Axonius Release Notes 7.0.11
Release Date: October 5th 2025
These Release Notes contain new features and enhancements added in version 7.0.11.
Cyber Assets New Features and Enhancements
The following new features and enhancements were added to Axonius Cyber Assets:
Devices New Features and Enhancements
The following new features and enhancements were added to Devices .
Location Tab
A Location Tab was added to the Asset Profile page of Devices and its subset asset types (e.g., Network Devices). This tab displays a building map with the device’s position marked, along with details such as device name, floor, and more. This tab appears only when location data is available.
Exposures New Features and Enhancements
The following new features and enhancements were added to Exposures:
Risk Score Levels
When creating a new Risk Score, users can now define specific Risk Score ranges as Risk Levels. A Risk Level is a translation of a Risk Score's numeric value into one of the following strings: Low, Medium, High, or Critical. For example, Axonius' default settings are that Risk Scores between 0.01 and 3.99 are Low level; Risk Scores between 4 and 6.99 are Medium level; and so on. Users can edit these default ranges to fit their security needs.
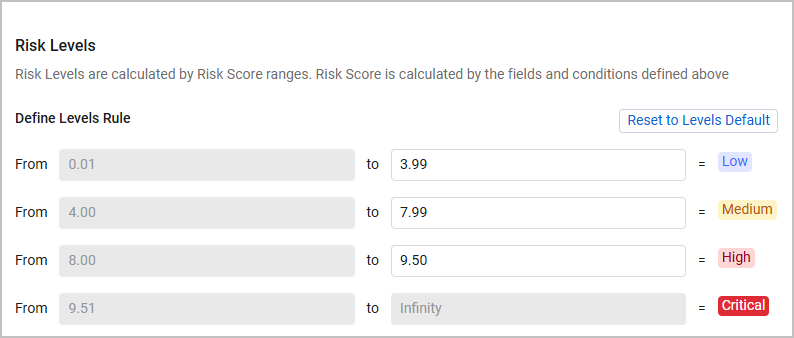
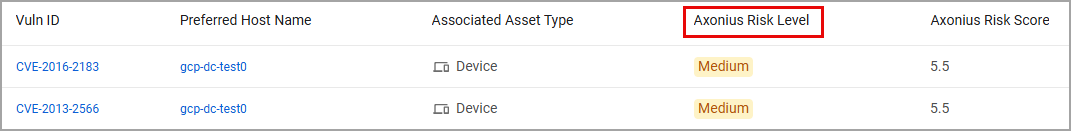
In addition, a new field called Axonius Risk Level was added to each Assets page, representing the Risk Level calculated for each asset. This field can be used in queries and dashboards, and helps users understand the correlation between an asset's numeric Risk Score and its Risk Level.
Axonius Platform New Features and Enhancements
Workflows
Query Node
The powerful Query node was introduced to Workflows, enabling users to fetch and use dynamic data directly from their Axonius environment. This feature is essential for building automations that require real-time lookups and conditional checks on asset data. Users can now configure the Query node with one or more custom or saved queries. Assets retrieved from all queries are combined (with Or logic) to create a single list for subsequent actions. The node executes the queries as soon as the workflow reaches it, ensuring the asset list is based on the most current synced data. This ensures that your automations can efficiently handle a wide range of scenarios and always act with the highest precision.
Enhanced Generic Webhook Event
Generic Webhook Events can now be configured to ingest and utilize complex and nested payloads. This includes support for fields of all types (nested JSON objects and arrays) and multiple nesting layers. This enhancement allows Axonius Workflows to handle complex data structures sent by external systems.
Enhanced Event and Action Conditions
-
It is now possible to configure both Event Conditions and Action Conditions to trigger based on data output from any previous Workflow node stored in the Workflow Data repository.
-
When setting up an Event Condition based on the incoming Event criteria, a fuller set of operators is now available for comparison of Event field values.
Case Sets
Edit Queries
It is now possible to modify the asset query for a saved Case Set. This new capability allows fine-tuning the scope of an ongoing Case Set without having to create a new one. The Query Preview updates immediately to reflect the count and composition of the new asset criteria.
System Settings New Features and Enhancements
The following updates were made to various System settings:
Enhanced Logging Capabilities
Two enhancements were introduced in the Activity Logs Settings (accessible from System Settings > System > Activity Logs) to strengthen auditing and visibility:
-
Enhanced API Logging for Syslog - A new Add API GET activities to Syslog option now logs all API GET activities (previously excluded from both the internal Activity Log and external Syslog) to a Syslog external system. This provides complete visibility and auditing of all API interactions with the platform.
-
Enhanced Activity Log Auditing - When the existing Add activity logs for access (read) activity option is enabled, the Activity Log now records View Activity Log actions. This means every time a user opens the log, that event is recorded, ensuring a complete and auditable record of who accessed the logs and when.
