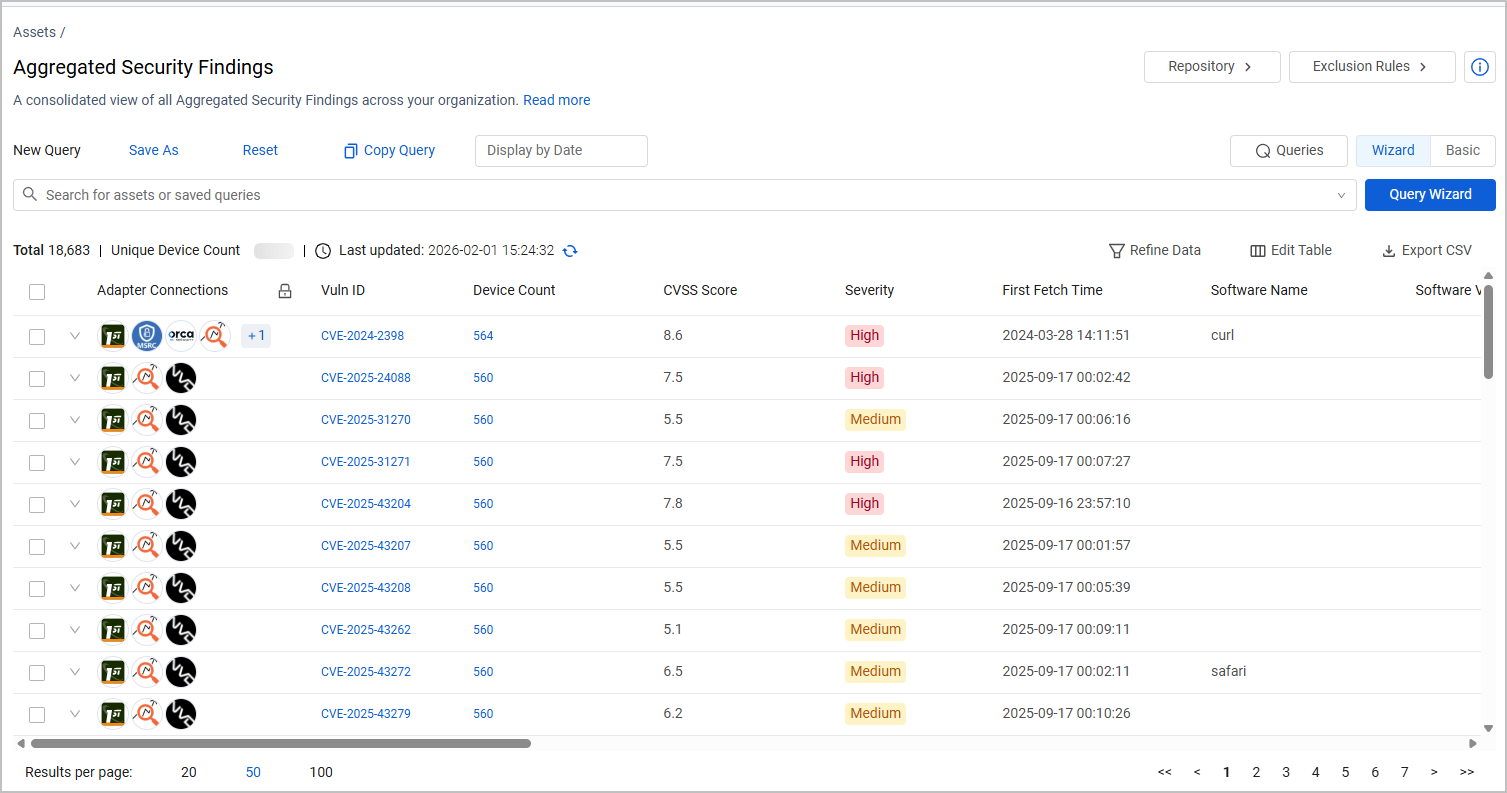
Aggregated Security Findings Page
Explore the Aggregated Security Findings page for a comprehensive view of cybersecurity vulnerabilities, enabling prioritization based on asset criticality and potential impact.
