter Configuration tab, see Adapter Advanced Settings.
Connect Axonius to Google Cloud Platform
To connect Axonius to Google Cloud Platform you need to:
- Enable cloud APIs
- Create a service account and grant permissions to that service account
1. Enable Cloud APIs
-
Navigate to the Google Cloud Console and select the project that you want Axonius to connect to.
-
Navigate to APIs & Services
>Dashboard..png)
-
Axonius requires the following APIs to be enabled:
| Enabled API Name | Required / Optional | Used for |
|---|---|---|
| Compute Engine API | Required | The adapter to fetch assets data from Google Cloud Platform. |
| Cloud Resource Manager API | Required | The adapter to fetch assets data from Google Cloud Platform. |
| Container Artifact API | Required | https://container.googleapis.com |
| Identity and Access Management (IAM) API | Required | https://iam.googleapis.com |
| Security Command Center API | Required | https://securitycenter.googleapis.com |
| Google Cloud Storage JSON API | Optional | Adapter advanced settings: Fetch Google Cloud Storage buckets - Fetch all Google Cloud Storage buckets. Fetch Object metadata in Google Cloud Storage buckets - Fetch Object metadata in GCP Storage buckets. |
| Cloud SQL Admin API | Optional | Adapter advanced settings: Fetch Google Cloud SQL database instances - Fetch all Google Cloud SQL instances. |
For example, in the screenshot below you can see that since the Cloud Resource Manager API doesn't appear in the list, it isn't enabled and needs to be enabled.
.png)
To enable an API, click Enable APIs and Services at the top of the page.
-
Search for the API you want to enable and select it. For example: Cloud Resource Manager API
.png)
-
Click Enable.
.png)
2. Create a Service Account and Grant Permissions to that Service Account
-
Navigate to the Google Cloud Console and select the project that you want Axonius to connect to.
-
Select IAM & admin
>Service accounts..png)
-
Click Create a Service Account.
.png)
- Provide a name and description for the service account, then click Create. If you already clicked Done, skip to Step 8.
.png)
- In the Grant this service account access to a project section, give the service account the roles listed below, as well as the "Security Reviewer" role.
| Role Name | Required / Optional | Used for |
|---|---|---|
| Compute Viewer | Required | Grants read-only access to Axonius to fetch assets. |
| Kubernetes Engine Viewer | Required | Grants read-only access to Axonius to fetch assets. |
| Storage Object Viewer | Optional | Adapter advanced settings: • Fetch Google Cloud Storage buckets - Fetch all Google Cloud Storage buckets.• Fetch Object metadata in Google Cloud Storage buckets - Fetch Object metadata in GCP Storage buckets. |
| Cloud SQL Viewer | Optional | Adapter advanced settings: • Fetch Google Cloud SQL database instances - Fetch all Google Cloud SQL instances. |
| IAM: Role Viewer | Optional | Adapter advanced settings:• Fetch IAM permissions for users - Fetch IAM permissions and associate those to the users roles. |
| Security Reviewer | Required | Provides permissions to list all resources and allow policies on them. |
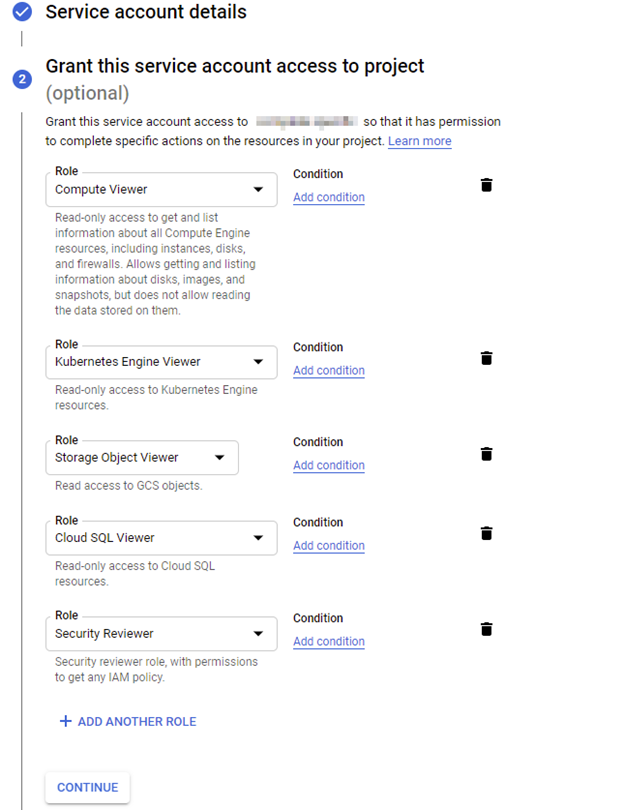
- Skip the Grant users access to this service account step.