Adapter and Enforcement Action Updates
New Adapters
The following new adapters were added:
- Atomicwork
- Atomicwork is an agentic ITSM and ESM platform that provides AI-driven automation, incident and asset management, and knowledge integration across service workflows. (Fetches: Users, Groups)
- mPro3
- mPro3 is a web-based maintenance management solution that offers equipment and area management with inspection, repair tracking, and paperless workflow features. (Fetches: Devices)
- Oligo
- Oligo is a runtime application security platform that provides protection against vulnerabilities in open-source code. (Fetches: Vulnerabilities, SaaS Applications, Compute Images)
- PATCH MANAGER
- PATCH MANAGER is a network infrastructure management tool that provides graphical planning, documentation, and control of physical connectivity and asset information. (Fetches: Devices)
- Tripwire IP360
- Tripwire IP360 is a vulnerability management solution that provides comprehensive asset discovery, risk-based vulnerability assessment, and integration with security systems to prioritize remediation efforts. (Fetches: Devices, Vulnerabilities, Users, SaaS Applications, Networks)
- Xage
- Xage is a platform that provides identity-based access control, zero trust remote access, and microsegmentation for IT, OT, and cloud assets. (Fetches: Devices, Users)
Adapter Updates
The following adapters were updated:
-
Alibaba Cloud - 'Use HTTPS' was added to connection parameters.
-
Amazon Web Services (AWS) - Added an option to fetch Critical findings from Inspector.
-
BeyondTrust PRA Cloud - Added the option to enrich users with the Jump Group Users endpoint.
-
Bishop Fox - Added support for API v5.
-
BloodHound - Added the option to fetch computer admin and RDP users.
-
Check Point Multi-Domain Security Management (MDSM) - Added a Multi-Checkpoint Domain connection parameter to the adapter's configuration.
-
Cisco Catalyst Center (formerly Cisco DNA Center) - Added an option to fetch network maps marking the location of Network Devices.
-
- This adapter now fetches SaaS Applications, Domains & URLs, Organizational Units, and Networks as assets.
- Added the option to fetch various asset types and sub-types from different endpoints.
- Added the option to identify deleted users by the Label field.
- Added the option to fetch user information from the Raw Label field.
-
Google Security Operations SIEM - The name of the 'Google Chronicle Security' adapter was changed to Google Security Operations SIEM.
-
Google Security Operations SOAR - The name of the 'Google Chronicle SOAR' adapter was changed to Google Security Operations SOAR.
-
HPE Aruba Networking Management Software (AirWave) - Added an option to fetch network maps marking the location of access points.
-
- Added the option to fetch URLs from the Org Assets endpoint.
- Added the option to fetch application services from the Cloud Assets endpoint.
-
Ironclad Contract Lifecycle Management - Added support for OAuth2 authentication.
-
LogRhythm - Added the option to avoid parsing the asset name if it contains a valid IP address.
-
- Added the option to fetch devices from the Devices endpoint.
- Added the option to fetch incidents from the List Incidents endpoint.
-
Nozomi Guardian and CMC - Added the option to enter a custom query to fetch assets, overriding the default query.
-
Orca Cloud Visibility Platform - The Axonius adapter has been updated to support the latest Orca API. As the Legacy Orca API is being deprecated, all users of the Orca Adapter are advised to upgrade to the current Axonius version (7.0.11) to ensure continued functionality.
-
Palo Alto Networks Panorama - Added the option to fetch HIP match logs as well as the capability to select the dates from which you want the data to be retrieved.
-
Palo Alto Networks Prisma Cloud Workload Protection
- This adapter now fetches Compute Images as assets.
- Added the option to fetch image information for containers.
-
Panorays - API RateLimit Window was added to the connection parameters.
-
Qualys Container Security - This adapter no longer fetches Devices; it only fetches Containers.
-
Qualys WAS - This adapter now fetches Domains and URLs as assets.
-
Rubrik Security Cloud - This adapter now fetches File Systems, Accounts/Tenants, and Application Resources as assets.
-
SailPoint IdentityNow - Added several options to filter the accounts fetched by the adapter to improve fetch time.
-
ServiceNow - Groups and User Groups assets are fetched for users who have the Axonius Cyber Asset Product and not only for users who have the SaaS Applications product
-
Slack - Added two new connection parameters:
- Team IDs - A list of IDs of specific teams to fetch data from.
- Not an Admin Token - If the Authentication Token used to connect the adapter is not an admin token, Team IDs must be provided.
-
SQL Server - This adapter now fetches Networks as assets.
-
- This adapter now fetches Alerts/Findings as assets.
- Added the option to fetch AlertFindings from the Alerts endpoint.
-
Tenable Vulnerability Management - Added the option to fetch Secure Boot Status.
-
Trend Micro Vision One - Added the option to enrich devices with installed software.
-
Wiz - Added the option to enrich assets with Authentication Configuration.
New Enforcement Actions
The following Enforcement Actions were added:
- Absolute - Freeze Devices - Freezes devices in Absolute.
- Absolute - Unfreeze Devices - Unfreezes devices in Absolute.
- Asana - Create Ticket - Creates a task ticket in Asana.
- ManageEngine Endpoint (Desktop) Central and Patch Manager Plus - Create Software Action per Asset - Creates one configuration for all assets.
- Qualys - Add Tags to User - Adds tags to or removes tags from a user in Qualys.
- Qualys - Assign Role to User - Adds roles to or removes roles from a user in Qualys.
- Splunk - Delete User - Removes a user in Splunk.
Updated Enforcement Actions
The following Enforcement Actions were updated:
- Salesforce - Create Case - Added the option to attach a CSV data file to the created case.
- Tenable Vulnerability Management - Add IP Addresses to Scan - Added the option to override or delete the current IP address list.