Use Aggregated Security Findings to see a consolidated view of all the vulnerabilities in your organization from all sources. The Aggregated Security Findings page delivers increased visibility into cybersecurity vulnerabilities and risks. It helps security, IT, and risk teams identify vulnerabilities across fleets of assets, enabling them to prioritize vulnerabilities based on asset criticality, potential impact, and recognized threats.
A vulnerability is a software defect that could allow hackers to gain control of a system. Axonius presents vulnerabilities as defined by the Common Vulnerabilities and Exposures (CVE) list. Axonius discovers vulnerabilities by extracting CVE information fetched from adapters.
Note
Some adapters, such as Tenable.sc, require selecting the Fetch Vulnerabilities advanced setting before viewing their vulnerability information on the Aggregated Security Findings page.
To access the page, from the Assets menu, expand Exposures and select Aggregated Security Findings.
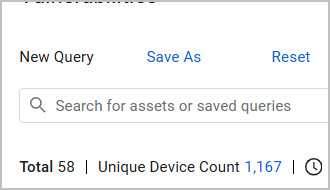
The total number of unique devices on which vulnerabilities were found is shown above the Aggregated Security Findings table. Click on the number of devices to open the devices on which vulnerabilities were found on the Devices page.
Aggregated Security Findings Fields
Fields displayed on the Aggregated Security Findings page include:
-
Adapter Connections - shows the icons of the adapter connections or enrichment from which the Aggregated Security Findings originate.
-
Vuln ID - The identifier of the vulnerability. This can be either a CVE ID or a different vulnerability identifier provided by some adapters.
-
When the value is a CVE ID, it contains is a clickable link to the CVE details in the NIST National Vulnerability Database (NVD).
-
When the vulnerability identifier isn't a CVE type but is fetched from an adapter, such as from a Tenable adapter, the vulnerability ID appears without a CVE prefix. When a link is available for a specific vulnerability identifier, you can click it to learn more about the vulnerability and how to remediate it.
Note
For supported adapters that fetch "non-CVE" vulnerability identifier information:
-
A prefix of the adapter appears before the value displayed in the Vuln ID column.
-
An optional Is CVE column displays ‘No’ for non-CVE vulnerabilities and ‘Yes’ for CVE vulnerabilities.
-
-
-
Device Count - The Device Count shows the number of devices affected by this specific vulnerability. Click a Device Count to open the Devices page with the devices affected by this vulnerability. Devices present Total CVE Count by Severity. CVEs are only counted if the CVE was validated on NVD.
-
Software Name and Software Vendor - When a CVE is applicable for multiple software, these fields are populated as "Multiple Software" and "Multiple Vendors".
-
NVD published date - The date the vulnerability was added to the NVD database.
-
NVD Modified date - The date the vulnerability was modified.
-
CVSS -Common Vulnerability Scoring System (CVSS), a numeric score used to supply a qualitative measure of severity. The CVSS rating is fetched from the source (v2,0, v3.0, v4.0, etc.).
-
CVE Exploitability Score - How likely it is that a vulnerability will be exploited according to NIST.
-
EPSS Score - How likely it is that a software vulnerability will be exploited in the wild according to EPSS.
-
CVE severity -NONE, LOW, MEDIUM, HIGH, CRITICAL, UNTRIAGED, NEGLIGIBLE, INFO, MODERATE, SERIOUS, SEVERE, URGENT, or CRITICAL value which are based on the CVSS rating.
-
CVE description, Synopsis, and Reference
-
First Seen, Last Seen - The time when an adapter first or last detected the vulnerability.
Not all available fields are displayed by default. Use Edit Columns to add or remove columns. See Setting Page Columns Display for more information.