- Click Done.
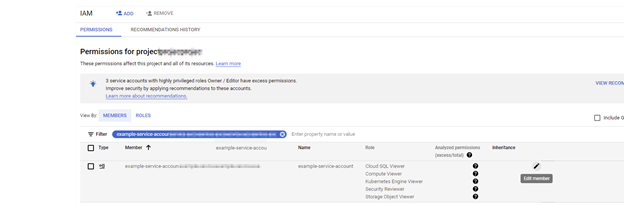
- To modify, or review the permissions granted to this service account in any project or at the organization level, go to IAM, find the service account you've created and click Edit Permissions.
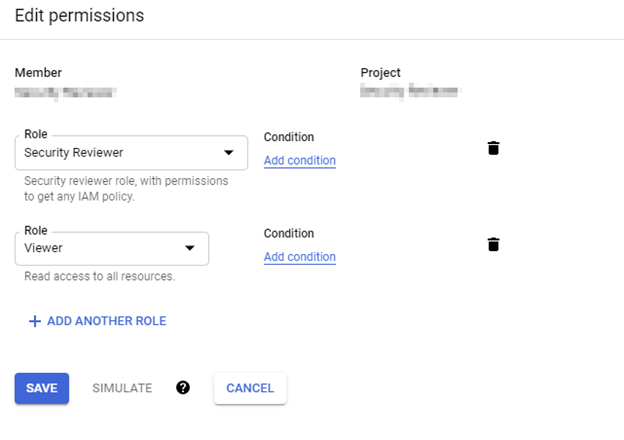
-
In the Service Account just created, go to Keys
-
Click Add key and then Create.
.png)
-
Your JSON key is subsequently downloaded. Finish creating the account and go back to the Service Accounts page. Copy the email address of the new service account.
-
In the top part of the page, select the organization resource, and go to IAM & Admin - IAM.
- Click Add and use the service account email to add the new service account as a new member of the organization.
- Click + Add Another role to add the following roles to added member:
| Role Name | Required / Optional | Used for |
|---|---|---|
| Compute Viewer | Required | Grants read-only access to Axonius to fetch assets. |
| Kubernetes Engine Viewer | Required | Grants read-only access to Axonius to fetch assets. |
| Storage Object Viewer | Optional | Adapter advanced settings: • Fetch Google Cloud Storage buckets - Fetch all Google Cloud Storage buckets. • Fetch Object metadata in Google Cloud Storage buckets - Fetch Object metadata in GCP Storage buckets. |
| Cloud SQL Viewer | Optional | Adapter advanced settings: • Fetch Google Cloud SQL database instances - Fetch all Google Cloud SQL instances. |
| IAM: Role Viewer | Optional | Adapter advanced settings:• Fetch IAM permissions for users - Fetch IAM permissions and associate those to the users roles. |
| • Security Center Findings Viewer role• Security Center Assets Viewer role(Or alternatively, Security Center Admin) | Optional | Adapter advanced settings:• Security Command Center organizations - Fetch Security Command Center device assets and their associated vulnerabilities from a specified list of organizations (NOTE: Those organization-level roles are required for each of the specified organizations.) |
.png)
Note
Additional permissions are required for GCP Enforcement Actions.
- Click Save.
Updated about 2 months ago