You can add the CWE ID column to view corresponding vulnerabilities appearing in the Common Weakness Enumeration (CWE) list. Click a specific CWE ID link to learn more about the vulnerability and how to remediate it.
Data Enrichments
Axonius uses a variety of sources to collect information on reported CVEs and other Security Findings, and enriches them with that information. The icon of the enrichment from which the vulnerabilities originate is displayed under the Adapter Connection column. See Vulnerability Enrichment for detailed information on the enrichment sources.
CVE Vector Information
To view CVE Vector information add these columns to the Aggregated Security Findings page. See Setting Page Columns Display for more information.
The following fields are available:
| Vector | Available in CVSS Version | Notes |
|---|---|---|
| CVE Vector: Access Complexity | 2.X | Describes whether the access complexity is low, medium, or high |
| CVE Vector: Access Vector | 2.X | Describes whether the Access Vector is local or on a network |
| CVE Vector: Attack Complexity | 3.X | |
| CVE Vector: Attack Vector | 3.X | |
| CVE Vector: Authentication | 2.0 | Returns None if no CVE Vector Authentication exists |
| CVE Vector: Availability | ||
| CVE Vector: Confidentiality | ||
| CVE Vector: Integrity | ||
| CVE Vector: Privileges Required | 3.X | Reports whether privileges or required, and what level, if known |
| CVE Vector: Scope | 3.X | |
| CVE Vector: User Interaction | 3.X | |
| CVE Vector: Version | 3.1, 3.0, 2.0 |
Creating Queries on Aggregated Security Findings
Use Queries on the Aggregated Security Findings page to create a unique set of queries. Create queries using either of the following modes:
-
Query Wizard (the default) - Create a query using the Query Wizard, or in the query bar, selecting a saved query or writing a query.
-
Basic mode - Create a query by selecting filters. Learn more and how to create Queries in Basic mode.
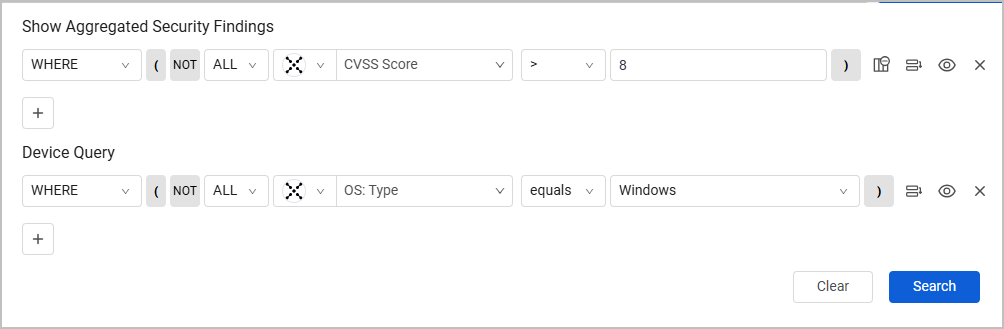
Aggregated Security Finding queries with the Query Wizard are created on two levels:
- The first level of the query focuses on vulnerability parameters: fields such as the CVSS score, severity, or attack vector.
- The second level queries devices, such as operating system, installed software, or the last update date. Use these queries to find out which critical vulnerabilities exist and whether they impact critical assets in your environment; or, how many vulnerabilities exist, and whether they appear on devices with open ports/a specific patch applied.
After running the query, the table shows the vulnerabilities queried, filtered by the devices they affect. For example, this query shows vulnerabilities with the CVSS score over 8, only on devices where the operating system is Windows:
Note
While it's recommended to get more context for the results, you don't have to fill in the Device section of the query to find vulnerabilities in your environment.
To learn more on Axonius queries, see Working with the Query Wizard and Saved Queries.
Refining the Device Count Displayed from Device-based Fields in Aggregated Security Findings
It can be very useful to refine the device count displayed for device connected fields in Aggregated Security Findings. For example, in this query:
- Build a query on an Aggregated Security Finding field on the table, such as CVSS Severity is High.
- Filter the findings displayed by a Device query to show the Aggregated Security Finding in your environment by a defined Device query, such as Windows Devices.
- After running the query, the table shows the Aggregated Security Findings queried, filtered by the devices they affect.
Once you get results for a query like this, to further refine the device count for such a query, use the Data Refinement field on the Device Count column for unique Aggregated Security Findings fields that are found on devices. For example: there might be 50 devices with CVSS Severity is High, and 20 with Mitigated Yes (and 30 with Mitigated no). To display the number of devices where both Mitigated Yes matches those exact devices who also have CVSS Severity is High, perform the following data refinement:
-
Click the Refine Data (filter) icon next to the Device Count column.
-
From the Refine Data dialog, under Device related asset entities - refine by condition, the Security Finding complex object field is pre-selected on the first row. From second row select the device-related Aggregated Security Finding field that you want to filter by and click Done.
For example, select Mitigated yes to display the exact number of devices where the selected Aggregated Security Finding on them has a mitigated field with yes.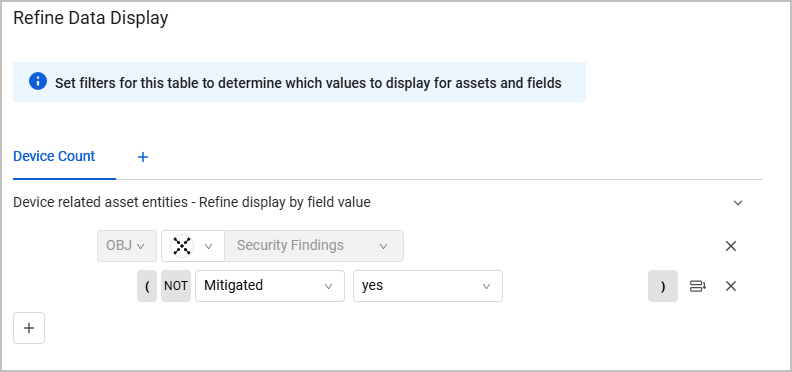
The Aggregated Security Findings page now shows the device count that matches the number of devices on which the vulnerabilities were found. If the device count is zero the row is hidden. Click on the Device Count to open these devices on the Devices page.
You can also refine the data displayed on the Aggregated Security Findings page in additional ways.
Additional Actions on the Aggregated Security Findings page
From Aggregated Security Findings page you can perform the following actions on the data:
And more actions as detailed in the Asset Actions page.
Managing Exclusions
You can manage exclusions from the Aggregated Security Findings page.
To add an Aggregated Security Finding to a rule, hover over a row and click the Exclude button, or select one or more items and then click Exclude. The Create Exclusion Rule dialog opens with the Aggregated Security Finding(s) you selected filled in.
Learn more about creating Vulnerabilities Exclusion Rules.
Using Aggregated Security Findings Queries in Enforcement Actions
The following Enforcement Center Actions can be used with Aggregated Security Findings queries:
- Axonius - Push System Notification
- Axonius - Send Email
- Email - Send per Asset
- Axonius - Add Custom Data to Assets
- Axonius - Remove Custom Data from Assets
- Manage Custom Enrichment - Enrich assets with CSV file
- Axonius - Add Tag
- Axonius - Remove Tag
- Axonius - Calculate Risk Score
- Cherwell - Create Incident
- Cherwell - Create Incident per Asset
- Freshservice - Create Ticket
- Freshservice - Create Ticket per Asset
- Ivanti Security Controls - Patch Group
- Jira - Create Issue
- Jira - Create Issue per Asset
- Jira Service Management - Create Issue
- Jira Service Management - Create Issue per Asset
- Jira Service Management - Create Ticket
- Jira Service Management - Create Ticket per Asset
- Jira Service Management - Update Tickets
- ServiceNow - Create Incident
- ServiceNow - Create Incident per Asset
For more details on creating and working with Enforcement Actions, see Creating Enforcement Sets.
Updated 2 days ago
